


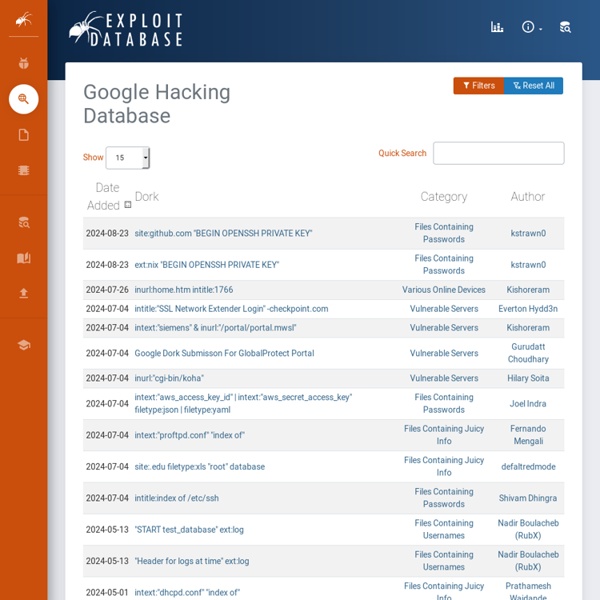
https://www.exploit-db.com/google-hacking-database
Related: Hacking && Hackers && (H)ac(k)tivism • Kali Linux • SecurityNcrack [RDP Bruteforce] Ncrack is a high-speed network authentication cracking tool. It was built to help companies secure their networks by proactively testing all their hosts and networking devices for poor passwords. Security professionals also rely on Ncrack when auditing their clients. Ncrack was designed using a modular approach, a command-line syntax similar to Nmap and a dynamic engine that can adapt its behaviour based on network feedback. It allows for rapid, yet reliable large-scale auditing of multiple hosts.
John the Ripper password cracker John the Ripper is free and Open Source software, distributed primarily in source code form. If you would rather use a commercial product, please consider John the Ripper Pro, which is distributed primarily in the form of "native" packages for the target operating systems and in general is meant to be easier to install and use while delivering optimal performance. To verify authenticity and integrity of your John the Ripper downloads, please use our GnuPG public key. Please refer to these pages on how to extract John the Ripper source code from the tar.gz and tar.xz archives and how to build (compile) John the Ripper core (for jumbo, please refer to instructions inside the archive). You may also consider the unofficial builds on the contributed resources list further down this page.
How to hack a router remotely - millions of routers still vulnerable 2016 A router is a gateway that connects a device to the internet with certain protocols. Hacking a router can be really serious, the attacker can take control over the whole network setup. Even in this 2016 millions routers are vulnerable to remote authentication.
Download the Free Nmap Security Scanner for Linux/Mac/Windows Nmap and Zenmap (the graphical front end) are available in several versions and formats. Recent source releases and binary packages are described below. Older version (and sometimes newer test releases) are available from the dist directory (and really old ones are in dist-old). For the more security-paranoid (smart) users, GPG detached signatures and SHA-1 hashes for each release are available in the sigs directory (verification instructions). Before downloading, be sure to read the relevant sections for your platform from the Nmap Install Guide. The most important changes (features, bugfixes, etc) in each Nmap version are described in the Changelog.
20 Popular Wireless Hacking Tools Last year, I wrote an article covering popular wireless hacking tools to crack or recover password of wireless network. We added 13 tools in that article which were popular and work great. Now I am updating that post to add few more in that list. I will not explain about wireless security and WPA/WEP.In this post, I am updating the existing list to add few more powerful tools. I am adding seven new tools in the existing list to give you a single list of the most used wireless cracking tools. Near Field Communication (NFC) Technology, Vulnerabilities and Principal Attack Schema - Infosec Resources The Near Field Communication (NFC) is a set of standards for mobile devices designed to establish radio communication with each other by being touched together or brought within a short distance. The NFC standard regulates a radio technology that allows two devices to communicate when they are in close proximity, usually no more than a few centimeters, allowing the secure exchange of information. NFC standards are based on different communications protocols and data exchange formats, and include also existing radio-frequency identification (RFID) standards such as the ISO/IEC 14443 specific for identification cards, proximity cards and contactless integrated circuit cards. The coverage of various ISO standards ensures for NFC technology the global interoperability that makes the technology usable in different areas. Figure 1 – NFC standards The NFC technology could be very effective in various areas.
Gridlock Sparrows Gridlock There is a reason as to why a coat hanger is the tool of choice for most Automobile lockouts.Picking a standard 10 wafer Automotive lock is a Huge challenge. Most often it is achieved by being stubborn with a pinch of lucky a dash of skill. The Gridlock set lets you develop that skill by working through three automotive locks of ever increasing difficulty.Building from a 3 to a 6 to a full 10 wafer Automotive lock will allow you to develop the skill for picking wafers.Wafer picking is an entirely different skill set when compared to pin tumbler picking. A standard pin tumbler key is cut just along the top to lift the pins up into place letting you open the lock.A wafer lock key is cut on the top and bottom, this then moves the wafers Up and Down positioning them for the lock to open.
WebGoat - Learn the hack - Stop the attack Learn the hack - Stop the attack WebGoat is a deliberately insecure application that allows interested developers just like you to test vulnerabilities commonly found in Java-based applications that use common and popular open source components. Description Neutralize ME firmware on SandyBridge and IvyBridge platforms Author: persmule Mail: persmule@tya.email, persmule@gmail.com 00 ME: Management Engine First introduced in Intel’s 965 Express Chipset Family, the Intel Management Engine (ME) is a separate computing environment physically located in the (G)MCH chip (for Core 2 family CPUs which is separate from the northbridge), or PCH chip replacing ICH(for Core i3/i5/i7 which is integrated with northbridge).
Bus Pirate From DP Bus Pirate v3.6 available now for $30.15, including worldwide shipping Bus Pirate v3.6 is also available at Adafruit Industries (USA) EpicTinker (USA) Watterott Electronic (Germany) Evola (Europe) Anibit (USA) Hackaday (USA) The Bus Pirate is an open source hacker multi-tool that talks to electronic stuff. It's got a bunch of features an intrepid hacker might need to prototype their next project.
Free Steganography Software - QuickStego Free Steganography Software - QuickStego What is Steganography? Steganography is the science of writing hidden messages in such a way that no one apart from the sender and intended recipient even realizes there is a hidden message. An Example of Image Steganography ...