

06.03.SEA.pdf. ECRYPT Low Cost Ciphers Page. Implementations of low cost block ciphers in Atmel AVR devices.
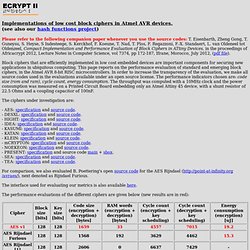
(see also our hash functions project) Please refer to the following companion paper whenever you use the source codes: T. Eisenbarth, Zheng Gong, T. Guneysu, S. Heyse, S Indesteege, S. Block ciphers that are efficiently implemented in low cost embedded devices are important components for securing new applications in ubiquitous computing. The ciphers under investigation are: Atmel-8873S-CryptoAuth-ATECC108-Datasheet-Summary.pdf. CryptoAuthentication. Get Started We'll tell you all you need to know to start evaluating and working with this product.
An easy-to-use USB dongle explores the capability of the ATSHA204(A), ATAES132, and ATECC108 » Learn more. A closer look at Atmel’s ATECC108. Atmel recently expanded its CryptoAuthentication portfolio with the ATECC108 solution, an elliptical curve cryptography (ECC) product.
As Atmel Product Marketing Manager Alex Dean notes, there are two basic encryption methods available on the security market today: symmetric and asymmetric key based algorithms. “In the context of using cryptography for authentication, symmetric key encryption uses an identical key on both a host and its client, while asymmetric key encryption employs two related keys (public and private),” Dean told Bits & Pieces. “Perhaps most importantly, asymmetric key encryption eliminates the security risk of key sharing, as the private key is never exposed. DIY Archives. Femto-ize it!
There’s no gender bias with the Femtoduino; it’s just a really small Arduino Leonardo clone. Ho-hum, another clone you say? Not so. The Femtoduino packs on board Bluetooth (BLE), accelerometer, altimeter and a USB port into a 34.54 mm (1.36 inches) wide PCB. At USD $75.00 a pop, it’s obviously more than the price of an Arduino. Smallest Arduino with Bluetooth LE + IMU – YouTube. So, Edward Snowden has some time on his hands in Russia, and decided to develop a super crypto-protected daughterboard for the Beaglebone Black. However, Josh Datko, Sparkfun’s hacker-in-residence and a well-known and respected player in the Beaglebone Black universe, did have time and has actually made what is being called the CryptoCape, a daughterboard which adds a hardware security layer to your BBB. Beaglebone Black CrytoCape What does it do beside run robots that write in disappearing ink?
MatsK (Mats Karlsson) Cathedrow/Cryptosuite. Encryption with Arduino AES-256 and RSA-512. ATSHA204 Authentication Chip plus Teensy. Atmel’s ATSHA204 helps secure the BBB. Hashlet – an authentication device embedded on a mini-cape – is specifically designed to secure the BeagleBone Black (BBB).
Powered by Atmel’s advanced ATSHA204, the mini-cape functions as an external hardware random number generator, performs the SHA-256 algorithm in hardware and is capable of storing up to 16 256-bit keys in write and read protected memory. Manufactured by Cryptotronix, the device is packaged with free software (GPLv3) that provides an easy to use Command Line Interface (CLI). “The Hashlet is assembled and tested by Cryptotronix prior to shipping,” the Cryptotronix crew explained in a recent product post. ”Simply slip the board on the top of the expansion header and the device is ready. The device uses /dev/i2c-1, which is enabled by default so there are no device-tree files that have to be installed.” Random numbers (data) are easily generated with a single line command, while creating and verifying a MAC is similarly straightforward. Building a security-optimized embedded design using protected key storage. The secure storage device’s basic functions enable many sophisticated security capabilities such as: Secure boot If an embedded device’s operating program is stored in an external Flash device, it's hard to prevent its contents from being copied and modified to run a fraudulent program.
The ATSHA204’s secure authentication capabilities can be used to implement a secure boot function which ensures that only the manufacturer’s authenticated firmware can be run on the system. To implement secure boot, a validating code or signature is stored in flash along with the boot code. The signature is created at the time of manufacture or code update and is the output of a cryptographic hash function, an irreversible algorithm that condenses the operating code into a compact but unique digest, typically 32-128 bytes in length. At system start-up, part of the boot sequence requires the security device to verify the signature accompanying the boot code. Atmelwhitepaper.pdf. ATSHA204 Authentication Chip Breakout - BOB-11551. Description: In secure embedded systems, you often need to authenticate messages or connected devices but many microcontrollers aren’t set up for the necessary cryptography.
That’s where the Atmel ATSHA204 comes in. The Atmel ATSHA204 is an optimized authentication chip that includes a 4.5Kb EEPROM. This array can be used for storage of keys, miscellaneous read/write, read-only, password or secret data, and consumption tracking. Access to the various sections of memory can be restricted in a variety of ways and then the configuration locked to prevent changes. ATSHA204. Get Started We'll tell you all you need to know to start evaluating and working with this product.
Datasheets ATSHA204 Mature ( file size: 1.11MB , 80 pages , revision H , updated: 07/2014 ) More Documents... Not Recommended for New Design. Atmel’s ATSHA204 helps secure the BBB.