

Remember that Citadel bank-slurping malware? Its main man was just jailed for five years.
"TorrentLocker" Malware Combines Elements From CryptoLocker, CryptoWall. A new piece of ransomware analyzed by researchers from iSIGHT Partners uses visual components borrowed from CryptoLocker and CryptoWall.
Syrian Malware Attacks Evolving in Sophistication: Kaspersky Lab. New research from Kaspersky Lab shows that cyber-attack activity involving Syria is stepping up in terms of both sophistication and organization.
The latest malware attacks have infected more than 10,000 users, with some files downloaded more than 2,000 times. The victims of these attacks are distributed around the globe, with countries such as Turkey, Saudi Arabia, Lebanon and Palestine also being hit by the attackers. The United Arab Emirates, Israel, Morocco, France and the United States have also been hit with attacks. Bad Actors rebuild from scratch the Gameover Zeus Botnet. Recently law enforcement agencies have taken down the GameOver Zeus botnet with a multinational effort, but a few weeks later, researchers at Seculert spotted a new variant in the wild, which implements a domain generation algorithm.Investigators from FBI and Europol coordinated their activities to seize servers and domains used by bad actors, that authorities discovered was also used to distribute CryptoLocker ransomware.
Experts at Seculert noticed that the DGA scheme allowed the botnet to pass from 1,000 new bots a week, to 1,000 a day on average. According to experts at Arbor networks, cybercriminals behind the malicious infrastructure have renewed it. Ukrainian Hackers Claim Attack on Polish Websites. WARSAW - Ukrainian hackers hostile to the government claimed Thursday to have launched a cyber attack against the websites of Poland's presidency and the Warsaw Stock Exchange.
The hacker group Cyber Berkut said it blocked the sites, both down on Thursday afternoon, in response to what it said were Poland's actions as "sponsors of fascism in Ukraine". "Our western neighbour on orders from Washington renders political, diplomatic and military assistance to nationalists and oligarchs who destabilise and wreck Ukraine," the group alleged on its website. They accused Poland of sending mercenaries to Ukraine, allegations already levelled by Moscow and firmly denied by Warsaw.
Named after "Berkut", the now-disbanded Ukrainian riot police unit used against pro-West protesters earlier this year in Kiev, the group has a history of unleashing virtual warfare over the country's crisis. SynoLocker Trojan crime gang: We QUIT this gig. Boost IT visibility and business value A ransomware Trojan gang appears to be moving on, and has offered to sell its remaining decryption keys in bulk for 200 BTC ($103,000, £61,500).
Cybercrooks behind the recent SynoLocker Trojan – which targets the network attached storage devices manufactured by Synology – have apparently decided to cash out on their ill-gotten gains. The ransomware encrypted users' files before demanding a payment for a private key necessary to unscramble them. The process, akin to a bank selling off bad debt in the world of legitimate business, was discovered by security researchers at F-Secure. Ukrainian Hackers Claim Attack on Polish Websites. New Citadel variant includes different remote management tools. Researchers at IBM discovered a new variant of the Citadel banking malware which includes a new interesting feature that allows attackers to maintain persistence in the victim’s machine through remote management tools.
Citadel is directly derived from the popular Zeus banking Trojan, in June 2013 Microsoft and the FBI carried out takedowns that eradicated more than 1,400 botnets (nearly 88% of overall Citadel botnet) associated with this malware. The new variant of Citadel detected by the experts is integrated with VNC and other remote management tools exploited by the attackers to remotely control victim machines, even after the malware has been detected and removed.
The choice of a remote management tool is not casual, because applications like VNC allows attackers to avoid detection of defense systems that usually don’t block them. The experts also detailed the commands that this variant of Citadel executes: Pierluigi Paganini Security Affairs – (malware, Citadel) New Ransomware Uses GnuPG to Encrypt Files. Security companies have come across a new piece of ransomware that's designed to encrypt files on infected computers.
What's interesting about this threat is that it's easy to update and it uses open source software to encrypt files. Ransomware attack hits Synology's NAS boxen. The essential guide to IT transformation Synology Diskstations and Rackstations are being hit by malware dubbed Synolocker.
The malware is a similar to the infamous Cryptolocker ransomware in that it encrypts all your files and then demands a ransom to unlock them. Analysis of the Stuxnet Cyber Weapon Family and Dragonfly. The progenitor of Duqu, Flame and Gauss are reported as the authors of STUXNET.
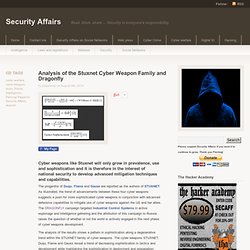
As illustrated, the trend of advancements between these four cyber weapons suggests a push for more sophisticated cyber weapons in conjunction with advanced defensive capabilities to mitigate use of cyber weapons against the US and her allies. The DRAGONFLY campaign targeted Industrial Control Systems in active espionage and intelligence gathering and the attribution of this campaign to Russia raises the question of whether or not the world is actively engaged in the next phase of cyber weapons development.
