LXC
LXC (LinuX Containers) is an operating system–level virtualization method for running multiple isolated Linux systems (containers) on a single control host. The Linux kernel comprises cgroups for resource isolation (CPU, memory, block I/O, network, etc.) that does not require starting any virtual machines. Cgroups also provides namespace isolation to completely isolate application's view of the operating environment, including process trees, network, user ids and mounted file systems. Overview[edit] LXC provides operating system-level virtualization not via a virtual machine but rather through a virtual environment that has its own process and network space. Security[edit] Alternatives[edit] LXC is similar to other OS-level virtualization technologies on Linux such as OpenVZ and Linux-VServer, as well as those on other operating systems such as FreeBSD jails, AIX Workload Partitions and Solaris Containers. See also[edit] References[edit] External links[edit]
User-mode Linux
User-mode Linux (UML)[1] enables multiple virtual Linux kernel-based operating systems (known as guests) to run as an application within a normal Linux system (known as the host). As each guest is just a normal application running as a process in user space, this approach provides the user with a way of running multiple virtual Linux machines on a single piece of hardware, offering security and safety[citation needed] without affecting the host environment's configuration or stability. Applications[edit] User-mode Linux is supported by libvirt In UML environments, host and guest kernel versions need not match, so it is entirely possible to test a "bleeding edge" version of Linux in User-mode on a system running a much older kernel. UML also allows kernel debugging to be performed on one machine, where other kernel debugging tools (such as kgdb) require two machines connected with a null modem cable. Integration into the Linux kernel[edit] Comparison with other technologies[edit]
VMware ESX
VMware ESX is an enterprise-level computer virtualization product offered by VMware, Inc. ESX is a component of VMware's larger offering, VMware Infrastructure, which adds management and reliability services to the core server product. VMware is replacing the original ESX with ESXi.[2] The basic server requires some form of persistent storage (typically an array of hard disk drives) that store the hypervisor and support files. A smaller footprint variant, ESXi, does away with the first requirement by permitting placement of the hypervisor on a dedicated compact storage device. Naming[edit] ESX is apparently derived from "Elastic Sky X",[5] but with rare exceptions[6] this doesn't appear in official VMware material. Technical description[edit] VMware, Inc. refers to the hypervisor used by VMware ESX as "vmkernel". Architecture[edit] The vmkernel itself, which VMware says is a microkernel,[10] has three interfaces to the outside world: hardwareguest systemsservice console (Console OS)
QEMU
QEMU (short for "Quick EMUlator") is a free and open-source hosted hypervisor that performs hardware virtualization. QEMU is a hosted virtual machine monitor: It emulates central processing units through dynamic binary translation and provides a set of device models, enabling it to run a variety of unmodified guest operating systems. It also provides an accelerated mode for supporting a mixture of binary translation (for kernel code) and native execution (for user code), in the same fashion as VMware Workstation and VirtualBox do. Licensing[edit] QEMU was written by Fabrice Bellard and is free software and is mainly licensed under GNU General Public License (GPL). Details[edit] QEMU has two operating modes:[3] User-mode emulation Computer emulation Architecture[edit] Features[edit] QEMU can save and restore the state of the virtual machine with all programs running. The virtual machine can interface with many types of physical host hardware. Tiny Code Generator[edit] Accelerator[edit] KVM[edit]
Installing Python on Windows
First, download the latest version of Python 2.7 from the official Website. If you want to be sure you are installing a fully up-to-date version, click the Downloads > Windows link from the home page of the Python.org web site . The Windows version is provided as an MSI package. To install it manually, just double-click the file. By design, Python installs to a directory with the version number embedded, e.g. Typing the full path name for a Python interpreter each time quickly gets tedious, so add the directories for your default Python version to the PATH. C:\Python27\;C:\Python27\Scripts\ You can do this easily by running the following in powershell: [Environment]::SetEnvironmentVariable("Path", "$env:Path;C:\Python27\;C:\Python27\Scripts\", "User") The second (Scripts) directory receives command files when certain packages are installed, so it is a very useful addition. Setuptools + Pip You’ll now have a new command available to you: easy_install. Virtual Environments



-------------------------------------------------------------------------------------------------------------------------------------------------------------------
2025-08-03 18:59
by raviii Aug 4
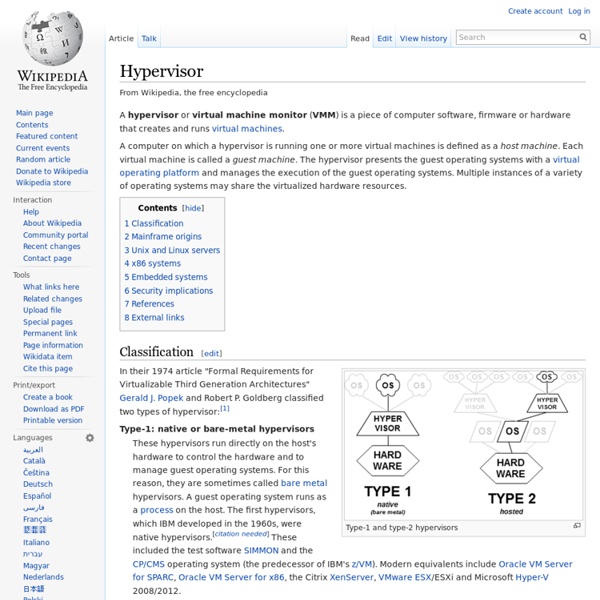
Hypervisor: Hardware that allows multiple operating systems to share a single host. The hypervisor sits at the lowest levels of the hardware environment and uses a thin layer of code in software to enable dynamic resource sharing. The hypervisor makes it seem like each operating system has the resources all to itself.
Found in: Hurwitz, J., Nugent, A., Halper, F. & Kaufman, M. (2013) Big Data For Dummies. Hoboken, New Jersey, United States of America: For Dummies. ISBN: 9781118504222. by raviii Jan 1