

NSA compromised more than 50000 networks with malware. How NSA tries to compromise Tor anonymity. Tor Stinks document. Top-secret presentation Tor Stinks leaked by Snowden shows the techniques implemented by the NSA to overwhelm Tor Anonymity with manual analysis.
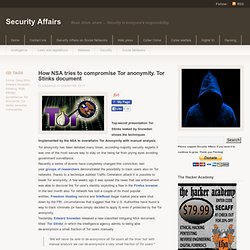
Tor anonymity has been debated many times, according majority security experts it was one of the most secure way to stay on line being far from prying eyes avoiding government surveillance. Recently a series of events have completely changed this conviction, last year groups of researchers demonstrated the possibility to track users also on Tor networks, thanks to a technique dubbed Traffic Correlation attack it is possible to break Tor anonymity. How The NSA Deploys Malware: An In-Depth Look at the New Revelations. Article by Dan Auerbach.
NSA tactics no better than a CYBERCRIME GANG, says infosec'er. Mid East undersea fibre telco hacked: US, UK spooks in spotlight. Belgian telco Belgacom - which operates vital undersea communications cables - says its internal network was compromised, possibly by foreign spooks.
Phone and data connections from international hot spots, such as Syria and Yemen, pass through submarine fibre lines handled by Belgacom International Carrier Services (BICS). Security experts suspect the Belgian biz was infiltrated by state-backed hackers - and NSA and GCHQ have emerged as the prime suspects. Journalists in Belgium - writing here, here, here, and here - cite sources who reckon Belgacom’s systems may have been compromised for two years by a foreign intelligence agency. Well-known security researcher Eddy Willems of antivirus biz G Data told El Reg that Belgacom admitted on TV that 5,000 of its internal machines were infected with sophisticated malware, which may have cyber-espionage purposes.
NSA tried to insert backdoor into Linux. Linux Torvalds during last LinixCon admitted to have received pressure from US Intelligence to insert a backdoor into Linux.
Linux Torvalds during a question-and-answer session at the LinuxCon publicly admitted that the US Government requested him to insert a backdoor into Linux kernel. The circumstance must induce a reflection in all those experts that believe open source software is the unique possible reply to elude surveillance programs such as PRISM and BullRun. Torvalds, considered the father of Linux kernel, attended the Linuxcon conference in New Orleans today with other top Linux developers, he replied to question on his OS, Microsoft, and other issues related to the events occurred in the last months. So, Linus Torvalds: Did US spooks demand a backdoor in Linux? 'Yes' Linux supremo Linus Torvalds has jokingly admitted US spooks approached him to put a backdoor in his open-source operating system.
During a question-and-answer session at the LinuxCon gathering in New Orleans this week, Torvalds and his fellow kernel programmers were asked by moderator Ric Wheeler whether America's g-men leaned on the Finn to compromise Linux's security, allowing spies to infiltrate computers. Torvalds replied with a firm "no" while nodding his head to say yes, a response greeted with laughter from the audience. He quickly followed up by repeating "no" while shaking his head in the negative. South Korean Red Hat developer Tejun Heo, sitting alongside the kernel boss, quipped: "Not that I can talk about.
" Linus Torvalds Admits He's Been Asked To Insert Backdoor Into Linux. Leaked docs: NSA 'Follow the money' team slurped BANK records, CREDIT CARD data. The NSA doesn't only hoover up your emails, web surfing habits and phone call metadata – they also harvest your credit card records and banking transactions.
The latest leaks from whistleblower Edward Snowden reveal that the NSA is monitoring international banking and credit card transactions that pass through the Society for Worldwide Interbank Financial Telecommunication (SWIFT) as well as the systems of several companies, including Visa. Anyone who has tried to transfer money between two countries will know that the SWIFT network is used by more than 8,000 banking institutions in over 200 countries to "securely" send their customers' transaction information.
According to the leaked documents, the aptly named "Follow The Money" 1 NSA team takes a lead in monitoring international financial transactions, German news magazine Der Spiegel reports. Only 180 million records? FBI spooks use MALWARE to spy on suspects' Android mobes - report. 2013 Cost of Cyber Crime study The Federal Bureau of Investigation is using mobile malware to infect, and control, suspects' Android handsets, allowing it to record nearby sounds and copy data without physical access to the devices.
'Black budget' Shows CIA Swells in Size. WASHINGTON - The CIA has mushroomed into the largest US spy agency with a nearly $15 billion budget as it expands intelligence, cyber sabotage and overseas covert operations, secret leaked documents showed Thursday.
