

Hybrid IPSec-MPLS VPNs: What They Are and When They Make Sense. In a recent post I wrote about MPLS VPNs, and how they’re a step up from VPNs based on IPSec.
That post ended with this paragraph: It’s also possible to use a mix of both IPSec and MPLS VPNs in a hybrid configuration. Smaller sites, for example, may feed in to the MPLS VPN via IPSec connections, enabling companies to use the service that makes the most sense for each location. In this post I thought I’d dive a little deeper into what a hybrid VPN is and the circumstances where it makes the most sense. Enterprise Branch Security Design Guide. Brocade%20remote%20connection. Collabpa.pdf. Your Network's Next Step: Cisco ACI Or VMware NSX. When it comes to SDN, Cisco's Application Centric Infrastructure and VMware's NSX are often discussed interchangeably, but they are really very different.

Joe Onisick explains how they compare and can even work together. Editor's Note: This article is written by Joe Onisick, an engineer at Cisco who helped develop and works closely with ACI technology. While we recognize that the column may have inherent biases, Joe is known as an authority on this subject, and we feel that he addresses points that are important to our readers. Other subject matter experts interested in contributing technical articles may contact the editors. 01home.pdf. Public Relations PR, Marketing Strategy, Internet Marketing-AlexComms.
Amazon Simple Storage Service (S3) - Online Cloud Storage for Data & Files. Twp-oracledbcloudbackup-130129.pdf. Providing Secure Communication Between Sites Using VPN CloudHub - Amazon Virtual Private Cloud. If you have multiple VPN connections, you can provide secure communication between sites using the AWS VPN CloudHub.
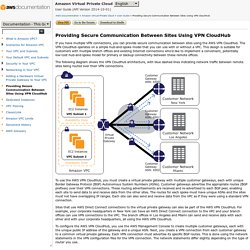
The VPN CloudHub operates on a simple hub-and-spoke model that you can use with or without a VPC. This design is suitable for customers with multiple branch offices and existing Internet connections who'd like to implement a convenient, potentially low-cost hub-and-spoke model for primary or backup connectivity between these remote offices. The following diagram shows the VPN CloudHub architecture, with blue dashed lines indicating network traffic between remote sites being routed over their VPN connections. To use the AWS VPN CloudHub, you must create a virtual private gateway with multiple customer gateways, each with unique Border Gateway Protocol (BGP) Autonomous System Numbers (ASNs). Customer gateways advertise the appropriate routes (BGP prefixes) over their VPN connections. When using an AWS VPN CloudHub, you pay typical Amazon VPC VPN connection rates.
SDN Security Attack Vectors and SDN Hardening. As enterprises look to adopt Software Defined Networking (SDN), the top of mind issue is the concern for security.
Enterprises want to know how SDN products will assure them that their applications, data and infrastructure will not be vulnerable. With the introduction of SDN, new strategies for securing the control plane traffic are needed. This article will review the attack vectors of SDN systems and share ways to secure the SDN-enabled virtualized network infrastructure. This article will then discuss the methods currently being considered to secure SDN deployments. 1. Software-Defined Networking (SDN) is an approach to networking that separates the control plane from the forwarding plane to support virtualization. Error. VMware-Cisco-Virtualizing-Unified-Communications-Solution-Brief.pdf. Cisco Intelligent WAN. vCloud Suite: Infrastructure-as-a-Service (IaaS) & Cloud Computing.
Simplifying management of distributed networks with new model and features « Cisco Meraki Blog. We’ve got exciting news if you’re a current or future Cisco Meraki MX security appliance customer.

