

Jokes > Hacker test. Home > jokes > Hacker test This test exists in many variants, reflecting the changing interests of nerds over time -- I manage a good score on all of them.

(And yes, by 'good' I do mean 'high' :-). I got the following off the Net, but without an attribution. If you know it, could you email it to me for inclusion? Thanks.
Niggles. Emerging tech to be aware of. Teaching aids. Azure. Networking. Mobile phones. Rfid. Internet of Things. Audio processing. MetaCASE. Diagrams for JavaScript and HTML, by Northwoods Software. How to Design Programs, Second Edition. Latex/Tex. Version control. MS-Windows - Tricks and Tips. Docker-AWS.
Computers in use - Voices of Science. Designing and programming computers - Voices of Science. Xml and java. GPS as a Time Source - GPSD/NTPD. WiFi. Ubuntu (or other Linux) on the Asus Transformer Book T100. This post is now out of date — see the latest update, here The T100 is a nice little convertible tablet/netbook.
Internal and External Linkage in C++ – Peter Goldsborough. Ever come across the terms internal and external linkage?

Ever wanted to know what the extern keyword is for and what declaring something static does in the global scope? University of Abertay Dundee - Portal. Module Code : TG0903G Module Title : Network Infrastructure and Services AimThe aim of this module is to provide the student with the knowledge and skills to analyse, design and implement network directory services and scaleable routed and switched networks.

Learning OutcomesBy the end of this module the student should be able to : 1. Describe and evaluate various implementations of directory services. 2. Identify the stages in designing and implementing a directory services and network infrastructure. 3. Configuring Mozilla Thunderbird to use your domain's Global Address Book - Web Browsers. 1.
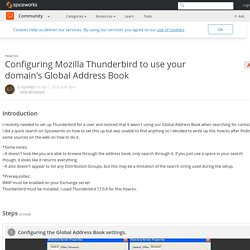
Open up the address book by clicking the icon on the toolbar. 2. Click File -> New -> LDAP Directory 3. Use the following settings to set up your address book: Solarized - Ethan Schoonover. Precision colors for machines and people Solarized is a sixteen color palette (eight monotones, eight accent colors) designed for use with terminal and gui applications.
It has several unique properties. Welcome to STINGER - STINGER.
Automata: the good, the bad and the cheaters (and a bit of magic too) Movie animatronics create some breathtaking computer-controlled movie monsters, but the history of making things come alive and move the way you want them to stretches way beyond the Hollywood hills.

Automata, mechanically animated figures and creatures, go way back in history and show just how clever inventors the world over can be. The contraptions they built were the forerunners of today’s computers, and if these inventors were at work now, they would be computer scientists. So let’s have a look at some of the more interesting and influential characters in automata history. Boat the beat.
Gnuplot. Raspberry pi. P2P References. RFC 4981 - Survey of Research towards Robust Peer-to-Peer Networks: Search Methods. [Docs] [txt|pdf] [draft-irtf-p2prg-...]

