

GUI Architectures. There have been many different ways to organize the code for a rich client system.

Here I discuss a selection of those that I feel have been the most influential and introduce how they relate to the patterns. Graphical user interfaces have become a familiar part of our software landscape, both as users and as developers. Looking at it from a design perspective they represent a particular set of problems in system design - problems that have led to a number of different but similar solutions. My interest is identifying common and useful patterns for application developers to use in rich-client development. I've seen various designs in project reviews and also various designs that have been written in a more permanent way. In this essay I want to explore a number of interesting architectures and describe my interpretation of their most interesting features.
(There is something of an exception here, in that I did have access to a running Smalltalk-80 to examine MVC. Forms and Controls. The Clean Architecture. Over the last several years we’ve seen a whole range of ideas regarding the architecture of systems.

These include: Hexagonal Architecture (a.k.a. Ports and Adapters) by Alistair Cockburn and adopted by Steve Freeman, and Nat Pryce in their wonderful book Growing Object Oriented Software Onion Architecture by Jeffrey Palermo Screaming Architecture from a blog of mine last year DCI from James Coplien, and Trygve Reenskaug. BCE by Ivar Jacobson from his book Object Oriented Software Engineering: A Use-Case Driven Approach Though these architectures all vary somewhat in their details, they are very similar. Each of these architectures produce systems that are: Independent of Frameworks.
The diagram at the top of this article is an attempt at integrating all these architectures into a single actionable idea. The Dependency Rule The concentric circles represent different areas of software. The overriding rule that makes this architecture work is The Dependency Rule. Entities Use Cases Conclusion. Entity-Control-Boundary Pattern. When identifying the elements for some scenario of system behavior, you can align each participating element with one of three key perspectives: Entity, Control, or Boundary.
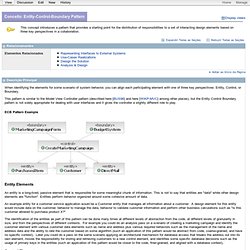
This pattern is similar to the Model View Controller pattern (described here [BUS96] and here [WIKP-MVC] among other places), but the Entity Control Boundary pattern is not solely appropriate for dealing with user interfaces and it gives the controller a slightly different role to play. ECB Pattern Example Entity Elements An entity is a long-lived, passive element that is responsible for some meaningful chunk of information. This is not to say that entities are "data" while other design elements are "function". Use-Case 2.0 ebook. Introduction to Robustness Diagrams. A robustness diagram is basically a simplified UML communication/collaboration diagram which uses the graphical symbols depicted in Figure 1.

As you can see robustness diagrams depict several types of concepts: Actors. This is the same concept as actors on a UML use case diagram. Boundary elements. These represent software elements such as screens, reports, HTML pages, or system interfaces that actors interact with. Introduction to UML 2 Use Case Diagrams. Use case diagrams depict: Use cases.

A use case describes a sequence of actions that provide something of measurable value to an actor and is drawn as a horizontal ellipse. Clean Architecture in Spring MVC with a data-centric approach. UML: The Art of Modeling Demonstrated. Managing Non-Functional Requirements in SAFe. Managing non-functional requirements (NFR’s) in software development has always been a challenge.

These “system capabilities”, such as ‘how fast a page loads’, ‘how many concurrent users the system can sustain’ or ‘how vulnerable to denial-of-server attacks can we be", traditionally have been ascribed as belonging to “quadrant four of the agile testing quadrants” of Brian Marick. That is, these are tests that are technology facing and which critique the product. That said, it has never been clear *why* this is so as this information can be critical for the business to clearly understand. In the Scaled Agile Framework (SAFe) NFR’s are represented as a symbol bolted to the bottom of the various backlogs in the system. This indicates that they apply to all of the other stories in the backlog. This paper advances an approach to handling NFR’s in SAFe which promotes the concept that NFRs are more valuable when considered as first class objects in our business facing testing and dialogs.