

Easiest Way to Hack ! NETBIOS BASED HACKING TUTORIAL BY Ethical Hacker GAURAV KUMAR. Ethicalhackers@yahoo.com Note- This tutorial may bear a resemblance to tutorials written by other authors.

I have acknowledged to tutorials or articles that I referred before writing this tutorial. It is possible that there may be other tutorials I have not referred and are similar to my tutorial. It is not possible for me to give acknowledgment to such tutorials and hence there must be no copyright or legal issues regarding thistutorial. Preface Dear reader I have written this tutorial keeping in mind that readers having only the basic knowledge will also be able to know how hackers hack using NetBIOS.
How To Use Netcat to Establish and Test TCP and UDP Connections on a VPS. Introduction Linux is known for having a great number of mature, useful command line utilities available out of the box in most distributions.
Skilled system administrators can do much of their work using the built-in tools without having to install additional software. In this guide, we will discuss how to use the netcat utility. Host Vulnerability Assessment with Nessus, NeXpose and Metasploitable 2. Network Vulnerability Assessment Basics. Pass the hash. In cryptanalysis and computer security, pass the hash is a hacking technique that allows an attacker to authenticate to a remote server/service by using the underlying NTLM and/or LanMan hash of a user's password, instead of requiring the associated plaintext password as is normally the case.
This technique can be performed against any server/service accepting LM or NTLM authentication, whether it is running on a machine with Windows, Unix, or any other operating system. Description[edit] On systems/services using NTLM authentication, users' passwords are never sent in cleartext over the wire. Man-in-the-middle attack. In cryptography and computer security, a man-in-the-middle attack (often abbreviated to MITM, MitM, MIM, MiM or MITMA) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
One example is active eavesdropping, in which the attacker makes independent connections with the victims and relays messages between them to make them believe they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within reception range of an unencrypted Wi-Fi wireless access point, can insert himself as a man-in-the-middle.[1] Example of an attack[edit] Illustration of man-in-the-middle attack. Suppose Alice wishes to communicate with Bob. 1. Top mobile security concerns: Blacklisted apps and password protection. Blacklisted apps and password protection issues remain a top security concern for organizations with a mobile workforce.
Password protection and application security are high on the list of security concerns as more organizations move to mobile first and Bring Your Own Device (BYOD) strategies. I recently spoke with Jonathan Dale, director of marketing for Fiberlink (recently acquired by IBM), and James Brown, chief digital technologist at Compuware Professional Services, and they answered some questions concerning the blacklisting and whitelisting of apps and password security. Creating app blacklists and whitelists According to Jonathan Dale, “File sharing apps are the most common blacklisted apps in the enterprise. The top five blacklisted apps include Dropbox, SugarSync, Box, Facebook, and Google Drive.” Figure A shows the top 10 list of blacklisted iOS and Android apps amongst Fiberlink customers: Figure A The top 10 list of blacklisted iOS and Android apps.
Figure B Conclusion. Dictionary attack. Birthday attack. Understanding the problem[edit] , about 7.9%.
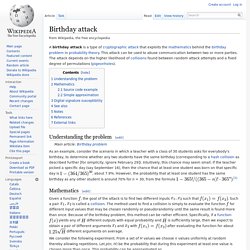
However, the probability that at least one student has the same birthday as any other student is around 70% for n = 30, from the formula Mathematics[edit] Given a function , the goal of the attack is to find two different inputs such that . Yields any of different outputs with equal probability and is sufficiently large, then we expect to obtain a pair of different arguments. Preimage attack. In cryptography, a preimage attack on cryptographic hash functions tries to find a message that has a specific hash value.
A cryptographic hash function should resist attacks on its preimage. In the context of attack, there are two types of preimage resistance: CrackStation - Online Password Hash Cracking - MD5, SHA1, Linux, Rainbow Tables, etc. Brute-force attack. The EFF's US$250,000 DEScracking machine contained over 1,800 custom chips and could brute-force a DES key in a matter of days.
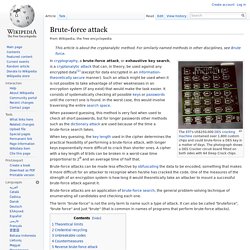
The photograph shows a DES Cracker circuit board fitted on both sides with 64 Deep Crack chips. When password guessing, this method is very fast when used to check all short passwords, but for longer passwords other methods such as the dictionary attack are used because of the time a brute-force search takes. When key guessing, the key length used in the cipher determines the practical feasibility of performing a brute-force attack, with longer keys exponentially more difficult to crack than shorter ones.