First, we’ve got a brand new MX model available for order: the MX100. Second, we’re releasing several new feature enhancements in our next firmware update, scheduled for the end of this calendar year. The biggest of these are: Integrated Sourcefire Snort IPSConfiguration templates for multi-MX environmentsWired splash pagesMPLS to VPN failover These new features provide redundancy and additional management flexibility to organizations with multiple remote sites, and expand the MX’s capabilities in managing BYOD environments. vSphere Documentation Center. Why MPLS VPNs are a step up from traditional VPNs. While the Internet offers a relatively inexpensive way to connect your various business locations and foster communications with employees, partners and even customers, it is also inherently insecure.
For that reason, companies have for years been using virtual private networks (VPNs) to essentially carve a secure tunnel through the Internet. While VPNs based on IPSec dominated the landscape early on, today customers have a choice between VPNs based on IPSec or MPLS. This post will try to shed light on why, for many business use cases, the MPLS version is a better option.
Public vs. private network For starters, IPSec VPNs run across the public Internet. MPLS VPNs, on the other hand, run across a single carrier’s private MPLS network, not the public Internet. Improved connectivity. Securely Connect Your Business - EarthLink Business. Business Internet Plans, Business Internet Prices - Comcast Business. Cisco SPA8800 IP Telephony Gateway with 4 FXS and 4 FXO Ports. Click the arrow to open and close the My Cisco Menu.
The Cisco SPA8800 IP Telephony Gateway is a multipurpose solution that small businesses can use to connect an on-premise IP private branch exchange (PBX) system to the public switched telephone network (PSTN), or connect a legacy time-division multiplexing (TDM) PBX or key system to voice-over-IP (VoIP) services. The Cisco SPA8800 provides a combination of four Foreign eXchange Office (FXO) and four Foreign eXchange Subscriber (FXS) ports to connect to existing analog phones, which helps protect and extend your existing communications equipment investments, too.
The Cisco SPA8800 also has the capability to be configured as an FXO gateway for an Asterisk Open Source PBX providing a versatile solution when conditions favor an external device. Additional features of the Cisco SPA8800 include: User Guides, Release Notes, and Support Information. Phone Home for Free – A Customer Story « Cisco Meraki Blog. Note: The full case study will be featured on our website soon, but here is a sneak peek into how they are using VOIP and the automatic failover mechanisms built into Meraki products to support their business operation.
Based in Perth, Australia, Cash Converters is a pawnbroking franchise company and retailer, with over 700 stores in 21 countries that specialize in the sale of second-hand goods. All of their stores operate on an online point of sale system, making Internet connectivity critical. “We are 100% dependent on the Internet at all times,” Duncalf stressed. To ensure a secure, reliable, and scalable network, each Australian Cash Converters store is equipped with a full Meraki stack, consisting of a Cisco Meraki MX security appliance, MS switch, and MR wireless access point.
The stores use a fully-redundant MPLS network, with traffic spanned across multiple VLANs. All phone calls are now free between distant sites as a result of this network design. vSphere Documentation Center. PacketFence: Open Source NAC (Network Access Control) Hyper-V Comparison – Windows Server 2008 R2 vs Windows Server 2012 - The Irish IT Professional. Catalyst 3560 Software Configuration Guide, Release 12.2(52)SE - Configuring Voice VLAN [Cisco Catalyst 3560 Series Switches] FreeRADIUS: The world's most popular RADIUS Server. Cisco Virtual Wireless Controller - Products & Services. Minimize hardware costs while optimizing wireless network performance with centralized control.
The Virtual Wireless Controller can cost-effectively manage, secure, and optimize the performance of local and branch wireless networks. Ideal for small and medium-sized businesses, the Virtual Wireless Controller facilitates server consolidation and improves business continuity in the face of outages. A component of the Cisco Unified Wireless Network, the Virtual Wireless Controller provides real-time, centralized communications between Cisco Aironet Access Points, the Cisco Prime Infrastructure, and the Cisco Mobility Services Engine Designed for organizations with virtualization initiatives, and for small to medium enterprise deployments, the Virtual Wireless Controller offers: The Virtual Wireless Controller is a part of the complete Wireless Controller family, all offering: Minimize hardware costs while optimizing wireless network performance with centralized control.
EUI-64 in IPv6. By stretch | Monday, August 4, 2008 at 2:13 a.m.
UTC One of IPv6's key benefits over IPv4 is its capability for automatic interface addressing. By implementing the IEEE's 64-bit Extended Unique Identifier (EUI-64) format, a host can automatically assign itself a unique 64-bit IPv6 interface identifier without the need for manual configuration or DHCP. This is accomplished on Ethernet interfaces by referencing the already unique 48-bit MAC address, and reformatting that value to match the EUI-64 specification.
RFC 2373 dictates the conversion process, which can be described as having two steps. Why 0xFFFE? The second step is to invert the universal/local (U/L) flag (bit 7) in the OUI portion of the address. Again, you're probably wondering why this is done. IPv6 EUI-64 Rules With Subinterfaces - The Cisco Learning Network. IPSec Transforms > IPSec Overview Part Two: Modes and Transforms.
ISAKMP Profile Overview. Configuration Guide The ISAKMP profile is an enhancement to Internet Security Association and Key Management Protocol (ISAKMP) configurations. It enables modularity of ISAKMP configuration for phase 1 negotiations. Crypto map based IPsec VPN fundamentals - negotiation and configuration. This document will outline basic negotiation and configuration for crypto-map-based IPsec VPN configuration.
This document is intended as an introduction to certain aspects of IKE and IPsec, it WILL contain certain simplifications and colloquialisms. IPsec is a standard based security architecture for IP hence IP-sec. IKE (Internet Key Exchange) is one of the ways to negotiate IPsec Security Associations (SAs), in particular case ISAKMP (implementation of IKE) is what Cisco uses. Currently two versions of IKE exist: IKE version 1 (IKEv1) - the more common and older, widely deployed. IPsec Troubleshooting: Understanding and Using debug Commands. Introduction This document describes common debug commands used to troubleshoot IPsec issues on both the Cisco IOS® Software and PIX/ASA.
This document assumes you have configured IPsec. Refer to Common IPsec Error Messages and Common IPsec Issues for more details. Refer to Most Common L2L and Remote Access IPsec VPN Troubleshooting Solutions for information on the most common solutions to IPsec VPN problems. It contains a checklist of common procedures that you might try before you begin to troubleshoot a connection and call Cisco Technical Support. Prerequisites Requirements. Cisco Security Appliance Command Line Configuration Guide, Version 7.2 - Configuring Remote Access VPNs [Cisco ASA 5500-X Series Next-Generation Firewalls]
Configuring IP Access Lists. Introduction This document describes how IP access control lists (ACLs) can filter network traffic. It also contains brief descriptions of the IP ACL types, feature availability, and an example of use in a network. Access the Software Advisor (registered customers only) tool in order to determine the support of some of the more advanced Cisco IOS® IP ACL features. Int5505.pdf. Cisco 2911 - Remote Access VPN. Conf gd. Cisco IOS VPN Configuration Guide - Site-to-Site and Extranet VPN Business Scenarios [Cisco 7200 Series Routers] Connecting Remote Offices by Setting Up VPN Tunnels.
Welcome to Forbes.