

Sayalipatil
Customer Complaint Management. According to Metric Stream, complaint management is the process of how organizations handle, manage, respond to and report customer complaints.
Systems are put into place to track and trend the data that is captured by complaint management processes. The organizations are established on the objective of delivering the best service and product to the customer. However, because of some issues, miss understating of the need of the customer or the defect in manufacture the faulty service or product is delivered to the customer. Working on the customer complains is also one of the ways of making them satisfied and maintaining the customer value. Inroduction : Kaizen module is an idea posting system, where any Employee within the organization can able to submit the idea which can be about anything, and once the idea posted to it will follow some Approval process which user has ability to configure the same.
Improvement of the organization is not the responsibility of the some of the employees of the organization. It involves every member of the organization irrespective of their hierarchy level. Customer Complaint Management : retail. Untitled — Customer Complaint Management. Introduction: Digitalization in corporate healthcare is revolutionizing health service providers to create a robust infrastructure by focusing on the patient’s needs.
This evolution is promising since patients are more comfortable using digital services for complex and sensitive issues which technically make life easier. Introduction: Digitalization in corporate healthcare is revolutionizing health service providers to create a robust infrastructure by focusing on the patient’s needs.
This evolution is promising since patients are more comfortable using digital services for complex and sensitive issues which technically make life easier. It is a clear indication for patients to embrace healthcare’s digital future by adopting the third wave of digitization. Core Functions: Find a Doctor: This Feature has removed the barrier of turning pages of the phone directory to find a specialized doctor to book an appointment.
The expansion of the virtual world has majorly transformed the way business operates and its arena.
For present-day, small and medium-size business establishments and enterprises have to create a strong online persona and a reliable suite of desktop applications to sustain the expansion and operation. As a business owner, it is inevitable to ensure unsurpassed user experience for the website visitors or application users. Choosing the right web application development frameworks such as .NET proves to be highly beneficial as it is scalable, secure and reliable. Do you have an application requirement that requires .NET expertise? Opt for the IT leaders, Leo TechnoSoft is a .net application development company that designs and builds quality solutions with complete Dot Net architecture using Visual Studio which is a collaborative platform.
Microsoft .Net Development. UEBA: User And Entity Behavior Analytics : cybersecurity. LTS Secure UEBA for SIEM. LTS Secure UEBA for SIEM - Download - 4shared - Sayali patil. LTS Secure Cyber Security Analytics PowerPoint Presentation, free download - ID:9748086. LTS Secure Security Analytics. LTS Secure Security Analytics - Download - 4shared - Sayali patil. LTS Secure Security Analytics.
MediaFire Pro: Faster bulk downloads, Ad free downloads, & 1 TB of storage.
From $3.75/month. LTS Secure Security Analytics.pdf File size: 1.33MB Uploaded: 2020-01-15 01:07:21 About PDF Formats Portable Document Format (PDF) is a specific document file format. Upgrade to PRO for the best download experience. LTS Secure SOC as a Service : cybersecurity. LTS Secure Intelligence Driven SOC is integrated Context-aware Security protection platform that provides and integrates prediction, prevention, detection and response capabilities by leveraging adaptive security framework.
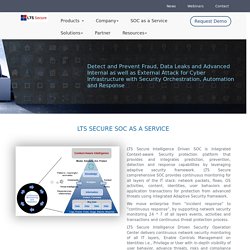
LTS Secure comprehensive SOC provides continuous monitoring for all layers of the IT stack: network packets, flows, OS activities, content, identities, user behaviors and application transactions for protection from advanced threats using integrated Adaptive Security framework. We move enterprise from “incident response” to “continuous response”, by supporting network security monitoring 24 * 7 of all layers events, activities and transactions and continuous threat protection process.
LTS Secure Intelligence Driven Security Operation Center delivers continuous network security monitoring of all IT layers, Enable Controls Management on Identities i.e., Privilege or User with in-depth visibility of user behavior, advance threats, risks and compliance dashboards. USER ENTITY BEHAVIOR ANALYTICS: A BOON FOR THE WORLD OF CYBER SECURITY. The world has seen an unabated rise in the number of cyber-attacks as the hackers continue to target the vulnerabilities in the security system.
Even a small loophole in security system can serve as an entry point for the cyber attackers. Insider threats pose significant risk to any organization and quite often it is very hard to detect. The encouraging part is that we have UEBA to address these threats. UEBA can be defined as a security solution that analyzes the behaviors of people that are connected to an organization’s network and entities or end-points such as servers, applications, etc. to figure out the anomalies in the security. UEBA uses behavioral analysis to monitor the activities of the users and entities. This can be explained with an example, Let us say an employee accesses a certain file named “A” daily, however he begins to send information from file A to an unknown entity. Untitled — USER ENTITY BEHAVIOR ANALYTICS: A BOON FOR THE... User Entity Behavior Analytics: A boon for the world of cyber security The world has seen an unabated rise in the number of cyber-attacks as the hackers continue to target the vulnerabilities in the security system.
Even a small loophole in security system can serve as an entry point for the cyber attackers. Insider threats pose significant risk to any organization and quite often it is very hard to detect. The encouraging part is that we have UEBA to address these threats. UEBA can be defined as a security solution that analyzes the behaviors of people that are connected to an organization’s network and entities or end-points such as servers, applications, etc. to figure out the anomalies in the security. This can be explained with an example, Let us say an employee accesses a certain file named “A” daily, however he begins to send information from file A to an unknown entity.
