It's because I think too much: Galactic Manicure
I loved how my glittery gradient mani turned out so much that I decided to do a variation on it, using the night sky as my inspiration! Here's how I did it: 1. Prep I grabbed deep navy, silver glitter, and gold glitter polish along with my favorite top coat. I also grabbed an orange stick and some nail art rhinestones. 2.
How to Vanish with a New Identity
Dark Side or not, it's always good to say, "Hey, folks. Don't forget, this is illegal. Do it at your own risk. LH is not responsible for any trouble you may cause/get yourself into!"
Cracking WEP Using Backtrack: A Beginner’s Guide / Ryan Underdown
This tutorial is intended for user’s with little or no experience with linux or wifi. The folks over at remote-exploit have released “Backtrack” a tool which makes it ridiculously easy to access any network secured by WEP encryption. This tutorial aims to guide you through the process of using it effectively. Required Tools
Top Ten Uses for Duct Tape
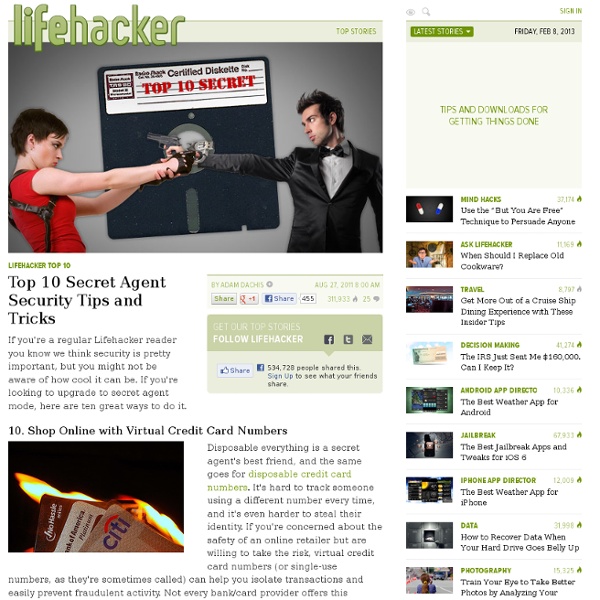
Top ten reasons why you should wear duct tape to the prom by the Duct Tape Guys, authors of The Duct Tape Book(s) 10. Cheaper than renting a tux or gown. 9. Resistant to punch spills. 8. Prom decorations start falling down? Just peel off part of your outfit and repair 'em on the spot. 7. The gals' dads LOVE those hard-to-remove duct tape gowns. 6.
Hacking a commercial airport WLAN
Posted on 30/8/06 by Felix Geisendörfer Welcome lifehacker.com & hackszine.com visitors. Read this follow up post if you care about the story of this article.
25 Things Women Should Know How To Do
I normally don't read mass emails but a good friend of mine sent this to me this morning and I couldn't resist reading the 25 Life Saving Tips Every Woman Should Know. I probably have mastered about 3 of these but now I have a good starting point of what I should learn. I'm not sure that you all will agree with these but I felt that as a member of Girls Guide To I should share this list with you. (And this ecard made me crack up too!)
How to hide emails from government snooping
By Jack Schofield, The GuardianMonday, April 2, 2012 21:38 EDT Despite coalition proposals to monitor public email, there remain numerous free or low-cost methods to keep messages private You already know how to keep messages private: you just encrypt the contents using a password. But although this kind of technology has been freely available to PC users since Phil Zimmermann launched PGP (Pretty Good Privacy) in 1991, hardly anyone uses it. The benefits of email and online messaging are that they are fast and relatively frictionless – you don’t need to address an envelope, find a stamp, walk to a post box and so on – and encryption becomes an annoyance. The problem with the latest government attempts at snooping is that they are not concerned with the content of messages, but their existence.
Teacher Goals You Can Actually Accomplish Over One School Year
Choose one social media site to master this year. Share snapshots and musings from your year of teaching on Instagram. Follow teachers you admire and get your own following on Twitter. Or, check out how to do teacher PD via social media. 6. Keep work at work.
how to: repair a shattered eyeshadow
How to repair your shattered eyeshadow. Today I’m going to share something with you, something precious and close to me. It will help you preserve your sanity and hard earned dollars. It might be a little bit of fun for your Monday too, but I don’t want to assume things on your behalf. Have you ever shattered a brand new eyeshadow?
Creating Mosaic Art with Google Drawings
Making Mosaic Art with Google Drawings is a fun way to get kids creating in the classroom. Here are the steps to get started along with 5 ideas for using this activity in the classroom. This post is written by Sarah Jacobs, a middle school technology and English teacher from San Jose, California.
Water Marble Tutorial. Supplies: orange stick or...
Water Marble Tutorial. Supplies: orange stick or toothpick, shot glass or cup (the smaller the circumference, the less polish you end up wasting), room temp. water, nail polish, tape (optional, but it helps with the clean up) I like to begin by prepping my nails with base coat and one coat of polish. Here I used China Glaze Innocence for a nice neutral base. Steps:
Top 10 Best Budget Smartphones Under 200 USD
Not everyone has the best of budget or saving to buy expensive phones. Majority of them wants a phone that is light on their pocket yet have the best of features. Starting from a big screen to an amazing camera, large storage space, low-cost mobiles offers some of the best features that any person may want. This article will be helpful for people who do not want to dig deep in their pockets and still find the best budget smartphones under USD 200. There are ample of low-price smartphones launched in year 2019 that fits your budget and are power packed with some of the best features:
3 Ways You Can Use Video to Grow Your Email List Fast
Here’s the deal: video is huge right now, and it’s only going to get bigger.2 But don’t just believe me on that, check out these facts: Snapchat (an app for making and consuming video) is only 5 years old and valued at $20BFacebook-owned Instagram recently copied Snapchat video features almost one-to-oneFacebook VP Nicola Mendelsohn said that in 5 years, our Facebook feeds will be “all video” Now here are a few email + video stats: The word “video” in subject line increases open rate by 19% (source)A video inside email increases click-through rate by 60% (source)Video can increases web conversion rates by 100% (lots of examples here)
Welcome to Your Private Little Stash of (Totally Free) Cool Tools at LYL…
And More Importantly, Welcome to the Live Your Legend Family! Now that you’re in, you’re in for life. You’ve just joined a community of over 100,000 Living Legends from every country in the world. Something tells me you’re going to enjoy your new surroundings. And remember, we all get out of things what we put in, so please commit to being an engaged member of your new tribe.