

Find Security Bugs.
OWASP Global Webinars. APPSEC Cali 2018 - OWASP Top 10. OWASP Secure Headers Project. The following contains a list of HTTP response headers related to security.
OWASP Dependency Check. OWASP Dependency-Check Dependency-Check is a utility that identifies project dependencies and checks if there are any known, publicly disclosed, vulnerabilities.
Currently, Java and .NET are supported; additional experimental support has been added for Ruby, Node.js, Python, and limited support for C/C++ build systems (autoconf and cmake). The tool can be part of a solution to the OWASP Top 10 2017 A9-Using Components with Known Vulnerabilities previously known as OWASP Top 10 2013 A9-Using Components with Known Vulnerabilities.
Introduction. OWASP SAMM Project. SAMM is developed and maintained by a worldwide team of volunteers.
We have also been helped by many organizations, either financially or by encouraging their employees to work on SAMM. SAMM Adopters SAMM is the premier open source software assurance framework. You can find a list of SAMM adopters online. Software Assurance Maturity Model (SAMM): A guide to building security into software development. OWASP ASVS / Application Security Verification Standard 3.0.1. Shenril/owasp-asvs-checklist: OWASP ASVS checklist for audits. OWASP/ASVS: Application Security Verification Standard. ASVS/OWASP Application Security Verification Standard 4.0-en.pdf at master · OWASP/ASVS. OWASP/ASVS: Application Security Verification Standard. How To Start With Software Security. The software security field sometimes feels a bit negative.
The focus is on things that went wrong and people are constantly told what not to do. Build Security In One often heard piece of advice is that one cannot bolt security on as an afterthought, that it has to be built in. Swiss cheese model. The Swiss cheese model of accident causation illustrates that, although many layers of defense lie between hazards and accidents, there are flaws in each layer that, if aligned, can allow the accident to occur.
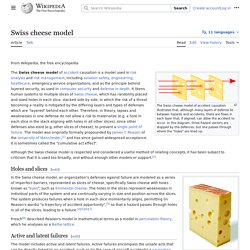
Although the Swiss cheese model is respected and considered to be a useful method of relating concepts, it has been subject to criticism that it is used too broadly, and without enough other models or support.[2] Failure domains[edit] Reason hypothesized that most accidents can be traced to one or more of four failure domains: organizational influences, supervision, preconditions, and specific acts.[3][4]For example, in aviation, preconditions for unsafe acts include fatigued air crew or improper communications practices. Unsafe supervision encompasses for example, pairing inexperienced pilots on a night flight into known adverse weather. Organizational influences encompass such things as reduction in expenditure on pilot training in times of financial austerity.[5][6]
Defense in depth (computing) Physical controls are anything that physically limits or prevents access to IT systems.
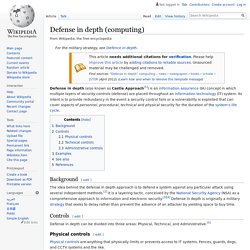
Fences, guards, dogs, and CCTV systems and the like. Technical controls are hardware or software whose purpose is to protect systems and resources. Examples of technical controls would be disk encryption, fingerprint readers, and Windows Active Directory. Hardware technical controls differ from physical controls in that they prevent access to the contents of a system, but not the physical systems themselves. Administrative controls are an organization's policies and procedures. OWASP DefectDojo Project. OWASP Juice Shop Project. OWASP Juice Shop Tool Project The most trustworthy online shop out there.
OWASP / Cross-site request forgery (CSRF ou XSRF) Dans ce troisième article de la série consacrée aux failles applicatives, j’aborde les failles CSRF au travers de l’OWASP.

Vous découvrirez ces failles et apprendrez à les détecter. Vous verrez enfin les moyens de vous en prémunir. Fixation de session. Un article de Wikipédia, l'encyclopédie libre.
Untitled. Center for Internet Security. Développement sécurisé - Apprendre à maitriser le risque. À l'origine des failles de sécurité, il y a le plus souvent, une erreur humaine.
Et les développeurs sont (à quelques rares exceptions prêtes ) des humains. Pourtant il existe quelques principes de base notamment recommandée par l'OWASP qui permettent de produire du code à minima sécurisé. Mais peu de développeurs prennent le temps d'intégrer et d'appliquer ces principes. C'est d'ailleurs pour ça que le bug bounty et bountyfactory.io ont le vent en poupe, car au-delà d'aider les boites à mieux se sécuriser, il permet aussi aux développeurs de monter en compétences en se frottant à une véritable communauté d'experts en sécurité. Souvenez-vous, en 2013, Adobe subissait une fuite de données impactant 38 millions de personnes. Puis en 2015, Orange Business a vu fuiter plus de 9500 contacts pros (adresses postales, téléphones, noms de sociétés de responsables de comptes, responsables commerciaux, RSSI...etc.) à cause d'une erreur dans un formulaire, autorisant une injection SQL.
