

Cyber Security Expert
Are you in search of ways to secure your devices and networks? Your search ends here! Cyber Cops lists the best tools and techniques and compares multiple online gadgets for users to make an informed choice!
What is Sachet Complaints Reporting Portal in India 2020. Sachet Complaint Portal Sachet Complaint Reporting Portal in India: Launch and Objective: In 2016, the former RBI Governor Raghuram Rajan had launched a portal to curb illegal collection of money by companies.The “Sachet” website is an initiative of the State Level Coordination Committee (SLCC).

SLCC is the joint forum formed in all the States to facilitate the information sharing among the Regulators viz. RBI, SEBI, IRDA, NHB, PFRDA, Registrar of Companies etc. with the objective to control the incidents of unauthorized acceptance of deposits by unscrupulous entities. IPS Agam Jain: Always leading from front. The true leadership story of IPS Agam Jain: One fine morning, instead of going for usual morning walk and exercise, IPS Agam Jain thought of channelizing the same energy into something productive for the Police Station.
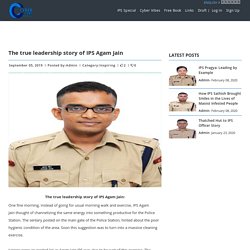
The sentary posted on the main gate of the Police Station, hinted about the poor hygienic condition of the area. Soon this suggestion was to turn into a massive cleaning exercise. YouTube. What makes cybersecurity important? The importance of cybercrime security is on the rise.

Our society is more technologically dependent than ever before and this trend is bound to rise. Personal data that could lead to identity theft is now accessible to the public via social media accounts. Sensitive information comprising things like credit card information, bank account details, social security numbers, etc. are now stored in cloud storage devices like Google Drive or Dropbox.
Thus, no matter if you are an individual or own a small or a big business, you depend on computer systems every day and this makes information and computer security the need of the hour. How to find pwned emails - Cyber Cops. How to Track Someone's Location with IP Logger - Cyber Cops. How to Track Someone's Location with IP Logger IP Logger is considered Gold standard for finding the true location of a suspect.
The website commands huge respect among OSINT experts and investigators alike. The process involves sending special customized links created with the help of IP Logger to the suspect. Once the recipient clicks on it, the IP address and geographical location is revealed. The process can be executed for a variety of purposes, which requires knowing the true location of a person.
One Stop Solution. IPS Saidulu Adavath - Story of perseverance and hard work: IPS Saidulu Adavath - Story of perseverance and hard work: Let’s read the galvanizing story of Saidulu, a son of tribal farm laborers, who chased his dream with strong determination and perseverance and how he made a rugged journey from a thatched hut to the portals of Indian Police Service.

One rose from abject poverty to power corridors, conquered manifold obstacles, to secure All India Rank 795 in the country’s toughest – Civil Services Exam, 2016. Saidulu was born and raised in a poor, illiterate family at a tiny hamlet called Geri thanda of Kodrapol, Miryalaguda. He experienced severe hardships in his childhood. The family often struggled a lot to have three square meals a day. A stroke of misfortune hit him in IX th standard, when his father died of a sudden cardiac arrest.
How to Lodge Complaints with Instagram - Cyber Security Experts. SOP for Money Refund in Online Fraud Cases. SOP for Money Refund in Online Fraud Cases: The virtual world crimes including cyber frauds are rising at an alarming rate.

According to crime data, identity theft accounts for 77 % of the fraud cases registered in India. Another analysis suggests that, “one in every three Indian will be affected by identity theft at some point in their lives”. Victims in cyber fraud cases are concerned not only with conviction of cyber criminals but also with refund of money.
Hence, this blog, focuses on legal aspect of refund of money as well as procedure for the same. RBI Notification:The bank’s (All scheduled commercial banks, Small finance bank and Payment Banks) liability in case of Unauthorized Electronic Banking Transactions is governed by RBI circular - RBI/2017-18/15, DBR.No.Leg.BC.78/09.07.005/2017-18 dated July 06, 2017. How to Report Abusive Post on Facebook – Cyber Cops. How to Report Abusive Post on Facebook How to Report an Abusive Post, Video, Photo etc on Facebook: Facebook claims that “When something gets reported to Facebook, we review it and remove anything that goes against the Facebook Community Standards.
We don't include any information about the person who filed the report when we reach out to the reported. Get the Best Solution of Cyber Crime with Cyber Crime Security Experts. WhatsApp Frauds You Need to Avoid – Cyber Cops. Whatsapp Fraud Whatsapp Fraud: WhatsApp is increasingly being used to de-fraud gullible and innocent people.
In this Section, we shall discuss their Modus Operandi. Modus Operandi:Step 1:The scammer first sends an attractive WhatsApp message. In some cases, the sender’s number starts with the code + 92 i.e, numbers originating from Pakistan. Has won a major lottery/ contest/ jackpotHas been selected for a high-profile job Will be given shares of a Company etc Step 2:Due to temptation, once a person shows interest, scammer builds trust by sending forged identity proofs, fake certificates, documents etc. Step 3:To receive the prize, shares etc., fraudster demands initial payment as Processing fees Handling charges Transportation cost Paper work Legal expenses Income tax deduction Any other pretext.
The Most Common Online Threats -CYBER COPS. The Most Common Online Threats: Computer Viruses:A computer virus is a malicious code or program which alters a computer negatively.
It may attach itself to a legitimate program or document and execute itself remotely. As per stats, about 33% of household computers are affected by some form of malware, more than half of which are computer viruses. Brute Force Attacks Explained. What is a Brute-force attack?

