

The Sleuth Kit (TSK) & Autopsy: Open Source Digital Forensics Tools. List of digital forensics tools. During the 1980s, most digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools.
In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. Welcome to the Digital Forensics Association - Open Source Tools. Free & open Source digital forensics software. Top 20 Free Digital Forensic Investigation Tools for SysAdmins. Digital forensics tools come in many categories, so the exact choice of tool depends on where and how you want to use it. Here are some broad categories to give you an idea of the variety that comes under the umbrella of digital forensics tools: Database forensicsEmail analysisAudio/video forensicsInternet browsing analysisNetwork forensicsMemory forensicsFile analysisDisk and data captureComputer forensicsDigital image forensics While this is not an exhaustive list, it gives you a picture of what constitutes digital forensics tools and what you can do with them.
Sometimes multiple tools are packaged together into a single toolkit to help you tap into the potential of related tools. Also, it is important to note that these categories can get blurred at times depending on the skill set of the staff, the lab conditions, availability of equipment, existing laws, and contractual obligations. Choosing the right tool Skill level Output Cost Focus Additional accessories. iForensics - ...living Digital Forensics, eDiscovery and Information Governance. Digital Forensics. Digital Forensics. Using Microsoft Network Monitor 3.3. The only way to gain an idea of what a network conversation is all about is to expand the node in the tree and take a look at who is talking to whom and what sort of conversation is going on.
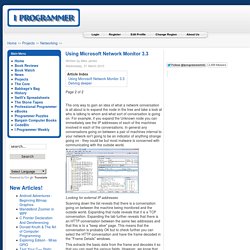
For example, if you expand the Unknown node you can immediately see the IP addresses of each of the machines involved in each of the conversations. In general any conversations going on between a pair of machines internal to your network isn't going to be an indicator of anything strange going on - they could be but most malware is concerned with communicating with the outside world. Looking for external IP addresses Scanning down the list reveals that there is a conversation going on between the machine being monitored and the outside world. Expanding that node reveals that it is a TCP conversation. This extracts the basic data from the frame and decodes it so that you can read the various fields.
Decode the data in the frame Now you have seen some of the basic capabilities of the network monitor. Computer Forensics - Free Computer Forensics Software Download. 3 Ways to View or Display Unicode and Special Characters. Have you ever noticed that when visiting some websites, sometimes you will see various characters dotted around the screen which don’t quite look as if they’re meant to be there?
You might see question marks and boxes when you think there’s supposed to be some sort of special characters or text displayed. This problem is quite a common one, especially so for new Windows installs or ones that don’t have Microsoft Office or supplemental languages installed. This problem is due to the fact that the default fonts and encoding in use by your browser are not capable of showing the special character or glyph which the webpage is trying to display. If it can’t show what it’s supposed to show, the browser will simply display a question mark or sometimes a small box instead to represent an unrecognized character.
As a simple demonstration, look at the pictures below. Notice the box either side of “Stars”. How To Remove Carpet Glue From Concrete Flooring. 20 of the best free tools that will help you conduct a digital forensic investigation. Decrypt encrypted packets using cryptcat. Download the challenge file from here.
Given a pcap file and we were asked to submit the hash of the encrypted file after reconstructing it. The challenge title will help you to get started. First I tried to learn the differences between netcat and cryptcat tools. Netcat is an opensource application which can read and write files to the network. Network Forensics. 21 Popular Computer Forensics Tools. Computer forensics is a very important branch of computer science in relation to computer and Internet related crimes.
Earlier, computers were only used to produce data but now it has expanded to all devices related to digital data. The goal of Computer forensics is to perform crime investigations by using evidence from digital data to find who was the responsible for that particular crime. For better research and investigation, developers have created many computer forensics tools. Police departments and investigation agencies select the tools based on various factors including budget and available experts on the team. Tools:Network Forensics. E-Detective Burst Expensive IP geolocation service. chkrootkit cryptcat Enterasys Dragon Instrusion Detection System, includes session reconstruction. ipfix/netflow v5/9 MNIS Collector is an IPFIX collector which also supports legacy Netflow.
