

- Avaddon Verschlüsselung geknackt - The No More Ransom Project veröffentlicht Entschlüsselungssoftware. - Avaddon Verschlüsselung geknackt - The No More Ransom Project veröffentlicht Entschlüsselungssoftware.
A TINY BIT about Cryptography. Darknet & The Deep Web. REVEALED: Hundreds of words to avoid using online if you don't want the government spying on you. Department of Homeland Security forced to release list following freedom of information requestAgency insists it only looks for evidence of genuine threats to the U.S. and not for signs of general dissent By Daniel Miller Published: 09:32 GMT, 26 May 2012 | Updated: 17:46 GMT, 26 May 2012.

Bank of the Underworld. By evening, a group of “carders”—cybercriminals who specialize in selling stolen credit-card numbers—had gathered online at a secure forum known as carder.pro to discuss the situation.

According to Damon McCoy, a George Mason University professor who studies cybercrime, such forums are not open to the public; you must apply to join the discussion. “They vet you to make sure you are a good criminal,” he told me. Despite not being able to access their accounts, some of the carders remained hopeful. “LR will be back and give everyone triple their account balance,” one wrote.
Blackphone - The first phone that keep your privacy. How the NSA Plans to Infect 'Millions' of Computers with Malware. One presentation outlines how the NSA performs “industrial-scale exploitation” of computer networks across the world.
Top-secret documents reveal that the National Security Agency is dramatically expanding its ability to covertly hack into computers on a mass scale by using automated systems that reduce the level of human oversight in the process. The classified files – provided previously by NSA whistleblower Edward Snowden – contain new details about groundbreaking surveillance technology the agency has developed to infect potentially millions of computers worldwide with malware “implants.” The clandestine initiative enables the NSA to break into targeted computers and to siphon out data from foreign Internet and phone networks.
Algorithms and Future Crimes: Welcome to the Racial Profiling of the Future. Photo Credit: Shutterstock.com/Viappy February 28, 2014 | Like this article?
Join our email list: Stay up to date with the latest headlines via email. Across the country, large police departments have been developing their ability to track where crime will happen next using predictive software. Cable Reveals Extent Of Lapdoggery From Swedish Govt On Copyright Monopoly. Among the treasure troves of recently released WikiLeaks cables, we find one whose significance has bypassed Swedish media.
In short: every law proposal, every ordinance, and every governmental report hostile to the net, youth, and civil liberties here in Sweden in recent years have been commissioned by the US government and industry interests. I can understand that the significance has been missed, because it takes a whole lot of knowledge in this domain to recognize the topics discussed. Court Rules Americans Can Be Ordered to Decrypt Data. NSA files decoded: Edward Snowden's surveillance revelations explained. Two factors opened the way for the rapid expansion of surveillance over the past decade: the fear of terrorism created by the 9/11 attacks and the digital revolution that led to an explosion in cell phone and internet use.

But along with these technologies came an extension in the NSA’s reach few in the early 1990s could have imagined. Details that in the past might have remained private were suddenly there for the taking. Apple Decides That Dead Silence Is The Best Way To Address Major Encryption Flaw On OS X. Big Data: why is metadata more personal than our fingerprints. A l’occasion du colloque « la politique des données personnelles : Big Data ou contrôle individuel « organisé par l’Institut des systèmes complexes et l’Ecole normale supérieure de Lyon qui se tenait le 21 novembre dernier, Yves-Alexandre de Montjoye (@yvesalexandre) était venu présenter ses travaux, et à travers lui, ceux du MediaLab sur ce sujet (Cf. « D’autres outils et règles pour mieux contrôler les données » ).
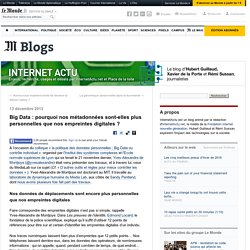
Yves-Alexandre de Montjoye est doctorant au MIT. Il travaille au laboratoire de dynamique humaine du Media Lab, aux côtés de Sandy Pentland, dont nous avons plusieurs fois fait part des travaux. Nos données de déplacements sont encore plus personnelles que nos empreintes digitales Faire correspondre des empreintes digitales n’est pas si simple, rappelle Yves-Alexandre de Montjoye. Image : illustration de l’unicité de nos parcours repérés via des antennes mobiles.
Et Yves-Alexandre de nous inviter à retrouver un de ses collègues du Media Lab. Google wants to make sure you know that it scans you emails. Good news!
Google is stil scanning your emails, but at least now they're asking permission. As of Monday, Google has updated its terms of service to explicitly inform Gmail users that it is in the habit of scanning their personal emails for the purposes of providing target advertisements, custom search results, and other features. The revised terms of service now state, "Our automated systems analyze your content (including emails) to provide you personally relevant product features, such as customized search results, tailored advertising, and spam and malware detection.
Mythologies du Darknet. Entrapment & Marginalization.