


How TCP/IP Works When transmitting data, the Transport layer gets data from the Application layer and divides them into several data packets. TCP (Transmission Control Protocol) is the most used protocol on the Transport layer. When receiving data, TCP protocol gets the packets sent by the Internet layer and put them in order, because packets can arrive at the destination out-of-order, and also checks if the contents of the received packet are intact and sends an acknowledge signal to the transmitter, allowing it to know that the packet arrived intact at destination. While TCP re-orders packets and also uses this acknowledge system we mention, which is desirable when transmitting data, there is another protocol that works on this layer that does not have these two features. Thus TCP is considered a reliable protocol, while UDP is considered an unreliable protocol. Both UDP and TCP will get the data from the Application layer and add a header to it when transmitting data.
POST Internet Governance as U.S. Relinquishes Control of ICANN The Department of Commerce announced on March 14 that it will give up its last bit of control of the Internet Corporation for Assigned Names and Numbers (ICANN) in 2015. As is often the case with government decisions announced late on a Friday, this decision is controversial. The U.S. has exercised light oversight of ICANN since it established the organization and emphasized the need for a free and open Internet. Other nations do not share America’s perspective and have sought repeatedly to work through U.N. organizations such as the International Telecommunication Union (ITU) to constrain and censor the Internet. America’s oversight of ICANN has provided a bulwark against these efforts. ICANN’s Role in Internet Governance ICANN is a U.S. nonprofit corporation established in 1998 to manage the Internet’s domain name system (DNS). Trouble Ahead Details of the structure of this successor institution are scarce. American Leadership Vital to Sustaining Internet Freedom —Brett D.
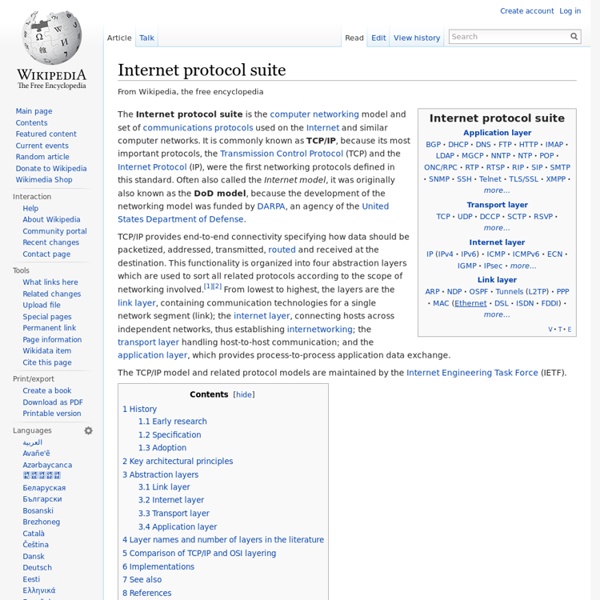
Computer Networking Computer networks differ in the physical media used to transmit their signals, the communications protocols to organize network traffic, the network's size, topology and organizational intent. In most cases, communications protocols are layered on (i.e. work using) other more specific or more general communications protocols, except for the physical layer that directly deals with the physical media. Computer networks support applications such as access to the World Wide Web, shared use of application and storage servers, printers, and fax machines, and use of email and instant messaging applications. History[edit] A computer network, or simply a network, is a collection of computers and other hardware components interconnected by communication channels that allow sharing of resources and information. Today, computer networks are the core of modern communication. The following is a chronology of significant computer network developments: Properties[edit] Network packet[edit]
GET NET NEUTRALITY: definition Definition of Net Neutrality Simply put, net neutrality is a network design paradigm that argues for broadband network providers to be completely detached from what information is sent over their networks. In essence, it argues that no bit of information should be prioritized over another. This principle implies that an information network such as the internet is most efficient and useful to the public when it is less focused on a particular audience and instead attentive to multiple users. To draw a simple example, take two content providers such as the Verizon website and the University of California website. The overall story of net neutrality is summed up nicely in this video: Origins The neutrality principle did not originate nor is it limited to the internet. This essentially stated that all messages transmitted must be transmitted in the order in which they were received and cannot be subject to discrimination.
