

Illegal sports streaming: Inside the billion-dollar heist. On a frosty winter evening with downtown Chicago’s bustle subsiding outside his shuttered apartment window, a 24-year-old man whom we’ll call Johnny is about to cheat the NBA.
He is slouching on a sofa in silence, scrolling aimlessly through social media, when Twitter erupts. Thousands of miles away, LeBron James is cooking. China’s Internet Is Flowering. And It Might Be Our Future. The HeyTea shop in the Chaoyang district of Beijing is an expression of svelte minimalism, its LED lettering and black tiles giving off a vaguely retro vibe.

On a recent weekend, one of the last truly warm days of early fall, the location was full of upmarket customers — families with strollers, Gen Z-ers in knockoff Supreme streetwear — enjoying the popular cheese tea. NSA using Browser Cookies to track Tor Users. Yesterday a new classified NSA document was leaked by Edward Snowden - titled ‘Tor Stinks’ in which ideas were being kicked around for identifying Tor users or degrading the user experience to dissuade people from using the Tor browser.
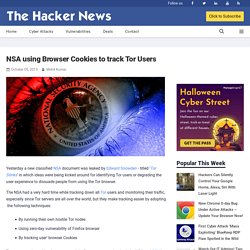
The NSA had a very hard time while tracking down all Tor users and monitoring their traffic, especially since Tor servers are all over the world, but they make tracking easier by adopting the following techniques: By running their own hostile Tor nodesUsing zero-day vulnerability of Firefox browserBy tracking user' browser Cookies Tor access node tracking is not new and the Document says that both the NSA and GCHQ run Tor nodes themselves. Chinese scientists are at the forefront of the quantum revolution. Adding these Chrome and Firefox extensions puts your privacy at risk. Defending your rights in the digital world. Is Firefox better than Chrome? It comes down to privacy. Viber. The First Spacewalk. The 25 Best Classical Music Tracks of 2018. Your Apps Know Where You Were Last Night, and They’re Not Keeping It Secret. The millions of dots on the map trace highways, side streets and bike trails — each one following the path of an anonymous cellphone user.
One path tracks someone from a home outside Newark to a nearby Planned Parenthood, remaining there for more than an hour. Another represents a person who travels with the mayor of New York during the day and returns to Long Island at night. Yet another leaves a house in upstate New York at 7 a.m. and travels to a middle school 14 miles away, staying until late afternoon each school day. Installation/Setup/Configuration: MoCA Setup and Info.
A Multimedia over Coax Alliance (MoCA) network Enables you to send information through the existing coaxial (coax) cable in your homeThis gives you both your television programming and Internet content through the same coax cable making MoCA perfect for transferring and streaming media between TiVo devices Helpful links: If you want to know more about MoCA and your TiVo, see our MoCA FAQ.For step-by-step instructions in setting up TiVo with MoCA, see our MoCA connection page MoCA Requirements You must have all the necessary equipment below (click for reference)
Machine Learning is Fun Part 6: How to do Speech Recognition with Deep Learning. Update: This article is part of a series.
Check out the full series: Part 1, Part 2, Part 3, Part 4, Part 5, Part 6, Part 7 and Part 8! You can also read this article in 普通话 , 한국어, Tiếng Việt or Русский. Speech recognition is invading our lives. It’s built into our phones, our game consoles and our smart watches. Technology. The Quantum Computer Factory That’s Taking on Google and IBM. Radar Basics. FrequencyCheck - Mobile Network Compatibility Search for Unlocked Phones and Devices. Google Groupes. LTE (telecommunication) - Wikipedia. Adoption of LTE technology Countries and regions with commercial LTE service Countries and regions with commercial LTE network deployment on-going or planned Countries and regions with LTE trial systems (pre-commitment) Telia-branded Samsung LTE modem For the complete list of all the countries/territories, see list of countries by 4G LTE penetration.
Much of the LTE standard addresses the upgrading of 3G UMTS to what will eventually be 4G mobile communications technology. Cs domLTE CSFB to GSM/UMTS network interconnects Voice over LTE (VoLTE) HSPA, UMTS, GSM, LTE and Other Acronyms Demystified. If you’re in charge of making the mobile purchase decisions for your company, or simply a consumer who wants to be informed before buying a new mobile device, you likely do a great deal of research before buying a smartphone.
However, as you begin to research smartphone choices, you start to get inundated with acronyms such as LTE, UMTS, GSM®, EDGE®, and so on. Instead of just nodding along with the smartphone rep the way you do when your crazy uncle corners you at the family reunion, let’s demystify a few of these popular acronyms to ensure you make intelligent buying decisions: CDMA: Code Division Multiple Access.
Google's TPU Chip Helped It Avoid Building Dozens of New Data Centers. Google operates what is surely the largest computer network on Earth, a system that comprises custom-built, warehouse-sized data centers spanning 15 locations in four continents.

