

Mikee chols
A small company focused on providing a wide range of solutions ranging from Cybersecurity, emergency management & disaster relief.
MAX CYBERSECURITY National Security and Emergency Preparedness Professionals. MAX has been providing post disaster engineering assessment, design, construction and process support for many years. Among our many services, we provide management services to repair and restore shorelines and to harden wastewater, water and drainage facilities, streets & bridges and levees, floodwalls & floodgates. Our in-house electrical civil, structural, environmental, mechanical and hydraulic engineers have extensive experience in modeling, planning and hazard mitigation design. We understand the specific issues involved in assessments, planning, preparedness, emergency repairs, design, construction and other services required to protect property and save lives.
Preparedness is a shared responsibility; it calls for the involvement of everyone — not just the government — in preparedness efforts. By working together, everyone can help keep the nation safe from harm and help keep it resilient when struck by hazards, such as natural disasters, acts of terrorism, and pandemics. MAX CYBERSECURITY National Security and Emergency Preparedness Professionals. Every nation has an obligation to protect the essential government, financial, energy, transportation, and other critical infrastructure operations against terrorist activities and natural disasters.

MAX addresses homeland security and critical infrastructure needs through objective research and project management that assists national, state, and local agencies in preventing and mitigating terrorist activities, as well as in improving disaster preparedness, response, and recovery. Our Nation’s well-being relies upon secure and resilient critical infrastructure—the assets, systems, and networks that underpin American society.
Critical Infrastructure is the fundamental base of our country’s security, economy, and health. The MAX Team has led, or participated in, the development of national planning for cyber and CIP over the last 15 years – we know Risk Management & Leadership. The U.S. protects critical infrastructure based on the National Infrastructure Protection Plan (NIPP). How to secure your business as a leader? In today’s digitized world, any company and/or individual can fall victim to cybercrime.

Our interconnectivity serves as a breeding ground for malicious actors who are continuously looking to exploit unsecured access points. Banks, law firms, nonprofits, schools, the government – they are no exceptions. Cybersecurity is no longer limited to the IT department, nor is it a strict technical term. Poor Cyber Leadership Is Risky - Mikeechols Secure you Online. Let’s get as cyber real as real gets.
The current political leadership is a distraction to the work and vision of national cyber resilience. If you are a cyber professional, you must be confused about the U.S. geopolitical approach to cyber awareness and network resilience. If you are a person with low cyber aptitude, you must be confused, no matter your political persuasion. Let’s get this straight. At a United Nations speech, a couple of years ago, President Donald Trump proclaimed that China interfered in our elections. MAX CYBERSECURITY National Security and Emergency Preparedness Professionals. In addition to ad-hoc projects and custom investigations, our company offers online risk assessments for enterprises, executives, and key suppliers.
Executive Threat Assessments examine the online environment for potential physical and information security risks to executives and their family members. Vendor and Company Assessments offer a snapshot assessment of online exposure in key areas, including: Putting the Human Being in Security Planning. Homeland Security officials at all levels of government would be wise to embrace the concept of human factors.

As it relates to this article, Human factors apply principles of psychology focused on designing products, plans, and environments that enhance desired outcomes. That’s a mouth-full and academic-sounding. However, the application is real-world and accounts for what a human being may, and will do, in stressful situations. In the past, the security managers and community planners have done a poor job of modeling how humans might render a plan useless. A person’s personal situations or inability to manage stress conditions may cause them to freeze.
Implementing Cybersecurity and Risk Management Strategies. Cybersecurity risk management is the practice of identifying potential risks and vulnerabilities, assessing the impacts and likelihood of those risks, and mitigating the consequences if the risks become reality.

Today’s ever-changing security landscape demands that every organization, no matter its size or industry, develops and implements a cybersecurity risk management plan. Investing time and resources in creating a risk management plan illustrates that businesses recognize no one is immune to falling victim of a cyber-attack. It is important to note that not all risks that are identified can be eliminated and/or avoided. However, early threat detection and risk projection does buy your organization time, which can reduce the potential impacts of an event.
Below you will find 10 things to consider when developing your organization’s cybersecurity risk management plan: MAX CYBERSECURITY National Security and Emergency Preparedness Professionals. MAX CYBERSECURITY National Security and Emergency Preparedness Professionals. National Security and Emergency Preparedness Professionals. National Security and Emergency Preparedness Professionals. States Say Cybersecurity Is Our Business. States Say Cybersecurity is Our Business The federal government has been dragging its feet when it comes to addressing cybersecurity concerns.

