

Hacker. Member: bmlbytes. What the Hack ?! - the temptation of the Dark Side - StumbleUpon. 'For educational purposes' ... that must be about the most widespread excuse for publishing virus creation tools,descriptions of exploits, 'hacking' manuals and the likes.
Personally,I don't see much of educational effects in using a Windows application to create a virus (next >> next >> next >> finish - congratulations, you have created the Ana Kournikova worm) or following simple instructions to break in to a system - sometimes as simple as 'find a Kazaa user, use your browser to access his PC on TCP port 1214 - you now have access to all his files'. I also disagree with the motivation / excuses such as 'the right to information - all information - anywhere' or 'I am motivated by curiosity'.
I would not like someone to enter my house, go through my drawers and read my papers, letters or whatever. I don't give a damn if this person is doing it 'just to see if it can be done', or to demonstrate the poor quality of my front door lock. What the Hack ?! - the temptation of the Dark Side.
Hacking servers. Inside the precision hack & Music Machinery. There’s a scene toward the end of the book Contact by Carl Sagan, where the protagonist Ellie Arroway finds a Message embedded deep in the digits of PI.
The Message is perhaps an artifact of an extremely advanced intelligence that apparently manipulated one of the fundamental constants of the universe as a testament to their power as they wove space and time. I’m reminded of this scene by the Time.com 100 Poll where millions have voted on who are the world’s most influential people in government, science, technology and the arts.
Just as Ellie found a Message embedded in PI, we find a Message embedded in the results of this poll. The Hacker Manifesto - StumbleUpon. By +++The Mentor+++ Written January 8, 1986 Another one got caught today, it's all over the papers.

"Teenager Arrested in Computer Crime Scandal", "Hacker Arrested after Bank Tampering"... Damn kids. They're all alike. But did you, in your three-piece psychology and 1950's technobrain, ever take a look behind the eyes of the hacker? I am a hacker, enter my world... Mine is a world that begins with school... Google Hacking Database, GHDB, Google Dorks.
PirateBox DIY - David Darts Wiki. Access Any Website Or Forum Without Registering. Visit any forum or website to find something useful and they will ask you to register.
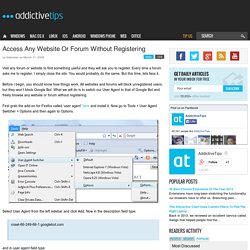
Every time a forum asks me to register, I simply close the site. You would probably do the same. But this time, lets face it. Before I begin, you should know how things work. All websites and forums will block unregistered users, but they won’t block Google Bot. First grab the add-on for Firefox called ‘user agent’ here and install it. Select User Agent from the left sidebar and click Add. Crawl-66-249-66-1.googlebot.com and in user agent field type:
Hacker warfare. How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine. However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. The following are some of the hacks that can be accomplished using Google. 1. Hacking Security Cameras There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time.
Inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls. you now have access to the Live cameras which work in real-time. Intitle:”Live View / – AXIS” 2. 3. . “? 4. Infographic: How Hackers Get In and Got In.