

Chrome Remote Desktop app. How to configure a computer to capture a complete memory dump. This article explains how to setup your computer so that a 'Complete memory dump' file will be created if the computer crashes.
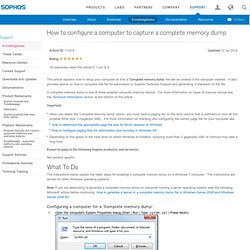
It also provides advice on how to compress the file for submission to Sophos Technical Support and generating a checksum of the file. A complete memory dump is one of three possible computer memory dumps. For more information on types of memory dumps see the Technical Information section at the bottom of this article. Important: Known to apply to the following Sophos product(s) and version(s) Not product specific The instructions below explain the basic steps for enabling a complete memory dump on a Windows 7 computer. Note: If you are attempting to generate a complete memory dump on computer running a server operating system read the following Microsoft article before continuing: How to generate a kernel or a complete memory dump file in Windows Server 2008 and Windows Server 2008 R2. Configuring a computer for a 'Complete memory dump' Compress the file for upload.
StartWire. 1.
Limited and Personal Use Only. Your use of the materials and services included on this Site is for informational purposes only. Unless you have received prior written consent from StartDate™, you agree you will not distribute, publish, transmit, modify, display or create derivative works from, exploit, or profit from the contents of this Site. You may only use the Site for the purpose of seeking employment or seeking and managing job prospects, career contacts or career networking on the Site. You agree that in order to use certain services, you will be required to submit your contact information, including email address. 2. 3. 4. 5. 15 The Network File System NFS. Enterprise Mobility Management. What we do: We Simplify Enterprise Mobility Every Mobile Device Smartphones & Tablets Laptops & Desktops Rugged Devices Printers & Peripherals Every Mobile OS Android Apple iOS and Mac OS BlackBerry and Symbian Windows Every Mobile Deployment Bring Your Own Device End User Multiuser Line of Business why we're different: Company Size and Product Scalability Company Differentiators 12,000+ customers in 150 countries 1,800+ employees across nine offices 600+ research and development resources Recognized as the industry leader Expertise in building enterprise solutions Product Differentiators Advanced integration and partner ecosystem Common development platform Broadest mobility solution set Multitenant, highly scalable architecture Flexible delivery: cloud and on premise Featured Resources Featured Webinars AirWatch Videos.

Difference Between NFS and CIFS. NFS vs.
CIFS In the realm of computers, file systems and network protocols, two names often surface ‘“ the NFS and the CIFS. These acronyms sound too technical, because indeed they are really tech related, not to mention, understanding each concept requires some background in computer networking and its various applications. To clarify the technicality of this topic, let’s start off with the NFS. The NFS is actually the acronym for Network File System. On the contrary, CIFS is its Windows-based counterpart used in file sharing. CIFS is actually the public version of SMB (Server Message Block protocol), invented by Microsoft. On a good note, some of the advantages of CIFS include: 1. 2. 3.
Although NFS already has many versions under its belt, some of its advantages are: OSI-TCP-Model-v1.png (1111×768) Osi 7 layer model. The OSI, or Open System Interconnection, model defines a networking framework for implementing protocols in seven layers.

Control is passed from one layer to the next, starting at the application layer in one station, proceeding to the bottom layer, over the channel to the next station and back up the hierarchy. Easy Way to Remember the OSI 7 Layer Model All People Seem to Need Data Processing or Please Do Not Throw Sausage Pizza Away Special thanks to M. Watkins Application(Layer 7) This layer supports application and end-user processes.
Presentation(Layer 6) This layer provides independence from differences in data representation (e.g., encryption) by translating from application to network format, and vice versa. Session(Layer 5) This layer establishes, manages and terminates connections between applications. Transport(Layer 4) This layer provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-end error recovery and flow control. Free Resume Builder. Write Your Cover Letter in Minutes: Cover Letter: LiveCareer. Company Salaries.