

A SAML Whitepaper: How to Study and Learn SAML. Abstract This brief whitepaper provides a functional introduction to the SAMLv2 specifications tailored to protocol designer and developer's perspectives.

First a conceptual introduction is presented, next suggestions on how to study and learn SAML are given, and then more detailed aspects are discussed. 1. Conceptual Introduction to SAML SAML [OASIS.sstc‑saml‑exec‑overview‑2.0‑cd‑01] (Madsen, P. and E. Thus one can employ SAML to make statements such as: "Alice has these profile attributes and her domain's certificate is available over there, and I'm making this statement, and here's who I am.
" Then one can cause such an assertion to be conveyed to some party who can then rely on it in some fashion for some purpose, for example input it into a local policy evaluation gating access to some resource. Such applications of SAML are done in a particular "context of use". The specification of just how SAML is employed in any given context of use is known as a "SAML profile". The Resource STS: R-STS, RP-STS, A-STS... the other face of token issuing - Vibro.NET. Scénario de délégation d'identité. Ce scénario décrit une application qui a besoin d'accéder aux ressources principales qui requièrent que la chaîne de délégation d'identité exécute des vérifications de contrôle d'accès.
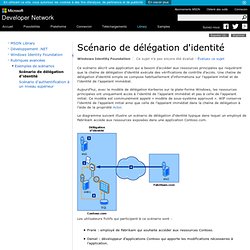
Une chaîne de délégation d'identité simple se compose habituellement d'informations sur l'appelant initial et de l'identité de l'appelant immédiat. Aujourd'hui, avec le modèle de délégation Kerberos sur la plate-forme Windows, les ressources principales ont uniquement accès à l'identité de l'appelant immédiat et pas à celle de l'appelant initial. Ce modèle est communément appelé « modèle de sous-système approuvé ». Developer's Introduction To Active Directory Federation Services. Single Sign-On A Developer's Introduction To Active Directory Federation Services Keith Brown One of the most important components of Windows Server® 2003 R2 is Active Directory Federation Services (ADFS).
ADFS solves a number of problems—one of the most obvious and compelling being business-to-business automation. In this article I'm going to take a look at ADFS from the perspective of a developer who is building a Web application and wants to allow other organizations to use it (for an administrator's viewpoint, see Matt Steele's article in TechNet Magazine. What kind of business-to-business problems am I referring to? An obvious solution would be to create a database containing user names and passwords, but this could become very costly to manage. What Is Active Directory Application Mode? In this section Active Directory Application Mode (ADAM) is a new mode of Active Directory that is designed specifically for directory-enabled applications.
ADAM is a Lightweight Directory Access Protocol (LDAP) directory service that runs as a user service, rather than as a system service. You can run ADAM on servers and domain controllers running operating systems in the Windows Server 2003 family (except for Windows Server 2003, Web Edition) and also on client computers running Windows XP Professional. The Business Need ADAM is a directory service that is designed to meet the needs of organizations that cannot rely solely on Active Directory for providing directory services for directory-enabled applications. For example, most directory-enabled applications require the directory service to be extended with application-specific schema extensions. The ADAM Solution.
Www.sans.org/reading_room/whitepapers/authentication/secure-implementation-enterprise-single-sign-on-product-organization_1520. Slant.avenuea-razorfish.com/0406_slant/SSOApproachPaper.pdf. All Will Be Revealed: ~7 Hours Recordings from the WIF Workshops - Vibro.NET. Www.pkisystems.com/pdfs/T9902004.pdf. SSO Strategy and Policies. SSO Strategy and Policies Before beginning implementation of a enterprise single sign on project, a lot of thinking and planning must go on.

