

Sending an anti-forgery token with Razor Pages AJAX requests. ASP.NET Razor Pages uses anti-forgery tokens to protect websites against Cross-site request forgery (CSRF) attacks.
When posting information to a Razor Page handler, you need to take special care to send this anti-forgery token otherwise the request fails. This blog post looks at a couple of techniques you can use to ensure the anti-forgery token is sent with your AJAX POST requests.
A Step by Step Guide on How to Host and Deploy an ASP NET Core app with SSL using Let's Encrypt, Traefik and Docker - Take 2. In this post I describe how to deploy an ASP.NET Core app that has been dockerized and host it on a Linux machine with SSL enabled for free.

This is all possible using Traefik, a reverse proxy and load balancer and its integration with Let's Encrypt. On Reflection In my previous post, whilst it still holds true, I had to break it down into 3 blog posts. How to add Sign in with Google, GitHub, Slack and more with ASP.NET Core. I'm sure you have come across web and mobile applications where they offer social logins such as Google, Facebook, Twitter and many more.
This is great, as its one less sign up and login you have to remember. It also reduces the friction of signing up. It's especially great if you can incorporate them into your own applications. The main benefit of this is that it lowers the barrier of entry for people registering to use your product or service. If the potential customer or user has the social login that you support, the more likely they will try the product or service. Aspnet-contrib/AspNet.Security.OAuth.Providers: OAuth2 social authentication providers for ASP.NET Core.
Use cookie authentication without ASP.NET Core Identity. Token Authentication in ASP.NET Core 2.0 - A Complete Guide. Token authentication has been a popular topic for the past few years, especially as mobile and JavaScript apps have continued to gain mindshare.

Widespread adoption of token-based standards like OAuth 2.0 and OpenID Connect have introduced even more developers to tokens, but the best practices aren’t always clear. ASP.Net Core - Protect your API with API Keys. Disclaimer There's a bunch of different ways to handle authentication/authorization.

As pointed out here on Twitter by Greg Bair, API keys has some limitations/drawbacks. Lightweight custom authentication with ASP.NET Core. ASP.NET Core Identity is popular choice when web application needs authentication.
It supports local accounts with username and password but also social ID-s like Facebook, Twitter, Microsoft Account etc. But what if ASP.NET Core Identity is too much for us and we need something smaller? What if requirements make it impossible to use it? Getting Started With ASP.NET Core 2.0 Identity And Role Management. Introduction In this article, we will see in detail how to use ASP.NET Core Identity in MVC Application for creating user roles and displaying the menu depending on user roles.
Here, we will see how to, Dodyg/practical-aspnetcore: Practical samples of aspnet core 2.1, 2.2, 3.0 and 3.1-Preview2 projects you can use. Readme contains explanations on all projects. .NET Foundation.
Performance. One user scenario to rule them all. Sergey The async series Almost every non-trivial behavior of the async methods in C# can be explained based on one user scenario: migration of the existing synchronous code to asynchronous should be as simple as possible.
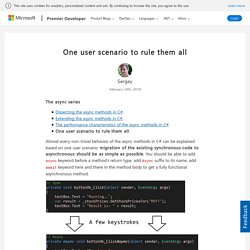
You should be able to add async keyword before a method’s return type, add Async suffix to its name, add await keyword here and there in the method body to get a fully functional asynchronous method. This “simple” scenario drastically affects the behavior of asynchronous methods in many different ways: from scheduling task’s continuations to exception handling. The scenario sounds plausible and important but it made simplicity behind the async methods very deceptive. Synchronization context UI development is one of the areas where the scenario mentioned above was especially important.
Deadlocks Let’s review a small and relatively simple piece of code. The code will cause a deadlock. You may argue, that the issue is relatively easy to spot, and I’ll agree with you. Sergey. Links about async/await in C# - Meziantou's blog. Cryptography in .NET - Meziantou's blog. Cryptography is a very important thing for information security.

Information security is composed of 4 parts: Integrity: ensure a document is not alteredConfidentiality: ensure only authorized people can read a documentAuthentication: ensure the document was written by an identified personNon-Repudiation: prove who/where a document came from as well as the authenticity of that message, so the sender cannot deny they have sent it. Alecgn/crypthash-net: CryptHash.NET is a .NET multi-target library to encrypt/decrypt/hash strings and files, with an optional .NET Core multiplatform console utility. RNGCryptoServiceProvider Class (System.Security.Cryptography)
Caveats in ASP.NET Core Data Protection - Edi.Wang. ASP.NET Core provides a built-in Data Protection mechanism to let us encrypt or decrypt sensitive data.
There are some limitations that can cause problems while bringing convenience. I met some problems these days. My Scenario My blog system has a feature to send email notifications, so you need to configure an email account to let the program use that account to send mail to an administrator or users. This involves the question of how to securely store your account password. Don't Reinvent the Wheel Before designing a feature, I usually check the internet first to see if there is already a framework feature that comes with the functionality to complete the requirements. You can check the detailed introduction on Microsoft Docs here.
The algorithm used by Data Protection is by default AES, which can meet my needs. Encryption and Decryption Flow After the framework helps us hide the complex algorithm process, we can complete the encryption and decryption with just 3 simple API calls: Usage. Key Storage Format — ASP.NET documentation. Objects are stored at rest in XML representation.
The default directory for key storage is %LOCALAPPDATA%\ASP.NET\DataProtection-Keys\. The <key> element¶ Keys exist as top-level objects in the key repository. By convention keys have the filename key-{guid}.xml, where {guid} is the id of the key. Each such file contains a single key. The <key> element contains the following attributes and child elements: The key id. In the above example, the key’s id is {80732141-ec8f-4b80-af9c-c4d2d1ff8901}, it was created and activated on March 19, 2015, and it has a lifetime of 90 days. The <descriptor> element¶ The outer <descriptor> element contains an attribute deserializerType, which is the assembly-qualified name of a type which implements IAuthenticatedEncryptorDescriptorDeserializer.
The particular format of the <descriptor> element depends on the authenticated encryptor implementation encapsulated by the key, and each deserializer type expects a slightly different format for this. Ephemeral data protection providers — ASP.NET documentation. There are scenarios where an application needs a throwaway IDataProtectionProvider. For example, the developer might just be experimenting in a one-off console application, or the application itself is transient (it’s scripted or a unit test project). To support these scenarios the package Microsoft.AspNetCore.DataProtection includes a type EphemeralDataProtectionProvider.
This type provides a basic implementation of IDataProtectionProvider whose key repository is held solely in-memory and isn’t written out to any backing store. Each instance of EphemeralDataProtectionProvider uses its own unique master key. Therefore, if an IDataProtector rooted at an EphemeralDataProtectionProvider generates a protected payload, that payload can only be unprotected by an equivalent IDataProtector (given the same purpose chain) rooted at the same EphemeralDataProtectionProvider instance. Hash passwords in ASP.NET Core. Non-DI aware scenarios for Data Protection in ASP.NET Core.