

Free hacking linux. HacDC. How to Hack Your Wii for Homebrew Games and DVD Playback. Want to play emulated games on your Wii?
How about DVD playback? Here’s how to use the SmashStack exploit to hack your Wii with the latest system menu and enable all of that and more! And yes, in case you are wondering, this does work with the latest version 4.3 firmware update. Before we get started, it’s important to mention that this guide will modify the software on your Wii, which will void the warranty, and there’s a chance that you could make your Wii console unusable if things go wrong. We didn’t have any problems hacking our own Wiis, but your mileage may vary.
What You’ll Need The SmashStack exploit requires – you guessed it – Super Smash Bros Brawl in order to execute it, as well as one GameCube controller, and you can borrow both from a friend or find them cheap online. You’ll also need an SD/SDHC card for all of the homebrew (“home brewed” apps) you want download—I’d recommend at least a 1 GB card to make sure you have enough space. Let’s Get Started with Hacking the Wii. CrackStore. Product Hacking. 12 Dozen Places To Educate Yourself Online For Free. How to use Google for Hacking. Google serves almost 80 percent of all search queries on the Internet, proving itself as the most popular search engine.
However Google makes it possible to reach not only the publicly available information resources, but also gives access to some of the most confidential information that should never have been revealed. In this post I will show how to use Google for exploiting security vulnerabilities within websites. The following are some of the hacks that can be accomplished using Google. 1. Hacking Security Cameras There exists many security cameras used for monitoring places like parking lots, college campus, road traffic etc. which can be hacked using Google so that you can view the images captured by those cameras in real time. Inurl:”viewerframe? Click on any of the search results (Top 5 recommended) and you will gain access to the live camera which has full controls.
How To Become A Hacker. Copyright © 2001 Eric S.

Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker? ". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one.
A lot of hackers now consider it definitive, and I suppose that means it is. Still, I don't claim to be the exclusive authority on this topic; if you don't like what you read here, write your own. If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document.
Numerous translations of this document are available: ArabicBelorussianBulgarianChinese, Czech. The five-dots-in-nine-squares diagram that decorates this document is called a glider. If you want to be a hacker, keep reading. 1. The Best Hacking Tutorial Sites - Learn Legal Hacking. Katamari Hack. Offensive Security Training presents - The Exploit Database. Nmap - Free Security Scanner For Network Exploration & Security. Access Any Website Or Forum Without Registering. Visit any forum or website to find something useful and they will ask you to register.
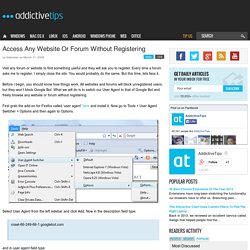
Every time a forum asks me to register, I simply close the site. You would probably do the same. But this time, lets face it. Before I begin, you should know how things work. All websites and forums will block unregistered users, but they won’t block Google Bot. First grab the add-on for Firefox called ‘user agent’ here and install it. Select User Agent from the left sidebar and click Add. Crawl-66-249-66-1.googlebot.com and in user agent field type: Googlebot/2.1 (+ as shown in the screenshot below. Select Google Bot as your User Script by going to Tools > User Agent Switcher. Cain & Abel. Cain & Abel is a password recovery tool for Microsoft Operating Systems.
It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncovering cached passwords and analyzing routing protocols. The program does not exploit any software vulnerabilities or bugs that could not be fixed with little effort. It covers some security aspects/weakness present in protocol's standards, authentication methods and caching mechanisms; its main purpose is the simplified recovery of passwords and credentials from various sources, however it also ships some "non standard" utilities for Microsoft Windows users. The latest version is faster and contains a lot of new features like APR (Arp Poison Routing) which enables sniffing on switched LANs and Man-in-the-Middle attacks.
Open Port Check Tool. Ophcrack.