Former National Security Agency contractor Edward Snowden leaked the government's "black budget" for fiscal year 2013 to The Washington Post, which published portions of the top-secret document online in the latest in a series of revelations that have put the US intelligence community under a spotlight. NSA spooks tooled up with zero-day PC security exploits from the FRENCH. The NSA bought specialist computer hacking tools and research from French security outfit Vupen, according to documents unearthed using the Freedom of Information Act.
A contract shows the American spooks paid for a year's supply of zero-day vulnerability information and the software needed to exploit those flaws to attack electronic systems. The paperwork, obtained by government transparency and accountability site MuckRock, show that the US intelligence nerve-centre signed up to a one-year subscription to Vupen's “binary analysis and exploits service” last September. Vupen prides itself on advanced vulnerability research as well as selling software exploits for unpatched flaws in systems - known as zero-days - to governments. Several US defence contractors and security startups, such as Endgame Systems, are also in the business of privately researching and selling information about software vulnerabilities and associated attack code. NSA Bought Exploit Service From VUPEN.
Trove of NSA Documents and FISC Opinions Declassified Thanks to EFF Lawsuit. NSA Documents Show Spy Agency Violated Privacy Rules. Declassified documents show NSA staff abused tapping, misled courts. High performance access to file storage The US Office of the Director of National Intelligence (ODNI) has declassified 1,800 pages of documents that indicate that the NSA routinely overstepped its authority and misled oversight bodies about the surveillance of US citizens.
"In June of this year, President Obama directed me to declassify and make public as much information as possible about certain sensitive intelligence collection programs undertaken under the authority of the Foreign Intelligence Surveillance Act (FISA) while being mindful of the need to protect national security," said James Clapper, director of national intelligence in a Tumblr posting. "These documents were properly classified, and their declassification is not done lightly. That earth-shattering NSA crypto-cracking: Have spooks smashed RC4? Midsize businesses face enterprise-caliber threats Analysis Fresh revelations from whistleblower Edward Snowden suggest that the NSA can crack TLS/SSL connections, the widespread technology securing HTTPS websites and virtual private networks (VPNs).
Although reports from the New York Times and its allied publications held off on the specifics, it may all mean that US spooks can reliably crack RC4, a popular encryption cipher, security experts fear. As reported last night, the NSA and GCHQ are able to foil basic safeguards that supposedly ensure privacy on the web, allowing spooks to peek inside the encrypted contents of VPN traffic, online banking and shopping, and more. US, British Spy Agencies Crack Web Encryption: Reports. WASHINGTON - US and British intelligence agencies have cracked the encryption that secures a wide range of online communications including emails, banking transactions and phone conversations, according to newly leaked documents. The documents provided by former US intelligence contractor Edward Snowden to The New York Times, ProPublica and The Guardian suggest that the spy agencies are able to decipher data even with the supposedly secure encryption to make it private.
The US National Security Agency, working with its British counterpart, GCHQ, accomplished the feat by using supercomputers, court orders, and some cooperation from technology companies, the documents indicate. If the reports are accurate, the highly secretive program would defeat much of the protection that is used to keep data secure and private on the Internet, from emails to chats to communications using smartphones. NSA’s pipe dream: Weakening crypto will only help the “good guys” Ever since Edward Snowden began leaking National Security Agency (NSA) secrets earlier this year, President Obama has insisted that they weren't "whistle blowing" in any useful sense because they didn't reveal any abuses.
Instead, they simply revealed secret programs that were: Operating with rigorous NSA oversight and without real problems;Extensively vetted by the secret Foreign Intelligence Surveillance Court (FISC);In compliance with US law, which didn't need any significant changes; andGenerally speaking, a good idea. For instance, here was Obama at an August 9 press conference at the White House, answering a couple of questions from journalists about the NSA's programs. Gizmodo. NSA Bullrun program, encryption and false perception of security. The latest nightmare for US Administration is named Bullrun, another US program for massive surveillance. Snowden‘s revelations represented a heartquake for IT security, the image of NSA and US IT companies are seriously compromised such the trust of worldwide consumers. Obama Promised Answers on Spying by Wednesday: Brazil.
BRASÍLIA - US President Barack Obama has promised answers by Wednesday to allegations of US spying on Brazil's President Dilma Rousseff, her government said Friday. Surveillance - NSA can access data on your mobile device. NSA: From Security Provider To Cell Phone Tracker - Infographic. An Educated Guess About How the NSA Is Structured - Marc Ambinder. Want to understand how an organism really works? Take a look at its plumbing.