Communications protocol In telecommunications, a communications protocol is a system of digital rules for data exchange within or between computers. In computer science, when data is exchanged through a computer network, the rules system is called a network protocol. Communicating systems use well-defined formats for exchanging messages. Each message has an exact meaning intended to provoke a particular response of the receiver. Thus, a protocol must define the syntax, semantics, and synchronization of communication; the specified behavior is typically independent of how it is to be implemented. A protocol can therefore be implemented as hardware, software, or both. Communicating systems[edit] In digital computing systems, the rules can be expressed by algorithms and data structures. Operating systems usually consist of a set of cooperating processes that manipulate shared data to communicate with each other. Systems typically do not use a single protocol to handle a transmission. Formal specification[edit]
Requests How Domain Name Servers Work" If you've ever used the Internet, it's a good bet that you've used the Domain Name System, or DNS, even without realizing it. DNS is a protocol within the set of standards for how computers exchange data on the Internet and on many private networks, known as the TCP/IP protocol suite. Its basic job is to turn a user-friendly domain name like "howstuffworks.com" into an Internet Protocol (IP) address like 70.42.251.42 that computers use to identify each other on the network. Computers and other network devices on the Internet use an IP address to route your request to the site you're trying to reach. Whether you're accessing a Web site or sending e-mail, your computer uses a DNS server to look up the domain name you're trying to access. You can always bypass a DNS lookup by entering 70.42.251.42 directly in your browser (give it a try). Without DNS servers, the Internet would shut down very quickly. So far, you've read about some important DNS basics.
The TCP/IP Guide I know everyone hates ads. But please understand that I am providing premium content for free that takes hundreds of hours of time to research and write. I don't want to go to a pay-only model like some sites, but when more and more people block ads, I end up working for free. And I have a family to support, just like you. :) If you like The TCP/IP Guide, please consider the download version. If you want to use this site for free, I'd be grateful if you could add the site to the whitelist for Adblock. Thanks for your understanding! Sincerely, Charles Kozierok Author and Publisher, The TCP/IP Guide Stateless protocol Examples of stateless protocols include the Internet Protocol (IP) which is the foundation for the Internet, and the Hypertext Transfer Protocol (HTTP) which is the foundation of data communication for the World Wide Web. Advantages and disadvantages[edit] The stateless design simplifies the server design because there is no need to dynamically allocate storage to deal with conversations in progress. A disadvantage of statelessness is that it may be necessary to include additional information in every request, and this extra information will need to be interpreted by the server. Examples[edit] An example of a stateless protocol is HTTP.[1] The protocol provides no means of storing a user's data between requests. Contrast this with a traditional FTP server that conducts an interactive session with the user. Stacking of stateless and stateful protocol layers[edit] There can be complex interactions between stateful and stateless protocols among different protocol layers. See also[edit]
Out with the Old: As Internet Addresses Run Out, the Next-Generation Protocols Step Up After years of warnings that the Internet's predominant addressing system would run out of these numbers, the bottom of the barrel has finally been scraped. The Internet Assigned Numbers Authority (IANA) announced Thursday that it has delegated the final 300 million addresses available through version 4 of the Internet protocol (IPv4) to the five Regional Internet Registries. These RIRs will over the next few years assign these remaining addresses to new Internet-connected computers, smart phones, televisions and other devices worldwide The distribution of IPv4's remaining addresses could be described as "one of the most important days in the Internet's history," Rod Beckstrom, president and CEO of the Internet Corporation for Assigned Names and Numbers (ICANN), said at a press conference commemorating the announcement. (ICANN operates the IANA.) "So the ISPs didn't implement IPv6 even though the operating system vendors and router vendors did implement the protocol," Cerf says.
Types of Network Protocols What is a Network Protocol A protocol is a set of rules that govern the communications between computers on a network. These rules include guidelines that regulate the following characteristics of a network: access method, allowed physical topologies, types of cabling, and speed of data transfer. Types of Network Protocols The most common network protocols are: Ethernet Local Talk Token Ring FDDI ATM The followings are some commonly used network symbols to draw different kinds of network protocols. Ethernet The Ethernet protocol is by far the most widely used one. The Ethernet protocol allows for linear bus, star, or tree topologies. Fast Ethernet To allow for an increased speed of transmission, the Ethernet protocol has developed a new standard that supports 100 Mbps. Local Talk Local Talk is a network protocol that was developed by Apple Computer, Inc. for Macintosh computers. The Local Talk protocol allows for linear bus, star, or tree topologies using twisted pair cable. Token Ring
Internet Protocol This article is about the IP network protocol only. For Internet architecture or other protocols, see Internet protocol suite. The Internet Protocol (IP) is the principal communications protocol in the Internet protocol suite for relaying datagrams across network boundaries. Its routing function enables internetworking, and essentially establishes the Internet. Historically, IP was the connectionless datagram service in the original Transmission Control Program introduced by Vint Cerf and Bob Kahn in 1974; the other being the connection-oriented Transmission Control Protocol (TCP). The Internet protocol suite is therefore often referred to as TCP/IP. The first major version of IP, Internet Protocol Version 4 (IPv4), is the dominant protocol of the Internet. Function[edit] The Internet Protocol is responsible for addressing hosts and for routing datagrams (packets) from a source host to a destination host across one or more IP networks. Datagram construction[edit] Reliability[edit]