[Diff1] [Diff2] INFORMATIONAL Network Working Group J. Risson Request for Comments: 4981 T. Moors Category: Informational University of New South Wales September 2007 Status of This Memo This memo provides information for the Internet community. It does not specify an Internet standard of any kind. RFC 4981 Survey of Research on P2P Search September 2007 Table of Contents 1.
OS Statistics.
Geotagging. REPL. Tinycore. PET. Stats. Openoffice. Stringtemplate. Kde. Graph databases. Develpers tools. PersistentObjects. Social media APIs. Tiling/packing problems. R. Beagleboard. Uproc. Usb flash. Linux. Java graphics. Thunderbird. Touchscreens. Via epia mii. Data visualisation.
Internet of Things. Eeepc 901. Iphone. Using mini (keychain) digital picture frames under Linux. PS3 Linux - GPU computing. Wii. Graphics. Cups. Intel Galileo. Bits and PCs. Frequently Asked Questions · jackpal/Android-Terminal-Emulator Wiki. Is "Terminal Emulator for Android" the same app as "Android Terminal Emulator"?
Yes. The name was changed due to Google Play branding guidelines. Unfortunately Google Play does not allow applications that start with the word "Android". What is a terminal emulator? A terminal emulator is a program that makes your Android phone act like an old fashioned computer terminal. If you don't know what all that means, and why it's cool, then this probably isn't the program for you. Help, I'm lost. I've written a brief, incomplete, guide to using the built-in Android shell: Android Shell Command Reference What sort of games does this emulator play? Reference.
Zdnet. As reported by Wayne Williams at Betanews and confirmed by us, a simple registry hack to a Windows XP system tricks Windows Update into providing updates for it.
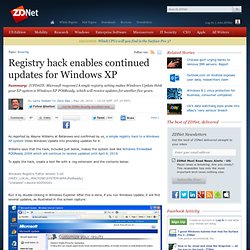
Williams says that the hack, included just below, makes the system look like Windows Embedded POSReady 2009 which will continue to receive updated until April 9, 2019. To apply the hack, create a text file with a .reg extension and the contents below: Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\WPA\PosReady] "Installed"=dword:00000001 Run it by double-clicking in Windows Explorer. After this is done, if you run Windows Update, it will find several updates, as illustrated in this screen capture:
NTP Debugging Techniques. NTP Debugging Techniques from Pogo, Walt Kelly We make house calls and bring our own bugs. Once the NTP software distribution has been compiled and installed and the configuration file constructed, the next step is to verify correct operation and fix any bugs that may result. Usually, the command line that starts the daemon is included in the system startup file, so it is executed only at system boot time; however, the daemon can be stopped and restarted from root at any time. Usually, no command-line arguments are required, unless special actions described in the ntpd page are required.
Initial Startup The best way to verify correct operation is using the ntpq and ntpdc utility programs, either on the server itself or from another machine elsewhere in the network. Easter egg hunt: Seven secrets of the world wide web. 22 January 2014Last updated at 19:10 ET By Dave Lee Technology reporter, BBC News If you're looking to fill six hours, try searching "atari breakout" on Google Images There are many hidden secrets tucked away in the media we consume, placed there by mischievous - or perhaps just bored - programmers and developers. They're known as "Easter eggs" - and the web has them in abundance. Andy Clarke, who owns Wales-based web design studio Stuff & Nonsense, has his own simple definition: "It's something unexpected that makes you smile.
"
Nexus 7. Hacker's Delight. Cryptography - What is the most efficient way to detect and to break xor encryption? - Reverse Engineering Stack Exchange. Tools for Examining XOR Obfuscation for Malware Analysis. There are numerous ways of concealing sensitive data and code within malicious files and programs. Fortunately, attackers use one particular XOR-based technique very frequently, because offers sufficient protection and is simple to implement. Here's a look at several tools for deobfuscating XOR-encoded data during static malware analysis. We'll cover XORSearch, XORStrings, xorBruteForcer, brutexor and NoMoreXOR. The XOR-based approach to obfuscating contents often works like this: The attacker picks a 1-byte value to act as the key. To deobfuscate the protected string, the attacker's code repeats step #2, this time XOR'ing each byte in the encoded string with the key value.
I/O Redirection. There are always three default files open, stdin (the keyboard), stdout (the screen), and stderr (error messages output to the screen). These, and any other open files, can be redirected. Redirection simply means capturing output from a file, command, program, script, or even code block within a script (see Example 3-1 and Example 3-2) and sending it as input to another file, command, program, or script.
The Rural Broadband Partnership. Hash function. A hash function that maps names to integers from 0 to 15. There is a collision between keys "John Smith" and "Sandra Dee". Uses[edit] Hash tables[edit] Thus, the hash function only hints at the record's location — it tells where one should start looking for it.
Lejos. Image processsing. Regular expressions. BASIC Programming Guide. This guide provides an introduction to programming with OpenOffice.org Basic. OpenCL. Unix spells. Security. Java. Using Multiple Active Result Sets (MARS) SQL Server 2005 introduced support for multiple active result sets (MARS) in applications accessing the Database Engine. In earlier versions of SQL Server, database applications could not maintain multiple active statements on a connection. When using SQL Server default result sets, the application had to process or cancel all result sets from one batch before it could execute any other batch on that connection. SQL Server 2005 introduced a new connection attribute that allows applications to have more than one pending request per connection, and in particular, to have more than one active default result set per connection. MARS simplifies application design with the following new capabilities: Applications can have multiple default result sets open and can interleave reading from them.
Kane.