

Design Tools. Single photon/electron double slit experiment, resetting the detector material after each impact. What is the experimental (*) outcome of a single photon/electron double slit experiment under the constraint that after each detection the detector material is reset to the original state ie, in the limit it is substituted by another detector sheet, or photographic plate.
Of course that the impact positions should be recorded in a computer to construct the accumulated final image. Phase Velocity vs. Group Velocity. Faster-than-light. Faster-than-light (also superluminal or FTL) communication and travel refer to the propagation of information or matter faster than the speed of light.
Under the special theory of relativity, a particle (that has rest mass) with subluminal velocity needs infinite energy to accelerate to the speed of light, although special relativity does not forbid the existence of particles that travel faster than light at all times (tachyons). On the other hand, what some physicists refer to as "apparent" or "effective" FTL[1][2][3][4] depends on the hypothesis that unusually distorted regions of spacetime might permit matter to reach distant locations in less time than light could in normal or undistorted spacetime.
Although according to current theories matter is still required to travel subluminally with respect to the locally distorted spacetime region, apparent FTL is not excluded by general relativity. FTL travel of non-information[edit] Daily sky motion[edit] Light spots and shadows[edit] Dr. The Spy Files. StumbleUpon. Google K pek. Free Cloud Services: 2-20 GB Free Storage. I/O Interface. Online Circuit Simulator with SPICE. FlowStone. FlowStone uses a combination of graphical and text based programming.
Applications are programmed by linking together functional building blocks called components. Events and data then flow between the links as the application executes. All this happens instantly - there's no compiling, your application runs as you build it making development an extremely rapid process. FlowStone allows you to create your own components using Ruby. This is a very modern language that is incredibly easy to pick up. The real power of FlowStone comes from modules. FlowStone can interface with a vast range of external hardware. OpenSourceProcessors. Bug Labs. Arduino.
Phduino - pH meter using Arduino board for glass electrode. This project was move to Google Code will be closed soon.
Zedomax.com. DIY QuadroCopter Built with Arduino and Wii Motion Plus!
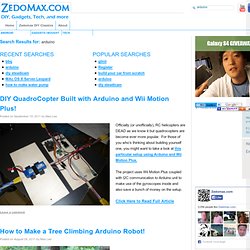
Officially (or unofficially), RC helicopters are DEAD as we know it but quadrocopters are become ever more popular. For those of you who’s thinking about building yourself one, you might want to take a look at this particular setup using Arduino and Wii Motion Plus. The project uses Wii Motion Plus coupled with I2C communication to Arduino unit to make use of the gyroscopes inside and also save a bunch of money on the setup.
Click Here to Read Full Article. Indoor Garderning. Arduino Assisted Gardening. Programming. Robotica. Visualization Tool. Lexipedia - Where words have meaning. Free PDF Search Engine. The Wolfram Education Portal Is Here! January 18, 2012 — Wolfram Blog Team Teachers, are you looking for a new way to integrate technology into your classroom? How about through a dynamic textbook or pre-generated lesson plans? Students, are you looking for some extra help or practice in your classes? How about using interactive demonstrations and widgets to help understand the concepts you are learning?
The Wolfram Education Portal is the answer for students and teachers alike! We are happy to announce the launch of the free Beta version of the Wolfram Education Portal. We developed the interactive textbook by working with the CK-12 Foundation, a non-profit organization with the mission to produce free and open source K-12 materials aligned to state curriculum standards and customized to meet student and teacher needs. The Wolfram Education Portal was built with the technology from Mathematica, and Wolfram|Alpha, and the Computable Document Format (CDF). Google-refine. By Sindice.
SIGMA. VisiNav. VisiNav is a system to search and navigate web data, collected from a multitude of sources.