Top 20 Free Digital Forensic Investigation Tools for SysAdmins. Large List of Free Forensic Software. While I personally have never gotten into forensics due to liability reasons, it has always been something that has interested me.
Recently, one of our forum members (mm201) posted an amazing resource with a large collection of free forensics tools for Windows, Mac and Linux as well as iOS, Android & Blackberry devices. If you are already doing forensics work or simply have an interest in it, be sure to check out this site: The tools on the site are divided into the following categories: Windows Systems and Artifacts in Digital Forensics, Part I: Registry.
Introduction Learning about artifacts in Windows is crucial for digital forensics examiners, as Windows accounts for most of the traffic in the world (91.8 of traffic comes from computers using Windows as their operating system as of 2013) and examiners will most likely encounter Windows and will have to collect evidence from it in almost all cyber-crime cases.
Below, we will discuss several places from which evidence may be gathered and ways to collect information from Windows. Windows actually provides a great abundance of artifacts and being aware of these artifacts is helpful not only for examiners but for companies and individuals (just to name a few reasons) trying to permanently and irrevocably erase sensitive information or perform informal investigations. The things you will find in this article. Forensic Analysis of the Windows Registry. Page: 1/16 Lih Wern Wong School of Computer and Information Science, Edith Cowan University lihwern@yahoo.com Abstract Windows registry contains lots of information that are of potential evidential value or helpful in aiding forensic examiners on other aspects of forensic analysis.
This paper discusses the basics of Windows XP registry and its structure, data hiding techniques in registry, and analysis on potential Windows XP registry entries that are of forensic values. Keywords: Windows registry, forensic analysis, data hiding Windows 9x/ME, Windows CE, Windows NT/2000/XP/2003 store configuration data in registry. 10 Data Recovery Tools You Can Download For Free [Windows]
It happens to the best of us.
![10 Data Recovery Tools You Can Download For Free [Windows]](http://cdn.pearltrees.com/s/pic/th/recovery-download-windows-87252802)
We are working on that very important file when suddenly disaster strikes. It accidently gets deleted, corrupted, the computer died or a number of unfortunate things that prevent you from gaining access to the file. What’s worse, you don’t have a backup and are in desperate need of those important files urgently.
Well, don’t fret as it is possible to recover those deleted files. When you delete a file, you don’t actually ‘delete’ it. SIFT Kit/Workstation: Investigative Forensic Toolkit Download. SANS Investigative Forensic Toolkit (SIFT) Workstation Version 3.0 Download SIFT Workstation VMware Appliance Now - 1.5 GB Having trouble downloading? If you are having trouble downloading the SIFT Kit please contact sift-support@sans.org and include the URL you were given, your IP address, browser type, and if you are using a proxy of any kind.
Having trouble with SIFT 3? If you are experiencing errors in SIFT 3 itself, please submit errors, bugs, and recommended updates here: Beta.techradar. The super-sleuth detectives in TV show CSI have some very nifty tools to help solve crimes. But the need to keep things interesting and wrap the show up in an hour means the technology used in each episode bears little resemblance to the work of real forensic experts. Or does it? When it comes to computer forensics, today's tools are becoming more advanced, leaving fewer places to hide information. This tension between fact and fiction took on a whole new dimension when Microsoft's police-only forensic toolkit was leaked on the internet. Reports say that it has more in common with CSI than The Bill.
Digital Forensics Links. This is a growing list of [digital/cyber/computational] forensic related resources. I agree, some serious reorganization is required. Please send any additions, corrections and/or dead-links to kulesh@cis.poly.edu I am now at Digital Assembly. Cyber Forensics Tools. 21 Popular Computer Forensics Tools. Digital Forensics Software. Our Recommended Six Mobile Forensics Tools. Mobile Internal Acquisition Tool. HTC Fuze Forensics Colby Lahaie The Senator Patrick Leahy Center for Digital Investigation Introduction Overview Many people use their cell phones to do a variety of different things, from storing word documents, using programs, playing games, using the GPS for travel, and other such things.
. · Retrieving contacts · Retrieving call logs.