Federal legislation has been slow to come, and state governments have been developing their own approaches. Several bills have been introduced and co-sponsored by members of Congress on both sides of the aisle. However, all efforts to address cyber law on a national level have stalled and many states just aren’t waiting around any longer. Clearly, the gravity of the situation surrounding cybersecurity measures must be taken seriously given the amount of data and network breaches the country has already experienced in recent years. To many people, this makes sense as a lot of citizens believe in state determination. Cybersecurity Risk Management. Wake-up people.
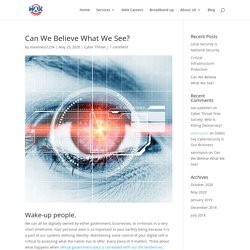
We can all be digitally owned by either government, businesses, or criminals in a very short timeframe. Your personal data is so important to your earthly being because it is a part of our systems defining identity. Maintaining some control of your digital self is critical to accessing what the nation has to offer. Every piece of it matters. Think about what happens when official government data is correlated with our life tendencies. The question is, are the hackers as who hold this data more dangerous than the government or companies seeking some of the same types of control over our lives? How to Conduct a Vulnerability Assessment: 5 Steps toward Better Cybersecurity? In today’s threat environment, it’s not just a good idea to conduct a cybersecurity vulnerability assessment, and to do so on a regular basis – it’s a core requirement for any organization that wants to protect critical data and ensure that its networks and systems aren’t exposed to cyberattacks.
Failing to do so can, simply put, spell the end of your company. According to IBM’s 2018 Cost of a Data Breach study, the average total cost of a data breach is now $3.86 million (an increase of 6.4 percent over the 2017 study), with an average cost of $148 per lost or stolen record (up 4.8 percent over the previous year’s study). And companies are taking note. Renub Research expects the global vulnerability assessment market to reach $15 billion by 2024, attributing the expected growth to several factors, including increased cloud adoption, the growing threat of data theft, and a surge in the number of systems affected by regulatory requirements. Vulnerability assessment benefits. How to Conduct a Vulnerability Assessment: 5 Steps toward Better Cybersecurity? Putting the Human Being in Security Planning. What Is Disaster And Emergency Management? What Is Disaster And Emergency Management?

When it comes to enterprise disaster management, there are multiple ways to describe how businesses prepare themselves for the same – namely disaster recovery, disaster management, emergency response, business continuity and so on. However, it should be noted that even though all of these terms refer to disaster planning one way or the other – each of these terms represents a separate meaning. One term can designate disaster planning while other can indicate responding to a disaster – which is the reason why you need to know the subtle differences between the same.
In this article guide, we’ll be explaining some of the major terms you need to know when it comes to disaster management. Implementing Cybersecurity and Risk Management Strategies. Micro Grid Development and Construction Service. Micro Grid Development and Construction MAX (dba MAX Services) has extensive experience working in Puerto Rico and globally to develop power system and capital projects.
MAX Services stands ready to assist is the recovery of power capabilities from catastrophic events. We are national planners and have staffed FEMA response efforts across the years. Our solutions include traditional solar, wind, Combined Heat & Power (CHP), and fuel cell solutions. Throughout the past years, our team has developed a deep array of relationships in the industry which allows them to quickly respond to bring your organization back on-line with innovative electrical systems. Max brings together world-class service professionals that are recognized as the valued leader on the topics of disaster management and Government support. Department of Homeland Security Consulting Services.
Max Cyber Threat Information Sharing Consulting In United States DC. Cyber Threat Information Sharing Consulting: Cyber-attacks have increased in frequency and sophistication, presenting significant challenges for organizations that must defend their data and systems from capable threat actors.