Brute force attack is an act of trying every possible combination of a given key-space or character set for a given length. Thus, the attacker first exhaustively tries all the single charecter passwords i.e, "a to z", "A to Z", "0 to 9", all the special characters etc. Tips That Help Increase Cybersecurity Awareness in Your Office. What is Advertisement Based Fraud – Cyber Cops. Advertisement Based Frauds: The fraud is through fraudulent advertisements in OLX, Indiamart etc. Modus Operandi:The fraudster displays products for sale on online platforms, typically at highly under-valued rates. When a gullible customer, due to temptation contacts the fraudster, they first ask for initial payment under different pretext like to book the order, as parcel fees, transportation costs, GST charges etc. To win the trust of the victim, they send fake ID proofs, at times even of army-men!
Thus, the victim ends up paying the money into the different accounts furnished by the fraudster. How to Report an Imposter Account on Facebook – Cyber Cops. How to Report an Imposter Account on Facebook How to Report an Imposter Account on Facebook: A fake account is an impersonated account generally for malicious ends. What is Juice Jacking? How it happens? What are the safety measures? Juice Jacking Juice Jacking: What’s Juice Jacking?
Public places like airport, railways, shops etc have public charging stations and we are often desperate to use them when our devices are drained out. But, the same charging port can take complete control of your smart-phone and inject malicious codes. Thus, public charging spots are both boon and bane for users. Gadgets. How to Connect Mobile Whatsapp on your Desktop or Laptop. How to Report Child Pornography – Cyber Cops. What are Vishing or OTP frauds and how to Avoid Them – Cyber Cops. Vishing OR OTP Fraud OTP Based Frauds: What is OTP Sharing Fraud? In this fraud, the victim gets an anonymous call where the caller introduces himself/ herself as a bank employee, bank manager etc. The caller tries collect credit / debit card details and OTP (One Time Password) using various pretext like card renewal, unblocking the card, card activation, compliance with new norms like Aadhar card linkage etc.
Once the victim mistakenly shares his card details and OTP, the fraudster siphons off the money from the victim’s bank account/ wallet. Interestingly, in most of the cases the fraudster already has partial information about the victim and the bank details which enables convince the victim through various social engineering techniques. Modus Operandi: Fraudsters ask for OTP and unaware people may share their OTP message with them. How to Lodge Complaints with Instagram - Cyber Security Experts. An insight into anti-virus. Anti-Virus Anti-Virus: Introduction:Antivirus software also known as anti-malware, is a computer program used to prevent, detect, and remove malwares. Learn how to Track an Email - Cyber Cops. How to Track an Email. Protect Your Account from Facebook Hackers – Cyber Cops. Facebook Hacking: Facebook account can be hacked if - The login credentials has been shared Someone has access to the registered phone number/ email ID You click on a Phishing link and fill in the login details You use a device with key-logger pre-installed You use a spoofed/ compromised network.
What is a Key-logger and How to Detect Key-logger on Computer. Know How To Detect Hidden Cameras and Micro-phones. Detecting Hidden Cameras and Micro-phones: How to Avoid Tracking. Vulnerabilities that Hackers Exploit in Websites. Vulnerabilities that Hackers Exploit in Websites: Report cybercrime complaints online. Mind Your Google Searches - Delete Your Browsing History. Open Source Intelligence Techniques. Popular OSINT Tools. How and Where to Report Cyber-crimes in India Officially. How to Find Pwned Emails - Cyber Cops. How to Create Unbreakable Passwords – Cyber Cops.