

Silk Road (black market) For the historical trade routes, see Silk Road.
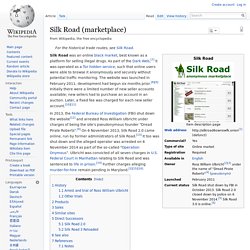
In 2013, the Federal Bureau of Investigation (FBI) shut down the website[12] and arrested Ross William Ulbricht under charges of being the site's pseudonymous founder "Dread Pirate Roberts".[4] On 6 November 2013, Silk Road 2.0 came online, run by former administrators of Silk Road.[13] It too was shut down and the alleged operator was arrested on 6 November 2014 as part of the so-called "Operation Onymous”.
Ulbricht was convicted of all seven charges in U.S. Federal Court in Manhattan relating to Silk Road and was sentenced to life in prison.[14] Further charges alleging murder-for-hire remain pending in Maryland.[2][15][16] Silk Road was founded in February 2011.[17] The name "Silk Road" comes from a historical network of trade routes, started during the Han Dynasty (206 BC – 220 AD), between Europe, India, China, and many other countries on the Afro-Eurasian landmass. Traveling the Silk Road: A Study of the Online Black Market. (Translated from the original Italian)
How And Why To Get To Silk Road. I’m sure by now many of you have heard about Silk Road.
It is the anonymous marketplace. It is the Amazon.com for all things illegal. And as anarchist activists we owe it to ourselves to at least understand its potential and browse its goods and services. I am going to give you the directions to Silk Road. I am also going to tell you where it leads. Editor Picks: The Top 10 Secret Resources Hiding in the Tor Network.
Editor Picks: The Top 10 Secret Resources Hiding in the Tor Network We've talked about the deep web before, but we never really covered the details of what's out there.
It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web. However, I should warn you—the deep web is a vast, often uncharted and unpoliced area. This is why it's great, but you need to attack it with an open mind. Getting Ready. Anonymity, Darknets and Staying Out of Federal Custody, Part One: Deep Web. Anonymity, Darknets and Staying Out of Federal Custody, Part One: Deep Web You've probably seen those deep-web images floating around on the Internet.
Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up. So what exactly is 'deep web' then? Anonymity, Darknets and Staying Out of Federal Custody, Part Two: Onions and Daggers. Anonymity, Darknets and Staying Out of Federal Custody, Part Two: Onions and Daggers In the first part of this series, we learned about darknets, as well as how they came about.
But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical address and a search warrant along with it.
Tor vs. I2P: The Great Onion Debate. Tor vs.
Anonymity, Darknets and Staying Out of Federal Custody, Part Four: The Invisible Internet. Anonymity, Darknets and Staying Out of Federal Custody, Part Four: The Invisible Internet In the last article, we left off with the Tor network and its hidden services.
As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P. For a web browsing proxy and hidden services host, Tor gets the job done well. But if you are looking to expand your options for secure communication, then enter I2P! Anonymity, Darknets and Staying Out of Federal Custody, Part Three: Hidden Services. Anonymity, Darknets and Staying Out of Federal Custody, Part Three: Hidden Services For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you.
Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. In the last article, we spent some time going over the concepts of onion routing and how it can be useful to you. Tor Hidden Services A Tor hidden service is simply a web server that runs locally and only takes requests from inside the Tor network. Due to the nature of hidden services being anonymous to a degree, the content can be extreme.
Setting Up Your Own Hidden Service If you have gotten this far in my series, you are probably interested in setting up your own service. Anonymity Networks. Don't use one, use all of them! Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet.
If you feel confused on which one is the "best" one to use the answer is simple. Use all three! Each anonymity network is designed for a different specific purpose. One network alone cannot do what the three can do together. Tor/Onionland Tor is an anonymous Internet proxy. Onionland uses the same method to connect to machine identified by a cryptographic public key. Positive Parts of Tor/Onionland: Written In C, that means that it is fast and generally low memory usage.Very easy and simple user interface. Negative Parts of Tor/Onionland: Written in C.