These actors range from individual, autonomous attackers to well-resourced groups operating in a coordinated manner as part of a criminal enterprise or on behalf of a nation-state. Threat actors can be persistent, motivated, and agile, and they use a variety of tactics, techniques, and procedures (TTPs) to compromise systems, disrupt services, commit financial fraud, and expose or steal intellectual property and other sensitive information. Given the risks these threats present, it is increasingly important that organizations share cyber threat information and use it to improve their security posture.
How to Conduct a Vulnerability Assessment: 5 Steps toward Better Cybersecurity? How do you Conducting a cyber risk assessment? - Mikeechols Secure you Online. Risk Assessments Help Save Businesses The steady increase in sophisticated and targeted cyber-attacks should serve as a warning for most organizations that it is not a matter of if, but when they will be hacked. From ransomware attacks to malicious phishing emails, cyber criminals use a multitude of vectors to gain access to an organization’s sensitive information. It is all done for financial gain, however the impact to victims can involve financial damage, a loss of performance or reputation.
All of these impacts can permanently dissolve a business. While the consequences may vary, financial loss and reputational damage are among the top repercussions reported by those who have experienced a data breach. National Security and Emergency Preparedness Professionals. Cybersecurity Risk Management. Poor Cyber Leadership Is Risky - Mikeechols Secure you Online. Services - MAX CYBERSECURITY National Security and Emergency Preparedness Professionals.
Poor Cyber Leadership Is Risky - Mikeechols Secure you Online. Cybersecurity Risk Management and Assessment. What are National Security and Cybersecurity Policy of Max. National Security and Cybersecurity Policy: MAX has a team of leaders and subject matter experts to promptly identify illicit cyber activity that may cause harm and a decrease value to businesses and Government entities. With over 15 years of national security experience, our leadership recognizes the need for a balance between convenience and security. For the last 10 years the leaders at MAX have created national policy supporting resilience programs. Executive Order implementation, Grants Management and Requirements Development are just a few of the areas of expertise MAX provides to our clients.With growing advances in technology and the rising accessibility to high-speed information technology systems, we are plagued with significant cybersecurity and national security risks.
The world will continue to become digitized with potential for a successful cyber event delivering greater consequences. Education is critical, from the Board of Director to the security guard. Department of Homeland Security Consulting Services. Department of Homeland Security Consulting Services. Max Cyber Threat Information Sharing Consulting In United States DC. Micro Grid Development and Construction Service. What are National Security and Cybersecurity Policy of Max. What are National Security and Cybersecurity Policy of Max. Emergency Management and Disaster Response Team. Critical Infrastructure Protection Program Support Near Me. Cybersecurity Risk Management and Assessment.
Iran Levels the Playing Field With Cyber Capabilities - Mikeechols Secure you Online. As everyone in the western hemisphere knows at this point the United States has a conflict with Iran. The United States killed Iran’s top military commander, General Qassem Soleimani under the direction of President Trump. He was unexpectedly killed in a drone strike ordered by our highest levels of government. The civil concerns when these types of actions are taken is how will one military act beget another. As far as we know, since the attack on Soleimani Iran has officially abandoned its commitment to the 2015 Nuclear Deal. They also launched missiles into a United States airbase in Iraq as part of its retaliation strategy.
The Power of the CISO 2020 - Mikeechols Secure you Online. Cybersecurity Risk Management and Assessment. Passionate Cyber Organizations. Getting to know organizations who are working to reduce in the cyber environment is very important to emerging cyber leaders. The factor that is consistent among all of them is that they were launched by people with a passion for helping others and who know the evolving threat. Here are a few organizations that you should know. Cyber security news and cyber security service. The Evolving Digital Monster. Hacking own people read cyber security news. Japan Begins Hacking IoT Devices Ahead of 2020 Olympics. A Culture of Cybersecurity Demands Cyber Education. Can’t Live Without It. Who Is Responsible When Tech Causes Pain. Scared to Near Death. Democracy Munipulation through Cyber Exploits. Cyber security news Mikeechols. Cyber security news Mikeechols. 911, What is Your Emergency? Cyber security service consultant Washington.
When calling 911, one is typically facing a dilemma that requires the assistance of the police. However, there have been several cases in which hackers use a harassment tactic called swatting to deceive an emergency service. The police are hoaxed into arriving at someone’s residence with the belief that there is a serious threat, only to find out that someone was playing a sick and twisted prank. This was the case for a Facebook cybersecurity executive who was detained by the Palo Alto Police for hours after they received a call claiming that he killed his wife, tied up his kids, and placed pipe bombs all around his home. Love Hacks You Into Pieces. Tell Me Where Your Love Lies For all of you online daters, beware. Small Businesses Are the New Hacker Target : Cyber security risks and theat.
Untitled. Businessman stressed. What is Firewalls and how it works? Cyber security threat. Untitled. Untitled. Small Businesses Are the New Hacker Target : Cyber security risks and theat. Sell Cyber Services. 911, What is Your Emergency? Cyber security service consultant Washington. Cybersecurity in60 Seconds - Oct 4 - Head In Sand. Cybersecurity in 60 Seconds - 8 days Until Elections. Cybersecurity in 60 Seconds - 6 Days Until the Election. November 13 - Cybersecurity In 60 Seconds. Cybersecurity In 60 Seconds - Business Cyber Regulation. Cybersecurity In 60 Seconds. Cybersecurity In 60 Seconds Smart Cities - Smart Cities. Cyber Secure Zones. Cybersecurity Tips for Everyone. Cybersecurity In 60 Seconds Huawei Is Spying. Cybersecurity in 60 Seconds Keep Enemies Close. Cybersecurity in 60 Seconds Keep Enemies Close. Untitled. Untitled.
Untitled. Cyber Threat Free Society: Who Is Killing Democracy? Untitled. Cyber security company Washington DC.
Untitled. Cyber security company washington. Untitled. States Say Cybersecurity Is Our Business. States Say Cybersecurity Is Our Business. Untitled. The U.S. GDPR: is it needs in USA? Check Your Network for Digital Landmines. Cyber Crime Does Pay - Here's how? Cyber security news. Government Partially Funds Dark Web Access ? Cyber security Services. New Year, New Congress, New Bills, New Cybersecurity Measures. Government Partially Funds Dark Web Access ? Cyber security Services. Mikeechols Secure you Online - Secure Cyber Life. Government Partially Funds Dark Web Access ? Cyber security Services. Who Is Do All the Hacking and why they are doing? Cyber security company. HHS and HSCC Release Voluntary Cybersecurity Practices for the Health Industry. Truth Behind The Major U.S. Newspaper Hacks. CISA Has A Tall Mission and Short Leash. Holiday Shopping From the Grinch.
Mikeechols Secure you Online - Secure Cyber Life.