

Cisco Quick Tips. IOS Configuration Fundamentals Command Reference. Configure and test Telnet on a Cisco router or switch. Telnet is a remote connection protocol known to be active on port 23.
It can be used to administrate a Cisco IOS powered device over the network. This article will demonstrate the necessary commands to configure Telnet. Cisco 871 (cisco871-SEC-K9) DHCP Client list. - Cisco. Ramblings o' Techie: Disable DHCP on a Cisco router or wireless access point. DHCP Binding in IOS: Entries under DHCP client-id/hardware address. The string under the DHCP client-id/hardware address represents the ASCII equivalent of the client identifier.
See the output of 'show ip DHCP bindings' on a router operating as a DHCP server: This string represents the ASCII equivalent of the client identifier. How to Configure DHCP on a Cisco Router. This tutorial will walk you through configuring a Cisco Router to server as a DHCP server for client computers. 1.
Define the DHCP address pool, Router(config)#ip dhcp pool POOLNAME Router(dhcp-config)#network XXX.XXX.XXX.XXX YYY.YYY.YYY.YYY. LAN switching Basics. Licensing information for ISR-G2. The Cisco ISR 1900, 2900 and 3900 Series adopt the Universal IOS image model enabling customers to future proof their networks.
Universal IOS Packaging Overview: As we all know that for ISR-G2 we have to enable licenses to use the feature instead of using IOS images. The Universal IOS image is loaded by Cisco manufacturing on all shipped routers. IOS Universal Image contains all IOS features. Feature sets in the universal image are unlocked using licensing keys i.e. the level of IOS functionality available is determined by the license applied to the device. IPBase, DATA, UC (Unified Communications) and SEC (Security) technology packages are enabled in the universal image via Cisco Software Activation licensing keys. And you can also get this information by command: “show license udi” FabricPath: Cisco’s New Technology of Extending Layer 2 Network Without Spanning Tree. The traditional Ethernet network designs require termination of the Layer 2 Network at Aggregation or Core layer to limit the fault isolation and broadcast domain due to spanning tree.
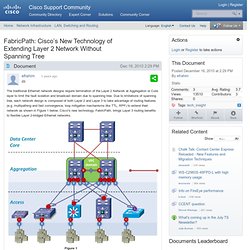
Due to limitations of spanning tree, each network design is composed of both Layer 2 and Layer 3 to take advantage of routing features (e.g. multipathing and fast convergence, loop mitigation mechanisms like TTL, RPF) to extend their network as shown in Figure 1 below. VLSM. Introduction to Border Gateway Protocol (BGP) By Sean Wilkins - October 29, 2012 Cisco Border Gateway Protocol (BGP) is a complex topic that often overwhelms those just getting into the network arena.
It also can be a confusing topic to cover, especially because it differs from many of the well-known routing protocols being used on most internal networks. Routing Protocol Selection Guide - IGRP, EIGRP, OSPF, IS-IS, BGP. Overview The purpose of routing protocols is to learn of available routes that exist on the enterprise network, build routing tables and make routing decisions.
Some of the most common routing protocols include IGRP, EIGRP, OSPF, IS-IS and BGP. There are two primary routing protocol types although many different routing protocols defined with those two types. Link state and distance vector protocols comprise the primary types. Configuring Privilege levels in Cisco IOS. It is possible to change the privilege level of “show run” and assign it to something other than level 15.
You can change the privilege level but you are likely to be surprised at the result when you do. A person executing “show run” can only see things that they have the ability to change. So someone executing the command at privilege level 8 would not have the ability to change anything and basically would see only an empty configuration. Refer the document IOS Privilege Levels Cannot See Complete Running Configuration for more information.
IPv6 features concepts and configurations. How to configure Cisco Router with IPv6 In this tutorial I will configure Cisco router with transition method discussed in previous article.

Dual Stacking This is the most common type of migration strategy because, it's the easiest on us—it allows our devices to communicate using either IPv4 or IPv6. Dual stacking lets you upgrade your devices and applications on the network one at a time. As more and more hosts and devices on the network are upgraded, more of your communication will happen over IPv6, and after you've arrived—everything's running on IPv6, and you get to remove all the old IPv4 protocol stacks you no longer need. Guide to Cisco Router Configuration. Preface and Scope This document is intended to instruct in the basics of Cisco router configuration and maintenance.

It is by no means complete or authoritative. This document purposely omits many topics and assumes a foreknowledge of others. It is assumed that the reader has a preexisting knowledge of Internet protocols and an understanding of TCP/IP networking. Top 10 Cisco IOS Configuration Mistakes. By Sean Wilkins - February 18, 2013. Configuring the Router - Basic Router Configuration [Cisco 1900 Series Integrated Services Routers. IOS IP Command Reference, Volume 2 of 3: Routing Protocols, Release 12.2 - RIP Commands [Cisco IOS Software Releases 12.2 Mainline. Introducing Kvasir. Cisco’s Advanced Services has been performing penetration tests for our customers since the acquisition of the Wheel Group in 1998. We call them Security Posture Assessments, or SPA for short, and I’ve been pen testing for just about as long. I’ll let you in on a little secret about penetration testing: it gets messy!
During our typical assessments we may analyze anywhere between 2,000 and 10,000 hosts for vulnerabilities, perform various exploitation methods such as account enumeration and password attempts, buffer/stack overflows, administrative bypasses, and others. We then have to collect and document our results within the one or two weeks we are on site and prepare a report. How can anyone keep track of all this data, let alone work together as a team? The answer is to build a data management application that works for you. Welcome to the 21st Century. Show IP access lists attached to an interface. What is NVI0 interface on router. Configure Cisco Router with ip-helper for redundant/failover MS DHCP servers. Configuring SNMP Support. MIBs and RFCs MIB modules typically are defined in RFC documents submitted to the Internet Engineering Task Force (IETF), an international standards body. RFCs are written by individuals or groups for consideration by the Internet Society and the Internet community as a whole, usually with the intention of establishing a recommended Internet standard.
Before being given RFC status, recommendations are published as Internet Draft (I-D) documents. RFCs that have become recommended standards are also labeled as standards (STD) documents. You can learn about the standards process and the activities of the IETF at the Internet Society website at You can read the full text of all RFCs, I-Ds, and STDs referenced in Cisco documentation at the IETF website at The Cisco implementation of SNMP uses the definitions of MIB II variables described in RFC 1213 and definitions of SNMP traps described in RFC 1215.