

How to Dual Boot and Virtualize the Same Partition on Your Computer. Kali Linux ISO of Doom. In our last blog post, we provided an example of running an unattended network installation of Kali Linux.
Our scenario covered the installation of a custom Kali configuration which contained select tools required for a remote vulnerability assessment using OpenVAS and the Metasploit Framework. With just a few minor changes to this concept, we can further leverage Kali to create other cool and shiny toys as well. In today’s post, we’ll see what it takes to create what we fondly refer to as “The Kali Linux ISO of Doom”. The idea we had was tbao build an “unattended self-deploying” instance of Kali Linux that would install itself on a target machine along with a customized configuration requiring no user input whatsoever. On reboot after the installation completes, Kali would automagically connect back to the attacker using a reverse OpenVPN connection.
There could be several uses for such an image: The second scenario is rather cool. . # Now we create the client keys. Installing pyrit on Windows (with cygwin) Preface If you are as unfortunate as I am and you need to use Windows (for some reason) to install pyrit, you will probably have a bad time.
However! :) I figured out how to make it work, at least for CPU-based cracking. I used cygwin, but it should be possible with MinGW too. GPU-based cracking will be a lot (and I mean A LOT) more difficult though. Installation steps So, here are the steps (based on [1] and [2]): Install cygwin from cygwin.com (download: or Make sure that you install gcc, cc, openssl, svn! References. How To Install Pyrit CUDA on Mac. Parallel Programming and Computing Platform. What is CUDA?
Enroll today! Intro to Parallel Programming An open, online course from Udacity Instructors: Dr. John Owens, UC Davis and Dr. David Luebke, NVIDIA CUDA® is a parallel computing platform and programming model invented by NVIDIA. With millions of CUDA-enabled GPUs sold to date, software developers, scientists and researchers are finding broad-ranging uses for GPU computing with CUDA. Identify hidden plaque in arteries: Heart attacks are the leading cause of death worldwide. Analyze air traffic flow: The National Airspace System manages the nationwide coordination of air traffic flow. Visualize molecules: A molecular simulation called NAMD (nanoscale molecular dynamics) gets a large performance boost with GPUs. Background GPU Computing: The Revolution. BITMAIN. AntMiner U1 (MOQ: 500 units) U1 has been sold out.

AntMiner U1 is an USB miner with 1 BM1380 chip. Rated 1.6 GH/s, 2 watt power from the USB port. 25 GPUs brute force 348 billion hashes per second to crack your passwords. It’s our understanding that the video game industry has long been a driving force in new and better graphics processing hardware.
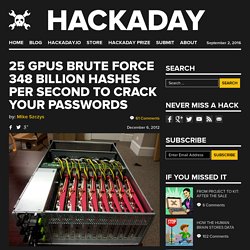
But they’re not the only benefactors to these advances. As we’ve heard before, a graphics processing unit is uniquely qualified to process encryption hashes quickly (we’ve seen this with bitcoin mining). This project strings together 25 GPU cards in 5 servers to form a super fast brute force attack. It’s so fast that the actual specs are beyond our comprehension. How can one understand 348 billion hashes per second? The testing was used on a collection of password hashes using LM and NTLM protocols. [via Boing Boing] The Raspberry Pi Compute Module. Hack and / - Password Cracking with GPUs, Part I: the Setup. Bitcoin mining is so last year.

Put your expensive GPU to use cracking passwords. When the Bitcoin mining craze hit its peak, I felt the tug to join this new community and make some easy money. I wasn't drawn only by the money; the concepts behind Bitcoin mining intrigued me, in particular the new use of graphics processors (GPUs). With a moderately expensive video card, you could bring in enough money to pay off your initial investment and your electricity bill in a relatively short time. Then Bitcoin tanked. Legitimate Reasons to Crack Passwords Before I get started, let's admit that there are some pretty shady reasons to crack passwords. That said, like with lock picking, there are legitimate reasons to crack passwords, particularly for a sysadmin or Webmaster: Test local users' password strength. In fact, many Linux systems will run a basic dictionary attack when you change your password to evaluate how weak it is.
Project Ubertooth - Hardware Build Guide. This describes the build process for Ubertooth One, but the processes for Ubertooth Zero and Pogoprog are essentially the same. step 0: read these instructions Seriously.

There are probably things in the later steps that you should know about before getting started. step 1: order a PCB You will need a four layer printed circuit board. If you are building an Ubertooth One or Zero, you should also consider building a Pogoprog unless you already have a plan for how you will program your board.