

Outlook Anywhere Basic vs. NTLM Authentication explained. I really wanted to figure out the difference between Basic and NTLM authentication (also known as Integrated Windows authentication) when enabling Outlook Anywhere.

Here is what I’ve found searching around. Let me know if you think differently. Risual support blog - Exchange 2010 Prompt after changing authentication for Outlook Anywhere. Replace Internal Name Certificates - Part II. Internal name and reserved IP address certificates will expire by October 31, 2015.

If you are reading this blog because you are knee-deep in replacing your publicly trusted internal name certificates, you have come to the right place. If you are just learning about replacing your internal name certificates, see our previous post Replacing Your Internal Name Certificates. Configure DAG in Exchange 2013. In Exchange 2013, Mailbox server high availability is provided by a feature called Database Availability Group (DAG).
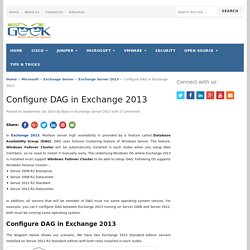
DAG uses failover clustering feature of Windows Server. The feature, Windows Failover Cluster will be automatically installed in each nodes when you setup DAG members, so no need to install it manually early. The underlying Windows OS where Exchange 2013 is installed must support Windows Failover Cluster to be able to setup DAG. Following OS supports Windows Failover Cluster: – Server 2008 R2 EnterpriseServer 2008 R2 DatacenterServer 2012 R2 StandardServer 2012 R2 Datacenter In addition, all servers that will be member of DAG must run same operating system version. The diagram below shows our scenario.
Step 1: NIC Configuration Let’s start with NIC configuration. Creating a two node Exchange 2013 DAG - jerridwills.com. Introduction I’m not sure how you got sucked into reading this post, but since you’re here I might as well tell you how to make your Exchange 2013 Mailbox role deployment highly available by using a Database Availability Group and I’m going to shorten that to DAG because it’s a nightmare to type.

Let’s get rockin’. Before we get too deep into it, let’s first make sure you’re on the right plane. Web Application Proxy Server in 2012 R2. When Microsoft discontinuedThreat Management Gateway (which once was Proxy and then ISA server) I must admit I was disappointed; it was a relatively inexpensive authenticated reverse proxy that worked with Exchange Server as well as many other complicated products.
In the interim we were told that Unified Access Gateway would be the replacement, but that product isn't as well suited to the task. Several alternatives are out there, including: Kemp, F5, Nginx, and Squid but either the price or the relative difficulty of setup isn't in line with TMG. Fortunately starting in Windows 2012R2 Microsoft introduced Web Application Proxy which largely fills the gap. How to Configure an SMTP Relay Connector in Exchange Server 2013. 403 - Forbidden: Access is denied. You do not have permission to view this directory or page using the credentials that you supplied. At a very high level under IIS server if you receive 403 error code means the content is forbidden but if you deeply check the server logs from IIS you will get an error code like 403.1 or 403.16 or 403.20.
For a complete list please follow the under given link which will give you more idea about the error code and description. I faced under given error which took my one month to figure out the solution. 403.16 – Client certificate is untrusted of invalid. I would like to elaborate my environment a little bit so that it becomes more clear why i was getting this error. I configured a web application on IIS8.5 which requires a client SSL certificate for authentication.
I Google every bit to find a solution which could solve my problem but still found nothing. As the error suggests that there is some problem with the client certificate. Open the registry editor (Be-careful!!!!!!!) Navigate to under given path HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL. Mobile Site Preview. Web Application Proxy Server in 2012 R2. Secure Extranet Publication of Exchange 2010 OWA via Server 2012 R2 Web Application Proxy. Hello all, Jesse Esquivel here again with a post about publishing Exchange 2010 via Server 2012 R2 Web Application Proxy (WAP).

Before we get started on this post I wanted to take a minute to talk about reverse proxy functionality and where Microsoft is headed with this technology. As you know, Threat Management Gateway (TMG) and Unified Access Gateway (UAG) have a definitive end of life. Some folks have looked into Internet Information Services Application Request Routing or ARR. ARR is a web farm extension meant for publishing web sites, however ARR does not do pre-authentication, there are no PowerShell cmdlets, no high availability, and there is no ongoing investment in ARR. Planning and Migrating a Small Organization from Exchange 2003 to Exchange 2013 (Part 1) This series will focus on how to migrate from Exchange 2003 to Exchange 2013 including approaches available, planning and migration.
If you would like to read the other parts in this article series please go to: Introduction If your organization is still on Exchange 2003 and you are eager to upgrade, you are certainly not alone.Although there is not a direct upgrade path from Exchange 2003 to Exchange 2013, a migration can still be straightforward. In this series we’ll examine how to plan and perform this migration. Our Example Organization. Analyze the Working of Exchange Server using ExMon Tool. In this blog, I will explain one of the best tools provided by Microsoft for Exchange server i.e.
ExMon. Microsoft introduced Exchange server User Monitor tool that helps administrator to monitor the performance of the Exchange server to know how it is affected by individual Outlook client. The tool enables administrator to collect & view real time data so that he can analyze current client usage pattern, it will help him to plan for future use accordingly. ExMon also allows administrator to view IP addresses of Exchange users, CPU usage, network traffic, Outlook edition & mode (Cached exchange mode or Classic online mode), sever side processor latency, total latency for network etc. Even though ExMon enables administrator to view & evaluate individual users’ usage, it doesn’t measure traffic by non-MAPI protocols like SMTP, POP3, IMAP4. Step 1: Download ExMon, it can be downloaded from Microsoft sites. Exchange Server 2010 Room Mailboxes Step by Step Guide.
Exchange Transaction Logs Fill Up Disk Completely. – Chase’s Notes. I have encountered this several times now.
I don’t know if the disks are being incorrectly sized or if something else is happening that is causing this, but the Exchange transaction logs are not being removed and they continue to fill up the disk until it is completely full, and then it causes mail to stop flowing or in sever cases the database will be dismounted and it can not be remounted until the disk has at least 1.5GB of space reclaimed. Every change made to an Exchange database must first be written in a transaction log file. Most Exchange administrators keep Exchange transaction log files on a dedicated drive. If the drive fills up, all Exchange databases in an affected storage group will dismount.
Before you can re-mount any of the databases, you must free up some space on the transaction log drive. Circular logging is not enabled and full successful backups are not being performed on a regular basis. Overview: Determine which logs are not necessary for restore. Exchange 2003 and Windows Server 2012 Domain Controller. Exchange 2010: How To Lockdown ActiveSync To Only Allow Specific IP Addresses – OSPC. This is a rather common question asked of an Exchange Admin, which usually results in a “not possible” answer.
Unless one uses a firewall in a very obscure way, to block activesync traffic to the cas servers, limiting the connection to certain IP Addresses, or other variable, this is truly a difficult task, if not impossible from a strictly exchange perspective. However, there is actually a rather simple solution that I will share with you in this article. This procedure should completely lockdown your Exchange ActiveSync connections to only a certain amount of specified IP Addresses. First step is to log into all existing exchange CAS servers and make sure IIS7 is installed. If it is not installed follow these steps: To Install IIS 7.5 on Windows Server® 2008 R2 You can perform this procedure using the user interface (UI) or a script.
Using the UI Using a Script: Click on “Roles” on the top left and make sure the following are installed if not, then install them to continue. Exchange Server Email Address Policies.