

SanDisk ULLtraDIMM™ Solid State Drives (SSDs) DDR3 Memory.
Social media for Information Storage. Google Applications and Documents. Tape Backup Versus Disk Backup. VMWare VSphere v.X. EMC² Education Area. Block Level Versus File Level Storage. Disaster Recovery. Hypervisors and Migration. RAID. Online cloud. Virtualization and Cloud. Cloud and security. Local and Remote Replication. Dropbox. Systems Management content from Windows IT Pro. The subject of snapshots and clones for duplicating data comes up a lot, and the topic is somewhat complex.

Limitations of host-based mirroring for stretched clusters. For data mirroring, EMC SRDF is sometimes used in such a setup that both servers write to one location only (the “far” server writes across dark fibre links to the local storage).
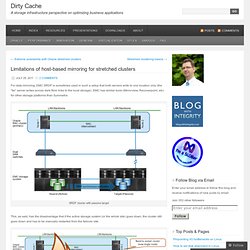
EMC has similar tools (Mirrorview, Recoverpoint, etc) for other storage platforms than Symmetrix. SRDF cluster with passive target This, as said, has the disadvantage that if the active storage system (or the whole site) goes down, the cluster still goes down and has to be manually restarted from the failover site. SRDF cluster failure recovery Host Based Mirroring A seemingly attractive alternative exists for replicating storage across multiple datacenters: Host Based Mirroring. Interestingevan's Blog. Cloud Computing vs. Virtualization. EmailShareEmailShare Like the article?
Cloud computing and Virtualization are both technologies that were developed to maximize the use of computing resources while reducing the cost of those resources. Virtualization Definition and Solutions. What is virtualization?
Virtualization refers to technologies designed to provide a layer of abstraction between computer hardware systems and the software running on them. By providing a logical view of computing resources, rather than a physical view, virtualization solutions make it possible to do a couple of very useful things: They can allow you, essentially, to trick your operating systems into thinking that a group of servers is a single pool of computing resources. And they can allow you to run multiple operating systems simultaneously on a single machine. Virtualization has its roots in partitioning, which divides a single physical server into multiple logical servers. Once the physical server is divided, each logical server can run an operating system and applications independently. Storage Optimization Techniques: Review the Benefits of Thin Provisioning. Introduction.
2011-025-slice-embedding.pdf. Business Continuity Knowledge Share. Cloutage - Tracking Cloud Incidents, Security, and Outages. Openfiler — Friendly enterprise storage management platform. What is continuous data protection (storage convergence)? - Definition from WhatIs.com. What is IT chargeback system? - Definition from WhatIs.com. IT chargeback is an accounting strategy that applies the costs of IT services, hardware or software to the business unit in which they are used.
What is virtual machine (VM)? - Definition from WhatIs.com. A virtual machine (VM) is an operating system OS or application environment that is installed on software which imitates dedicated hardware.
The end user has the same experience on a virtual machine as they would have on dedicated hardware. By submitting your email address, you agree to receive emails regarding relevant topic offers from TechTarget and its partners. You can withdraw your consent at any time. Contact TechTarget at 275 Grove Street, Newton, MA. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy.
Specialized software called a hypervisor emulates the PC client or server's CPU, memory, hard disk, network and other hardware resources completely, enabling virtual machines to share the resources. Virtual machines do not require specialized hypervisor-specific hardware. IBM big data platform - Bringing big data to the Enterprise. TDWI Big Data Maturity Model and Assessment Tool Sponsored by IBM, this big data maturity online assessment tool enables organizations to objectively measure the maturity of an enterprise’s big data analytics program across five dimensions that are key to deriving value from big data analytics: organization, infrastructure, data management, analytics, and governance.

Take it today! Big Data Hadoop Solutions, Q1 2014 Descritption: Read the report to see why IBM InfoSphere BigInsights was named a leader and how it stands in relation to other big data Hadoop vendors. Read the report The top five ways to get started with big data Learn how to determine which of the five can be your first step into big data. Get the white paper The FOUR V’s of Big Data. Clariion Cache: Idle, Watermark and Forced Flushing. Clariion Cache Flushing is a process – technique – method that controls when data from cache needs to be flushed out to Disk using patented algorithms that are defined as Watermarking levels.
To set watermarking limits on your Clariion frames, open Navisphere Manager. Once you select the Clariion that you need to set the Watermarking on, right click to select the properties of the Array and go to the Cache tab. There are several parameters you need to setup in there, without the actual knowledge and understanding of watermarking, please leave the default values in place. Internet Small Computer Systems Interface (iSCSI) Naming and Discovery. Guiding Principles in Information Security. 1.
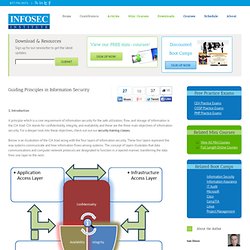
Introduction A principle which is a core requirement of information security for the safe utilization, flow, and storage of information is the CIA triad. CIA stands for confidentiality, integrity, and availability and these are the three main objectives of information security. For a deeper look into these objectives, check out out our security training classes. Below is an illustration of the CIA triad along with the four layers of information security.
Cloud 101: The Four Deployment Models. Types of Virtualization Technology-Advantages vs. Disadvantages.