But about six years ago, as the company embraced a new form of voice recognition on Android phones, its engineers worried that this network wasn’t nearly big enough. If each of the world’s Android phones used the new Google voice search for just three minutes a day, these engineers realized, the company would need twice as many data centers. At that time, Google was just beginning to drive its voice recognition services with deep neural networks, complex mathematical systems that can learn particular tasks by analyzing vast amounts of data. In recent years, this form of machine learning has rapidly reinvented not just voice recognition, but image recognition, machine translation, internet search, and more.
In moving to this method, Google saw error rates drop a good 25 percent. How Toy Story 2 Got Deleted Twice, Once on Accident, Again on purpose. “That’s when we first noticed it, with Woody.”

“[Larry Cutler] was in that directory and happened to be talking about installing a fix to Woody or Woody’s hat. He looked at the directory and it had like 40 files, and he looked again and it had four files.” How to Enter Recovery Mode on Lg G4. Recovery Mode is very important in context of customizing Android devices in proper way and to beyond its limits.

There many reasons why Recovery mode is important and most of us are already aware about us. Here we have this tutorial for LG G4 users, we have shown how we can enter recovery mode on LG G4 through several ways, that mean you can enter recovery mode through different ways. Also see: How To Resolve Android Bootloop On All Android Smartphones? If you are wondering what is Android bootloop in the first please, then you didn't have updated or rooted your Android Smartphones yet.
But those who have done it already might have came across this very often. Android bootloop is a common Android firmware glitch which throws your phone into endless booting and shutdown loop. Please follow the below given simple steps to resolve the Android bootloop issue on your favourite Android Smartphone from LG, HTC, Samsung, Motorola, Nokia, Huawei, Lenovo, Acer, Micromax or Lava. Symptoms and causes of Android Bootloop.
LG G5 news, release date, specs, price and more. The LG G5 is the followup to the G4. Announced at MWC 2016, the 5.5-inch G5 is a powerhouse offering from LG that features not one — but two — rear cameras, a removable battery, expandable storage and is running Android 6.0 Marshmallow. Breaking from its design scheme of the last few years, LG is going with a more traditional side button placement on the G5, rather than the back-mounted volume buttons we’ve almost gotten used to. The G5 also had various modular attachments that work by actually removing the lower portion of the phone. LG G5 Hands-on Video. Reid Hoffman’s Big Dreams for LinkedIn. Early on a Monday evening in June, Reid Hoffman, the founder and executive chairman of the business-oriented networking site LinkedIn, met Mark Pincus, the founder and chief executive of the gaming site Zynga, for dinner at a casual restaurant in Portola Valley, California, a wealthy residential town at the western edge of Silicon Valley.
Breakfasts and dinners are a big part of Hoffman’s life. Paul Ford: What is Code? A computer is a clock with benefits. VeraCrypt - Home. TrueCrypt's Security Audit Is Finally Done, with (Mostly) Good Results. IEEE Xplore: IEEE Access. Bitcoin mining the hard way: the algorithms, protocols, and bytes. This article explains Bitcoin mining in details, right down to the hex data and network traffic. If you've ever wondered what really happens in Bitcoin mining, you've come to the right place. My previous article, Bitcoins the hard way described how I manually created a Bitcoin transaction and sent it into the system.
2014 Tablet Comparison Guide. Shopping for a new tablet this holiday season? Or maybe you're looking for the best tablet to give to a loved one?