


VentureBeat: How to fool facial recognition technology? The day when you’ll be able to hold up your phone and identify a stranger through a viewfinder is getting closer. Google’s Goggles, a mobile app for visual search, has a facial recognition version unreleased to the public, while Israeli startup Face.com’s technology can tag people’s faces in Facebook photos. Facebook even released a basic version of face detection last night, although it doesn’t have recognition. So in a world where technology chips away at our ability to remain anonymous, how does one reclaim some semblance of control? It turns out there’s actually a pretty simple way around the facial recognition technology available in the market today, according to Adam Harvey, a graduate student at NYU’s ITP (the same program that produced Foursquare chief executive Dennis Crowley and that Twitter’s location guru Raffi Krikorian taught at).
21 Masculine Man Cave Ideas Man caves might get a bad stigma from all of the television shows out there, terrible movies and sitcoms that glorify these rooms as something tacky and horrible. But there is living proof out there that they can be done with taste and class. If you’re in the market for a man cave, or trying to convince your other half that a secluded room in the house is just what you need– our favorite 21 man cave inspirations could serve as a great guide for you, too. The Future of Surveillance in a Post-Snowden World Michael V. Hayden, former director of the National Security Agency and the Central Intelligence Agency. The following comments are adapted from his talk at the George Mason University's School of Public Policy on Feb. 28 for the National Security and Foreign Policy Lecture Series.
Blink! - Log in to Your PC by Simply Looking at It! Logging into Windows has never been easier! Simply look into your webcam and you’ll be logged into your account in the blink of an eye. Blink! employs advanced face recognition technologies to provide automatic, quick and reliable login for one, or multiple, computer users. Reliable Login under Varying Conditions With Blink! wearcam.org/sousveillance.htm Steve Mann, 2002 Secrecy, not privacy, may be the true cause of terrorism Gary Morton once said that ``many people feel that the security of Big Brother is another form of terror.'' -- Gary Morton, Dec 08, 01 09:56:40 PM -0500, posted to CitizensontheWeb.com. It has often been said that the true causes of terrorism are oppression, bad foreign policy, and secrecy, rather than privacy. (In fact some have even gone so far as to say that they've felt more frightened of the soldiers of their own armed forces than of the so-called ``terrorists''.)
Face.com Facial Recognition Face.com's API now returns an age estimation for faces it detects in photos - seen here with some recognizable examples. Looking at someone’s face can tell you a lot about who they are. Running a picture through Face.com‘s systems let’s you turn those instincts into cold hard data.
Datafication, dataism and dataveillance: Big Data between scientific paradigm and ideology Datafication, dataism and dataveillance: Big Data between scientific paradigm and ideology Jose van Dijck Abstract Metadata and data have become a regular currency for citizens to pay for their communication services and security—a trade-off that has nestled into the comfort zone of most people. This article deconstructs the ideological grounds of datafication. Datafication is rooted in problematic ontological and epistemological claims.
Face Emotion Recognition New Reviews There was a time when web page design used to be all about programming skills and several hours of coding, testing and debugging were required for a beautifully designed web site. However, with tremendous progress in web design arena, these have ...
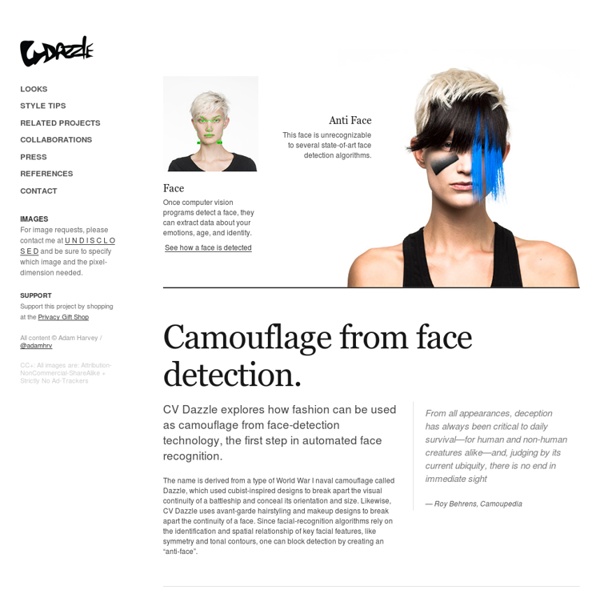
CV Dazzle: Open-Source Camouflage From Computer Vision by Adam Harvey by sirchamallow Nov 4