

CISCO GRE AND IPSEC - GRE OVER IPSEC - SELECTING AND CONFIGURING GRE IPSEC TUNNEL OR TRANSPORT MODE. GRE Tunnels are very common amongst VPN implementations thanks to their simplicity and ease of configuration.
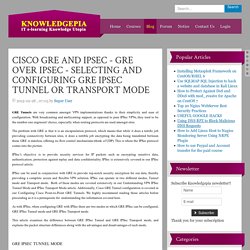
With broadcasting and multicasting support, as opposed to pure IPSec VPNs, they tend to be the number one engineers' choice, especially when routing protocols are used amongst sites. The problem with GRE is that it is an encapsulation protocol, which means that while it does a terrific job providing connectivity between sites, it does a terrible job encrypting the data being transferred between them. GRE is stateless, offering no flow control mechanisms (think of UDP). This is where the IPSec protocol comes into the picture. Pptp or l2tp - خرید vpn. Protocol: PPTP/L2TP/IPSec/OpenVPN/SSTP/SoftEther. To download these tutorials for OFFLINE viewing or for archive purposes please (Click here to download) (Clicking the “.zip” will open the Archive, un-zip the .mht files then use one of the plugins below to view them) You can open .mht WebArchive files directly inside FireFox Or Google Chrome by installing a plugin Different types of VPN Protocol Explained.

Below is all the different types of protocol that most VPN services offer in their packages. Most only support PPTP/OpenVPN but recently alot of services have added IPSec/SoftEther. We are going to give a detail of what these different Protocols do, and why they are used. The Point-to-Point Tunneling Protocol (PPTP) is a method for implementing virtual private networks. The PPTP specification does not describe encryption or authentication features and relies on the Point-to-Point Protocol being tunneled to implement security functionality. A PPTP tunnel is instantiated by communication to the peer on TCP port 1723. Implementations. PPTP vs L2TP vs OpenVPN vs SSTP vs IKEv2 - BestVPN.com. With Edward Snowden’s shocking revelations that the NSA has for years been working to crack and subvert VPN encryption technologies, together with the fact that it is becoming increasingly obvious that most such technologies have been developed and certified by the US government’s National Institute of Standards and Technology (NIST) and may therefore be considered suspect, we have decided it is time to revisit and update this popular article.
We will start with a rundown of the major differences between the different VPN protocols and how they affect you, before looking in more detail at the key concepts involved in cryptography, and how the NSA’s assault on encryption standards affects VPN users. The discussion below is rather technical, and although I have made every effort to make it as approachable as possible, you may prefer to just jump to the end of the article for a quick summary. Pros Client built-in to just about all platformsVery easy to set upFast Cons. Webinar SSL English. SSL versus TLS - What's the difference? - HIPAA News, Web & Email Security Tips & News - Plus More. SSL versus TLS TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are protocols that provide data encryption and authentication between applications and servers in scenarios where that data is being sent across an insecure network, such as checking your email (How does the Secure Socket Layer work?).
The terms SSL and TLS are often used interchangeably or in conjunction with each other (TLS/SSL), but one is in fact the predecessor of the other — SSL 3.0 served as the basis for TLS 1.0 which, as a result, is sometimes referred to as SSL 3.1. With this said though, is there actually a practical difference between the two? See also our Infographic which summarizes these differences. SSL vs TLS: What is the Difference? An Infographic. SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are foundations of security on the Internet.
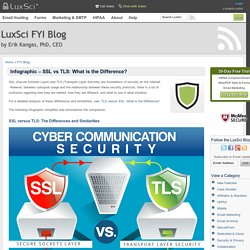
However, between colloquial usage and the relationship between these security protocols, there is a lot of confusion regarding how they are related, how they are different, and what to use in what situation. For a detailed analysis of these differences and similarities, see: TLS versus SSL: What is the Difference? The following infographic simplifies and summarizes the comparison. Elastix, TLS, SRTP y OpenVPN. Transport Layer Protection Cheat Sheet. Last revision (mm/dd/yy): 09/29/2018 This cheat sheet provides a simple model to follow when implementing transport layer protection for an application.
Although the concept of SSL is known to many, the actual details and security specific decisions of implementation are often poorly understood and frequently result in insecure deployments. This article establishes clear rules which provide guidance on securely designing and configuring transport layer security for an application. This article is focused on the use of SSL/TLS between a web application and a web browser, but we also encourage the use of SSL/TLS or other network encryption technologies, such as VPN, on back end and other non-browser based connections.
Architectural Decision An architectural decision must be made to determine the appropriate method to protect data when it is being transmitted. TLS is mainly a defence against man-in-the-middle attacks. Benefits Basic Requirements SSL vs. Cryptomodule Parts and Operation 1. 2.