CI/CD and DevSecOps Automation. OWASP DefectDojo Project. OWASP Find Security Bugs. MobSF/Mobile-Security-Framework-MobSF: Mobile Security Framework is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing framework capable of performing static analysis, dynamic analysis, malware analysis and web API testing. MobSF/Mobile-Security-Framework-MobSF: Mobile Security Framework is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing framework capable of performing static analysis, dynamic analysis, malware analysis and web API testing. OpenSecurity - Security Training, Security Engineering, Pentest, Code Review, and Research. DevOps Handbook Series Part 1: The Three Ways Cont.
OWASP Juice Shop Project. Same-origin policy. Security measure for client-side scripting This mechanism bears a particular significance for modern web applications that extensively depend on HTTP cookies[1] to maintain authenticated user sessions, as servers act based on the HTTP cookie information to reveal sensitive information or take state-changing actions. A strict separation between content provided by unrelated sites must be maintained on the client-side to prevent the loss of data confidentiality or integrity. It is very important to remember that the same-origin policy applies only to scripts. This means that resources such as images, CSS, and dynamically-loaded scripts, can be accessed across origins via the corresponding HTML tags[2] (with fonts being a notable exception[3]).
Cross site request forgery attacks take advantage of the fact that the same origin policy does not apply to HTML tags. History[edit] The concept of same-origin policy dates back to Netscape Navigator 2 in 1995. DVWA - Damn Vulnerable Web Application. Code injection. Injection de code. Cross-origin resource sharing. Mechanism to request restricted resources from another domain CORS defines a way in which a browser and server can interact to determine whether or not it is safe to allow the cross-origin request.[3] It allows for more freedom and functionality than purely same-origin requests, but is more secure than simply allowing all cross-origin requests. The specification for CORS was originally published as a W3C Recommendation[4] but that document is obsolete.[5] The current actively-maintained specification that defines CORS is WHATWG's Fetch Living Standard.[6] How CORS works[edit] The CORS standard describes new HTTP headers which provide browsers a way to request remote URLs only when they have permission.
Although some validation and authorization can be performed by the server, it is generally the browser's responsibility to support these headers and honor the restrictions they impose. Simple example[edit] Preflight example[edit] OPTIONS / Host: service.example.com Origin: OPTIONS - HTTP. The HTTP OPTIONS method is used to describe the communication options for the target resource. The client can specify a URL for the OPTIONS method, or an asterisk (*) to refer to the entire server. Syntax OPTIONS /index.html HTTP/1.1 OPTIONS * HTTP/1.1 Examples Identifying allowed request methods To find out which request methods a server supports, one can use curl and issue an OPTIONS request: Cipherli.st - Strong Ciphers for Apache, nginx and Lighttpd. Anti-CSRF Tokens to prevent Cross Site Request Forgery (CSRF) Anti CSRF Tokens ASP.NET. In short, CSRF abuses the trust relationship between browser and server. This means that anything that a server uses in order to establish trust with a browser (e.g., cookies, but also HTTP/Windows Authentication) is exactly what allows CSRF to take place - but this only the first piece for a successful CSRF attack.
The second piece is a web form or request which contains parameters predictable enough that an attacker could craft his own malicious form/request which, in turn, would be successfully accepted by the target service. Then, usually through social engineering or XSS, the victim would trigger that malicious form/request submission while authenticated to the legitimate service. This is where the browser/server trust is exploited. In order to prevent CSRF in ASP.NET, anti-forgery tokens (also known as request verification tokens) must be utilized. X-Frame-Options - HTTP. The X-Frame-Options HTTP response header can be used to indicate whether or not a browser should be allowed to render a page in a <frame>, <iframe>, <embed> or <object>.
Sites can use this to avoid clickjacking attacks, by ensuring that their content is not embedded into other sites. The added security is only provided if the user accessing the document is using a browser supporting X-Frame-Options. The Content-Security-Policy HTTP header has a frame-ancestors directive which obsoletes this header for supporting browsers. Syntax. Content Security Policy (CSP) - HTTP. Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks.
These attacks are used for everything from data theft to site defacement to distribution of malware. CSP is designed to be fully backward compatible (except CSP version 2 where there are some explicitly-mentioned inconsistencies in backward compatibility; more details here section 1.1). Browsers that don't support it still work with servers that implement it, and vice-versa: browsers that don't support CSP simply ignore it, functioning as usual, defaulting to the standard same-origin policy for web content. If the site doesn't offer the CSP header, browsers likewise use the standard same-origin policy.
Android dev tools Helper.