

NSA trying to map Rogers, RBC communications traffic, leak shows - The Globe and Mail. The NSA Has Taken Over the Internet Backbone. We're Suing to Get it Back. Every time you email someone overseas, the NSA copies and searches your message.
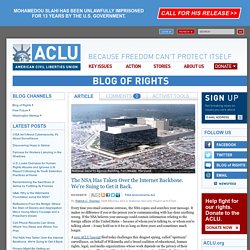
It makes no difference if you or the person you're communicating with has done anything wrong. If the NSA believes your message could contain information relating to the foreign affairs of the United States – because of whom you're talking to, or whom you're talking about – it may hold on to it for as long as three years and sometimes much longer. A new ACLU lawsuit filed today challenges this dragnet spying, called "upstream" surveillance, on behalf of Wikimedia and a broad coalition of educational, human rights, legal, and media organizations whose work depends on the privacy of their communications. The plaintiffs include Amnesty International USA, the National Association of Criminal Defense Lawyers, and The Nation magazine, and many other organizations whose work is critical to the functioning of our democracy.
But the effect of the surveillance we're challenging goes far beyond these organizations. Tech companies investigate reports of NSA backdoors in products. December 30, 2013 Some of the top technology companies – whose products have been reported by Germany-based news group Der Spiegel as containing NSA backdoors – have denied allegations of being involved and are conducting investigations.
The Der Spiegel reports are based on leaked documents, which reveal that network equipment company Juniper Networks had several compromised products, including the SSG 300 and SSG 500 series firewalls, the Juniper Netscreen NSG5T, NS25, NS50, and ISG1000, and the Juniper J-series and M-series routers. “We take allegations of this nature very seriously and are working actively to address any possible exploit paths,” Cindy Ta, a Juniper spokesperson, told SCMagazine.com in a Monday email. “[We] are committed to maintaining the integrity and security of our products. NSA Chief Mute on Spyware, Critical on Snowden. National Security Agency Director Mike Rogers on Monday defended his agency's online spying tactics to an audience of technologists in the nation's capital, but faced criticism about whether surveillance methods threaten cybersecurity and consumer privacy rights.
[READ: Months After Appeals Argued, NSA Cases Twist in the Wind] The NSA’s online data collection is not “a silver bullet in itself” to prevent terrorism, but “it generates value for the nation,” Rogers said during a conference on cybersecurity hosted by the New America Foundation. Former agency contractor Edward Snowden fueled criticism of government surveillance by exposing the broad scope of the NSA’s phone and Internet spying.
NSA director defends plan to maintain 'backdoors' into technology companies. The National Security Agency director, Mike Rogers, on Monday sought to calm a chorus of doubts about the government’s plans to maintain built-in access to data held by US technology companies, saying such “backdoors” would not be harmful to privacy, would not fatally compromise encryption and would not ruin international markets for US technology products.
Rogers mounted an elaborate defense of Barack Obama’s evolving cybersecurity strategy in an appearance before an audience of cryptographers, tech company security officers and national security reporters at the New America Foundation in Washington. In an hour-long question-and-answer session, Rogers said a cyber-attack against Sony pictures by North Korea last year showed the urgency and difficulty of defending against potential cyber threats. “If you look at the topology of that attack from North Korea against Sony Pictures Entertainment, it literally bounced all over the world before it got to California,” Rogers said.
Cookies used by NSA to spy. Will PRISM damage tech companies’ reputations for privacy? NSA ask top tech Cies to not reveal spying. Only One Big Telecom CEO Refused To Cave To The NSA ... And He's. Facebook Could Face Investigation In Ireland Over PRISM Data. Microsoft charge NSA for user data. Google, Facebook were paid millions by NSA to spy on taxpayers B.
Microsoft, Google Press Lawsuit On Government Spying Data. New leak shows feds can access user accounts for Google, Faceboo. NSA intercepts data from Google and Yahoo servers. NSA spying on international banking and credit card transactions. The US National Security Agency (NSA) has been spying on international banking and credit card transactions, according to a new report based on information leaked by Edward Snowden, as German Der Spiegel revealed.
The report indicates that the agency targeted VISA customers and global financial service SWIFT and created its own money flows database. More specific, the monitoring activities were carried out by a branch called "Follow the Money" (FTM). Once the information on transactions was obtained, it was redirected to the NSA's own financial database, called "Tracfin". According to the report, in 2011 the database contained 180 million records, with 84% of those being credit card transactions details.
RSA secret tie with NSA? NSA seeks to build quantum computer that could crack most types. War on Leaks Is Pitting Journalist vs. Journalist. IBM denies involvement with NSA. NSA’s backdoor catalog exposed: Targets include Juniper, Cisco, Top NSA Hacking Unit. Boundless Informant: the NSA's secret tool to track global surveillance data (Guardian) Linkedin challenges US government over data requests. How the cops watch your tweets in real-time. Recent leaks about the NSA's Internet spy programs have sparked renewed interest in government surveillance, though the leaks touch largely on a single form of such surveillance—the covert one.
But so-called "open source intelligence" (OSINT) is also big business— and not just at the national/international level. New tools now mine everything from "the deep Web" to Facebook posts to tweets so that cops and corporations can see what locals are saying. Due to the sheer scale of social media posts, many tools don't even aim at providing a complete picture. Others do. For instance, consider BlueJay, the "Law Enforcement Twitter Crime Scanner," which provides real-time, geo-fenced access to every single public tweet so that local police can keep tabs on #gunfire, #meth, and #protest (yes, those are real examples) in their communities. A look at the BlueJay interface shows it to be a fairly basic tool, but one that gets its power from full access to the Twitter "firehose" of all tweets.
Apple insists it did not work with NSA to create iPhone backdoor. Comment on Der Spiegel articles about NSA TAO Organization (UPDATE 2) UPDATE 2: On Monday, December 30th, Der Spiegel magazine published additional information about the techniques allegedly used by NSA TAO to infiltrate the technologies of numerous IT companies.
As a result of this new information coming to light, the Cisco Product Security Incident Response Team (PSIRT) has opened an investigation. Customers can stay informed of the progress of this investigation via the previously posted Cisco Security Response. December 29th -- An article was published in Der Spiegel today about the alleged capabilities of the United States National Security Agency (NSA) Tailored Access Operations (TAO) organization. The article says that TAO “exploits the technical weaknesses” of Information Technology products from numerous companies, and mentions Cisco. We are deeply concerned with anything that may impact the integrity of our products or our customers’ networks and continue to seek additional information. Additional Resources: Cisco Trustworthy Systems: