

Nvidia RTX 3060 vs. 3060 Ti vs. 3070. The RTX 3060 Ti, 3070, and recently released 3060 all target the upper-midrange price bracket, delivering excellent performance for AAA games at 1080p and 1440p.
Gamme de cartes graphiques GeForce RTX 3060. PRISM S-BLACK ATX Mid Tower - Rosewill. Tasty Computers. Custom Built Gaming PC/Computer i9 9900+RTX 2080+32GB+1TB NVME SSD+WiFi HOT SALE. TechPowerUp GPU Database. Graphics Processor Polaris 20 Cores TMUs ROPs Memory Size Memory Type.
Fix problems that block programs from being installed or removed. The Program Install and Uninstall troubleshooter helps you automatically repair issues when you're blocked from installing or removing programs.

It also fixes corrupted registry keys. First, you'll need to download the troubleshooter. Download troubleshooter If you see the File Download box when you start downloading, select Run or Open. Mifi.no - Mikael Finstad. Mifi/ezshare: Easily share files, folders and clipboard over LAN - Like Google Drive but without internet. Free Image Optimizer - Compress and resize photos.
Custom Gaming Computers, Laptops & Notebooks. (6) Dell Inspiron 5675 Gaming Desktop Review. Screen Capture Studio. View topic - How to move a clip frame by frame. DuckDuckGo — Privacy, simplified. IconViewer. How to Extract an Icon from a Windows EXE File. Sometimes you’re working on a project and need access to a high-quality version of a Windows 10 application icon, but you can’t find one on the internet.
Luckily, a free utility called IconViewer makes it easy to extract a high-quality icon from an application’s EXE file. Here’s how. First, download IconViewer from the developer’s website and install it. It’s important to note that IconViewer doesn’t run in a standalone program window. Instead, it adds a special tab to a file’s Properties window that lets you view and extract a program’s icon of your choice. For IconViewer to work, you need to have direct access to the EXE file of the application you’d like to extract an icon from. Otherwise, you can usually find an application’s EXE file in sub-folders of C:\Program Files or C:\Program Files (x86). When you’ve found the application’s EXE file, right-click it and select “Properties.”
In the Properties window, click the “Icons” tab. Then click “Save.” WD easystore 14TB External USB 3.0 Hard Drive Black WDBCKA0140HBK-NESN. Why does my hard drive report less capacity than indicated on the drive's label? Explains why a hard drive's capacity often appears to be less than advertised when displaying in Windows or Mac operating systems.
Hard drive manufacturers market drives in terms of decimal (base 10) capacity. In decimal notation, one megabyte (MB) is equal to 1,000,000 bytes, one gigabyte (GB) is equal to 1,000,000,000 bytes, and one terabyte (TB) is equal to 1,000,000,000,000 bytes. Programs such as FDISK, system BIOS, Windows, and older versions of macOS use the binary (base 2) numbering system. SatelliteGuys.US. Your step-by-step guide to repairing Windows 10. Though it's showing itself to be a good operating system (in line with Windows XP and Windows 7), sometimes a Windows 10 system will start misbehaving to the point where repair is needed.

This often takes the form of worsening performance or stability and can originate from damage to or loss or corruption of Windows system files typically found in the C:\Windows folder hierarchy. When that happens, users would be well advised to break out the following routine to help them set things back to rights. The Windows (10) repair drill Most of these approaches work with earlier versions of Windows (that is Windows 7 and 8) but the advice here focuses on Microsoft's latest and greatest desktop OS — Windows 10.
The idea is to first try the initial step in the sequence. The amount of time and effort required for each step goes up incrementally. Download Windows 10. Create Windows boot flash drive. PREDATOR Security Software. PREDATOR locks your PC when you are away, even if your Windows session is still active.

It uses a regular USB flash drive as an access control device, and works as follows: you insert the USB drive you run PREDATOR (autostart with Windows is possible) you do your work... when you're away from your PC, you simply remove the USB drive: - once it is removed, the keyboard and mouse are disabled and the screen darkens when you return back to your PC, you put the USB flash drive in place: - keyboard and mouse are immediately released, and the display is restored. PREDATOR helps to limit the time your kids spend on their computers: you define the times of day when each user may access the computer with the built-in scheduler you can make specific rules for each user and each day of the week out of authorized periods you can either lock the desktop, logoff the user or shutdown the computer ; or you can remove the flash drive to disable the computer for good. Watch a short demo video of PREDATOR: 10 best ways to use a flash drive or USB.
SLC vs MLC vs TLC NAND Flash. The underlying NAND architecture of SSDs can vary from model to model and this article will explore those differences.
Each of the various types of NAND flash – SLC, MLC, eMLC and TLC – have different characteristics that influence which is best for your business storage. Flash – in all its forms – has revolutionized enterprise data storage. Compared to HDDs, SSDs packing enable storage subsystems and arrays to provide blistering application performance and make short work out of business analytics and other workloads. In PCs and mobile devices, flash memory enables brisk boot times, snappy application start times and fast data transfers. And since flash storage lacks moving parts, SSDs aren't nearly as susceptible to damage from abrupt movements and physical shocks.
If you're in the market for a flash array, see our list of the best flash storage array vendors. The results of the Enterprise Storage Forum survey, Data Storage Trends 2018, provides insight into flash in the enterprise. How to Run Windows 10 From a USB Drive. Silicon Dies: Explaining OC Editions & the Bin-Out Process - CPUs, RAM, GPUs. Toward the final steps of silicon fabrication, individual dies and NAND Flash modules are tested for frequency and voltage tolerance, among other things; the stability (or volatility) of the silicon chip is gauged within a spec range, then the factory bins-out the chip for use in specific product lines.
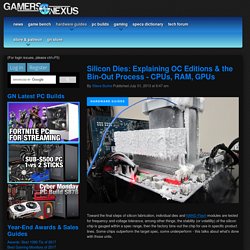
Some chips outperform the target spec, some underperform - this talks about what's done with those units. This article will discuss the process of binning-out silicon dies and Flash modules for use in your hardware. Download H2testw 1.4. Maybe you've bought a new storage unit and want to see if it's really up to the specs on the package, or perhaps you want to test an older storage device for errors and didn't know what to use.
H2testw is a simple tool that is distributed for free, does not require installation and offers a very simple, easy-to-use interface. The program can be used by anyone who wants to know how their product compares to others, or the amount of errors that can be detected on their device. Scan nearly all types of storage devices A cool feature of the program is that it offers you the possibility to choose the amount of data you want to scan.
You'll be able to scan the whole device or an exact amount of data, all with the help of a simple mouse click. Although, it is mainly aimed at USB devices, the program can also be used to scan hard disks (internal or external), network volumes or memory cards. Offering in-depth info on how well the device performs In conclusion. DaVinci Resolve 16. Blackmagic eGPU. - Free Logo Generator.