EXPOSED: Massive mobile malware network used by cops globally. Integrated tiered storage for Big Data and HPC A probe by Citizen Lab at the University of Toronto and computer security firm Kaspersky Lab has uncovered a massive network of mobile malware for all phone types that is sold by an Italian firm to police forces around the world.
The malware, dubbed Remote Control System (RCS), was produced by a company called Hacking Team. It can subvert Android, iOS, Windows Mobile, Symbian and BlackBerry devices. Gameover/Zeus. Nemanja, a botnet of thousand POSs, Grocery Management and Accounting Systems.
Kaspersky Lab Investigating 'Extremely Sophisticated Malware' “The Mask” Leverages High-end Exploits and Packs Bootkit and Rootkit With Mac OS X and Linux Versions Kasperky Lab said on Monday that it has been investigating a sophisticated cyber-espionage operation that it is calling “one of the most advanced threats at the moment”.
“During the past months we have been busy analyzing yet another sophisticated cyberespionage operation which has been going on at least since 2007, infecting victims in 27 countries,” the company wrote in a post to its Securelist blog. “We deemed this operation ‘The Mask” for reasons to be explained later.”
According to Kaspersky, the advanced malware leverages high-end exploits, and includes a bootkit and rootkit, and also has versions for Mac OS and Linux. Interestingly, researchers also found that the malware packs a customized attack specifically against Kaspersky’s security software. New crimekit Atrax exploits Tor, mines Bitcoin and much more. Atrax is the name of the last crimekit that is sold in the underground market, its particularity is the capability to exploit Tor networks to communicate with Command & Control infrastructure.
Jonas Mønsted of the Danish security firm CSIS, published a blog post that describes in depth the crimekit. Symantec Warns of Apache Tomcat Server Worm. Apache Tomcat Server Backdoor Worm Squirming Malware hunters at Symantec have intercepted a malicious backdoor worming its way though servers running the open-source Apache Tomcat servers.
Attackers Hide Communication With Linux Backdoor. Linux backdoor Fokirtor implements covert communication protocol. In May sophisticated attackers breached a large Internet hosting provider and gained access to internal administrative systems using a singular Linux backdoor. Assessing the impact of the Blackhole arrests. Early yesterday, a 'breaking news' tweet grabbed the attention of most security researchers involved with malware today. Sophisticated Hacker-for-Hire Gang 'Hidden Lynx' Strikes Organizations Worldwide. Securo-boffins link HIRED GUN hackers to Aurora, Bit9 megahacks.
Security researchers have linked the “Hackers for hire” Hidden Lynx Group with a number of high-profile attacks, including an assault on net security firm Bit9, as well as the notorious Operation Aurora assault against Google and other hi-tech firms back in 2009. Caphaw Financial Malware Surge Hits Customers of 24 Major Banks. New ransomware strain forces hapless users into becoming Bitcoin miners. Syrian Electronic Army attacked most major Qatar websites. The Syrian Electronic Army (SEA) has hit a new series of targets in a large hacking campaign against high profile Qatar based websites. The Syrian Electronic Army is considered one of the most active and dangerous group of hacktivists due the large number of high profile companies and government entities it has attacked with success, including Facebook, Twitter, Google, The Financial Times, The Guardian, the Associated Press, Aljazeera, numerous Government and Military websites and The White House.
Android Wroba banking trojan targeted Korean users. The Antivirus vendor Malwarebytes revealed that the Wroba banking trojan distributed via file sharing sites and alternative markets targeted Korean users. Citadel botnet resurges to storm Japanese PCs. Security intelligence for a faster world. Reach of 'Hand of Thief' Banking Trojan Exceeds Grasp: RSA.
TOR. Poison Ivy still alive, old malware new cyber threats - FireEye report. NetTraveler APT hackers still active improved their attacks. Hesperbot. Sophisticated Android Trojan Spreads Through Mobile Botnet. Cybercrime - Al Assam Alaikum directly linked to Russian Business Network. Koobface worm-flinging gangster linked to pharma spam ops. New Backdoor Family Being Installed via Java Exploit: Trend Micro.
Advanced malware logs Skype calls, steals files from removable drives. How the Qbot malware downed Melbourne Health's systems - Security - iTnews. "Gooligan" Android Malware Steals Authentication Tokens to Hack User Accounts. Cash-spitting ATM malware blamed on Cobalt hacking gang. Vigilante IoT worm Hajime hits Australia - Security - iTnews. Following the Money Hobbled vDOS Attack-for-Hire Service.