Now the question is “Why is finding insider threat so difficult?” SharePoint Portal Development company. Microsoft Office SharePoint Server is a world class enterprise portal platform that makes it easy for organizations to build and maintain portal sites for all the aspects of your business.

Portal sites enable users to connect to critical information, expertise and applications. With Microsoft Office SharePoint Server 2007 and Microsoft SharePoint 2010, 2013, 2016, Office 365, you can create collaboration portals which connect individual within an organization. SharePoint Portal Development company : sharepoint. SharePoint Portal Development comapny. Microsoft Office SharePoint Server is a world class enterprise portal platform that makes it easy for organizations to build and maintain portal sites for all the aspects of your business.
Portal sites enable users to connect to critical information, expertise and applications. With Microsoft Office SharePoint Server 2007 and Microsoft SharePoint 2010, 2013, 2016, Office 365, you can create collaboration portals which connect individual within an organization. Microsoft SharePoint has the following capabilities which can be harnessed for the portal development on that platform: - Untitled — SharePoint Portal Development comapny. SaaS-Tenant : Transit & Develop Multi Tenant SaaS system effortlessly. Are your clients demanding a SaaS version of your products? Have you realized lately that Software as a Service (SaaS) is the order of the day.
Then convert your single-tenant web-enabled application can into multi-tenant SaaS application! Your present applications may not be effective in a cloud environment for several reasons. Thus, you need SaaS. SaaS Tenant application offers cost-effective solutions, the benefits of which spread across the sectors, one of them being the maximum return on investments. Prototyping is an integral part of Design Thinking and User Experience design in general because it allows us to test our ideas quickly and improve on them in an equally timely fashion.
Prototyping has assisted stakeholders in effective and more awarded decision making. . The webinar explores the changing dynamics of Prototyping and choose best method to prototype the idea. The webinar is focused on: Why is prototyping so important in the design process? Fill The Form First Name (required) Last Name (required) Email (required) Company Website (required) Read Case Study Up Coming Webinar. Product Engineering Teams should aim at reducing noise while engineering a product. Overlooking the noise can impact in waste of time, cost and eventually product debacle. Seamless Product thought transitioning from the ideator’s to the people down the chain is essential to get a clear context into the product objective. Every attribute of the product or objective required to be addressed through the workflow must answer “Why” to define and solve product engineering problem.
Fundamentals Of SaaS Business: Multi-Tenant Models Tickets, Thu, Nov 14, 2019 at 9:00 AM. Fundamentals Of SaaS Business Multi-Tenant Models. Ensuring technology acceleration, SaaS multi-tenant application saves users from arduous task of building robust, scalable cloud solution and let them focus on their business logic. Software as a Service is the most popular delivery model existing in the market today for a wide variety of business applications. Being the most renowned division of cloud computing, its popularity is increasing in leaps and bounds with more and more businesses going for SaaS solutions. Benefits Of Adopting SaaS Solutions. Benefits Of Adopting SaaS Solutions. Benefits Of Adopting SaaS Solutions Introduction : SaaS, i.e., Software as a Service is the most popular delivery model existing in the market today for a wide variety of business applications.
Being the most renowned division of cloud computing, its popularity is increasing in leaps and bounds with more and more businesses going for SaaS solutions. In SaaS, business applications of various kinds are hosted as well as managed in a service provider’s datacenter and are employed by subscribing to it on an yearly or quarterly payment basis. It is accessible over an internet connection via any browser. benefits of adopting SaaS solutions:- • High Adoption Rate & Accessibility Anyone can access the SaaS applications from anywhere from any device, be it a desk computer, laptop, smartphone or a tablet. Advantages and Disadvantages of interpret SaaS SaaS (Software as a Service) is definitely the f... Untitled — Advantages and Disadvantages of interpret SaaS. Advantages and Disadvantages of interpret SaaS.
LTS Secure| 2406 Schumacher Drive, Mishawaka, IN, 46545| www.ltssecure.comLTS Secure provides high-level Cybersecurity Protection by:Centralization of Cybersecurity AlarmsPrioritization of CyberSecurity AlarmsOrchestration on Prioritized AlarmsAuthors:Satyen JainSagar Saurabh10.21.2019. Need of Alarm Centralization Priotirzation and Orchestration.pdf. Transfer Big Files Free - Email or Send Large Files. Need of Alarm Centralization Priotirzation and Orchestration.pdf. Need of Alarm Centralization Priotirzation and Orchestration. LTS Secure | 2406 Schumacher Drive, Mishawaka, IN, 46545| www.ltssecure.com LTS Secure provides high-level Cybersecurity Protection by: Centralization of Cybersecurity Alarms Prioritization of CyberSecurity Alarms Orchestration on Prioritized Alarms Authors: Satyen Jain Sagar Saurabh 10.21.2019 2 Cyber Security Alarm Threats: The rise of unknown Alarms monitoring is contributing to the maximum cybersecurity fraud and cyber threats internal as well as external to the organization.
Need of Alarm Centralization Priotirzation and Orchestration. Untitled — Converting Web Application to SaaS Multi Tenant... Converting Web Application to SaaS Multi Tenant Application by Sayali patil. Converting Web Application to SaaS Multi Tenant Application PowerPoint Presentation - ID:8453586. Converting Web Application to SaaS Multi Tenant Application - Download - 4shared - Sayali patil. Return On Investment (ROI)