In summary, the system demonstrates how to combine data from multiple sources into a single unified view, how to search and navigate the aggregated dataset, and how to re-use query results from web data in external applications. On a conceptual level, VisiNav deals with objects. Objects can have attributes and links to other objects. Disco Hyperdata Browser. The Disco - Hyperdata Browser is a simple browser for navigating the Semantic Web as an unbound set of data sources.
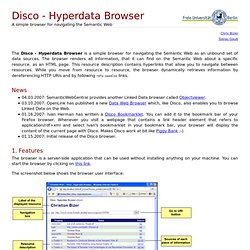
The browser renders all information, that it can find on the Semantic Web about a specific resource, as an HTML page. This resource description contains hyperlinks that allow you to navigate between resources. While you move from resource to resource, the browser dynamically retrieves information by dereferencing HTTP URIs and by following rdfs:seeAlso links.
News 04.03.2007: SemanticWebCentral provides another Linked Data browser called Objectviewer. 03.10.2007: OpenLink has published a new Data Web Browser which, like Disco, also enables you to browse Linked Data on the Web. 01.16.2007: Ivan Herman has written a Disco Bookmarklet. 1. The browser is a server-side application that can be used without installing anything on your machine. SamyGO, Samsung Firmware on the GO - Comodo IceDragon. Affordable encrypted VoIP - Comodo IceDragon. Product TiviPhone is a market-leading VoIP softphone for various smartphone platforms.

It also encrypts voice and video with the scientifically proven, open-source ZRTP. Provider We are Tivi, the developer and marketer of TiviPhone client software. Pay online with PayPal or Credit Card - Comodo IceDragon. How to recover TrueCrypt encryption password. Before using the unprotect.info software, first you need to download it to your computer.
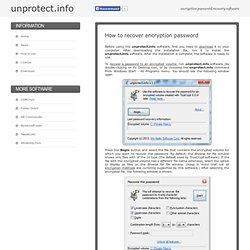
After downloading the installation file, run it to install the unprotect.info software. After the installation is complete, the software is ready to use. To recover a password to an encrypted volume, run unprotect.info software (by double-clicking on its Desktop icon, or by choosing the unprotect.info command from Windows Start - All Programs menu.
You should see the following window open: Press the Begin button and select the file that contains the encrypted volume for which you want to recover the password. You can use this window to select the character sets from which you want to try the passwords. Lowercase characters abcdefghijklmnopqrstuvwxyz. Downloads of DAQFactory HMI / SCADA Software - Comodo IceDragon. DAQFactory. DAQFactory - Comodo IceDragon. Hacker 10 – Security Hacker. I have been using Countermail for over a year on a weekly basis and this review is based on my experience with them during this time.
The service is free to try for a few days, after that you will be asked for payment which can be done with credit card, Paypal, wire transfer or Bitcoin. Credit card corporations force businesses to keep payment details stored for two weeks, Countermail claims to automatically destroy the records after that length of time but the credit card company and Paypal will likely preserve payment details for years although they will not be able to link them to any specific Countermail account or nick. If you pay with Bitcoin you will make tracing payment origin much more difficult but there is a surcharge. Signing up is simple, not requiring any personal information other than choosing a username and password, you only need Java installed in your computer, after account creation you can get rid of Java and use IMAP and SMTP with Thunderbird and Enigmail.
Facebook Privacy Watcher. Browser Extension Facebook Privacy Watcher is an addon for Mozilla Firefox and Google Chrome, that has been developed at Center for Advanced Security Research Darmstadt (CASED) in association with TU Darmstadt (Technical University of Darmstadt). It provides a new and very simple interface to manage your privacy settings on Facebook. Know your privacy settings Since the default privacy settings on Facebook are more and more open with each update, it is very important to be able to easily grasp and change the privacy settings, to be protected from unintended oversharing.
However, the settings are quite detailed, and thus it's hard to keep track of them. PublicFriendsOnly meCustom Simple and clear. Ipredia.org - Home of IprediaOS. Recover lost encryption password for TrueCrypt volume. Truecrack - Password cracking for truecrypt(c) volume files. - Google Project Hosting - Comodo IceDragon. WHAT TrueCrack IS? - NEW VERSION 3.5 AVAILABLE TrueCrack is a brute-force password cracker for TrueCrypt (Copyrigth) volumes. It works on Linux and it is optimized for Nvidia Cuda technology. It supports: PBKDF2 (defined in PKCS5 v2.0) based on key derivation functions: Ripemd160, Sha512 and Whirlpool. Free Protection, Virus Free Protection Software, Free Protection Downloads - Comodo - Comodo IceDragon.