This requires a cohesive SSO strategy and a set of governing SSO policies. Many projects don't do this and drift into unexpected security holes, SSO system and enterprise failures and frequently go over project budget. Saml-iis.html. By Alex Rykov 04/04/2007 Implementing single sign on (SSO) for several sites is a problem that has a multitude of variations and quite a few solutions.
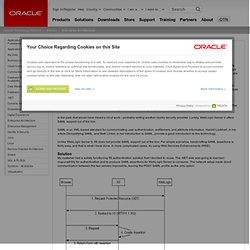
Security Assertion Markup Language (SAML) has emerged in the last five years to address this problem in a standard way, and BEA WebLogic Server 9 offers extensive support for it. Unfortunately, simple SAML configuration examples, especially for cross-platform scenarios, are hard to come by. This tutorial describes a simple SAML SSO scenario between Microsoft Internet Information Services Server (IIS) and BEA WebLogic Server 9. The article assumes some knowledge of SAML and is accompanied by a fully functional example that includes ASP.NET code as well as a script to fully configure WebLogic Server. Introduction Recently, I did some work for a customer who decided to add WebLogic Portal 9 into a predominantly ASP.NET Web infrastructure. In the past, that would have meant a lot of work—probably writing another clunky security provider.
First Issue : Authenticate WebLogic 11g with Active Directory User and SAML. OASIS Security Services (SAML. Defining and maintaining a standard, XML-based framework for creating and exchanging security information between online partners Nathan Klingenstein, ndk@internet2.edu, ChairThomas Hardjono, hardjono@mit.edu, ChairHal Lockhart, hal.lockhart@oracle.com, SecretaryScott Cantor, SecretaryAnil Saldhana, anil.saldhana@redhat.com, Secretary Table of Contents Announcements SAML--Right Here, Right Now Webinar: This webinar from 25 Sept 2012 summarizes the accomplishments of the TC and discusses plans for SAML 2.1.
Download the WMV or PPTX version. Overview The Security Assertion Markup Language (SAML), developed by the Security Services Technical Committee of OASIS, is an XML-based framework for communicating user authentication, entitlement, and attribute information. Single Sign-On. Gheimdall - A small web application for Google Apps SSO service. GHeimdall - A small web application for Google Apps SSO service This program is a TurboGears project for Google Apps SSO service.
This program enables you to authenticate Google Apps users by your own authenticate back end. There is a functionality for changing users' passwords for an option. To use it, please read the manual included in the tarball. Please do not pronounce leading G. Switching the web framework from TurboGears to Django (GHeimdall2). Untimate SSO SAML. SAML 2.0 Debugger. Example SAML 2.0 Request and Response. Anatomy of SAML Messages.
Feide RnD Identity Stuff at UNINETT.

Skip to content Anatomy of SAML Messages The SAML XML XSD Schemas are large and be a bit complex to read through to get a good overview of the content of a SAML Request and Response. I’ve tried to summarize the essence of the schemas applied to an AuthnRequest and a typical Response. Online community for the Security Assertion Markup Language (SAML) OASIS Standard. SimpleSAMLphp. Protect The Business - Enable Access.
Welcome to Attack Research. AD FS 2.0 Step-by-Step Guide: Federation with Oracle Identity Federation. Updated: July 22, 2010 Applies To: Active Directory Federation Services (AD FS) 2.0 This guide provides step-by-step instructions for configuring a basic identity federation deployment between Microsoft® Active Directory® Federation Services 2.0 (AD FS 2.0) and Oracle Identity Federation (OIF) by using the Security Assertion Markup Language (SAML) 2.0 protocol ( with the SAML2.0 HTTP POST binding.
Throughout this document, there are numerous references to federation concepts that are called by different names in the Microsoft and Oracle products. The following table assists in drawing parallels between the two vendors’ technologies. In this deployment, each product performs both the claims provider/identity provider role and the relying party/service provider role. SimpleSAMLphp. Democratizing Identity Management. Anatomy of SAML Messages.
Anatomy of a SAML-Secured SOAP Message (Superpatterns) As promised, here is a dissection of the SOAP message from yesterday's post on the AM 7.1 Beta Secure Web Services Tutorial. First, let's take another look at the secured message in its entirety: