


LookDisk: All-in-1 Search Tool With Text, Archive & Duplicate Lookups Previously, we have covered some very useful tools for quickly searching through files and folder by defining certain criteria and specifying parameters, such as UltraFileSearch and SearchMyFiles , and applications that allow you to search and delete duplicate files and folder on your system, like NoDupe . Today, we have a portable tool for you, called that combines both these functions and allows you to search duplicate files, files and folder using filters, such as file size, date and attributes, search for text in any file including PDF, displays the disk overview and search within multiple archive formats. More on LookDisk after the break. The application has four searching modes separated by tabs given on the left side of the main interface. Search for duplicate files by name or content Search for files using various parameters (file size, date, attributes) Search for a text in any file (also within PDF Files) Display disk overview (total size, free space) Download LookDIsk
5 Killer Tricks to Get the Most Out of Wireshark Wireshark has quite a few tricks up its sleeve, from capturing remote traffic to creating firewall rules based on captured packets. Read on for some more advanced tips if you want to use Wireshark like a pro. We’ve already covered basic usage of Wireshark, so be sure to read our original article for an introduction to this powerful network analysis tool. Network Name Resolution While capturing packets, you might be annoyed that Wireshark only displays IP addresses. Wireshark can automatically resolve these IP address to domain names, although this feature isn’t enabled by default. You can enable this setting by opening the preferences window from Edit -> Preferences, clicking the Name Resolution panel and clicking the “Enable Network Name Resolution” check box. Start Capturing Automatically You can create a special shortcut using Wirshark’s command-line arguments if you want to start capturing packets without delay. wireshark -i # -k Capturing Traffic From Remote Computers
How Secure Is My Password? Entries are 100% secure and not stored in any way or shared with anyone. Period. As Seen On Passwords are the bloodline of data and online security, but our research on the password habits in the U.S. shows that less than half of Americans feel confident that their password is secure. Pro Tip: We recently rolled out a new password generator tool that will help you create super secure passwords in a snap! How To Create Secure Passwords If you weren’t satisfied in your password strength rating, it’s time to create new and stronger passwords. Why Is Password Security Important? Not having secure passwords has its consequences, which include but are not limited to: After gaining access to a user’s credentials, many hackers will log into their accounts to steal more of their personally identifiable information (PII) like their names, addresses, and bank account information. The Impact of Stolen Passwords Impact on Businesses Impact on Consumers Other Ways To Protect Yourself Online
CRegistry Comparison: See Changes To System Registry Over Certain Time CRegistry Comparison is an open source registry comparison application for keeping an eye on registry changes. You can use this tool to check for changes that may have been made by newly installed applications (to the system registry), and identify unwanted changes. This application creates a .CRE registry file and enables comparison of two files. Furthermore, you can also save changes to a text file. When the application is run for the first time, it creates a registry compare file on your desktop for future reference. Once done, your system will be scanned and updates for registry changes will be detected. To compare registry changes, click Start Compare. CRegistry Comparison works on Windows XP, Windows Vista, Windows 7, Windows Server 2003 and Windows Server 2008. Download CRegistry Comparison Advertisement
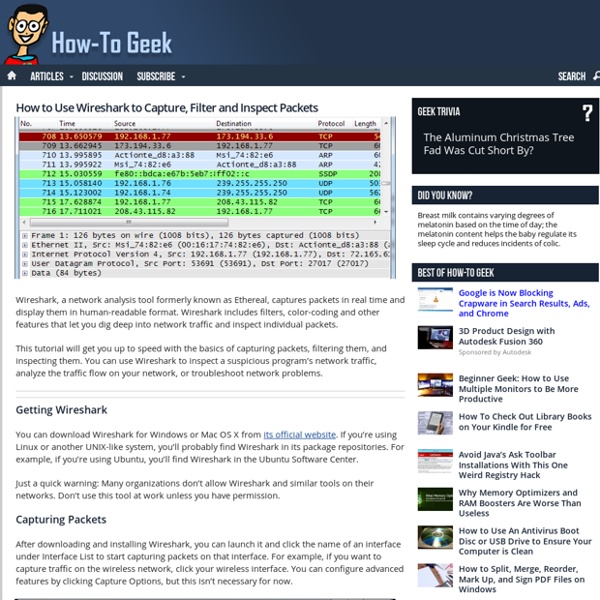
Wireshark tutorial: How to sniff network traffic In this Wireshark tutorial, Mike Chapple explains how to sniff network traffic and how to learn if your enterprise's... By submitting your personal information, you agree to receive emails regarding relevant products and special offers from TechTarget and its partners. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy. network security is lacking. Wireshark, formerly known as Ethereal, is one of the most powerful tools in a network security analyst's toolkit. How to sniff network traffic and why sniff the network? The phrase "sniff the network" may conjure Orwellian visions of a Big Brother network administrator reading people's private email messages. However, as a security professional, there are two important reasons to sniff network traffic. Wireshark how-to: Installing Wireshark Installing Wireshark is a piece of cake. Running a simple packet capture
Understanding and selecting authentication methods If you are serious about computer/network security, then you must have a solid understanding of authentication methods. Debra Littlejohn Shinder takes a moment to lay out the role authentication plays in a security plan. Computer/network security hinges on two very simple goals:Keeping unauthorized persons from gaining access to resourcesEnsuring that authorized persons can access the resources they needThere are a number of components involved in accomplishing these objectives. Access permissions, however, work only if you are able to verify the identity of the user who is attempting to access the resources. Authentication and securityAuthentication is an absolutely essential element of a typical security model. Authentication vs. authorizationIt is easy to confuse authentication with another element of the security plan: authorization. Another example of authorization is the Dialed Number Identification Service (DNIS), which authorizes a dial-in connection based on the number called.
Order Ordering Total Commander Total Commander is a Shareware program. This means that you can test it for a period of 30 days. After testing the program, you must either order the full version, or delete the program from your harddisk. When you register, you receive the latest version on CD, plus a quick reference card with an overview of all Total Commander functions and keystrokes.A personal licence costs 40 Swiss Francs (CHF) including shipping&handling (US$ 44 online).The price in US-Dollars is now US$ 44 (multiply price in CHF with 1.10)The price in EURO is EUR 32.- (multiply price in CHF with 0.8)Pupils and Students with identity card or other proof can get the software at a reduced price (30 instead of 40 Swiss Francs, EUR 24 or US$ 34.50). The program must be registered to the student's name. To order the full version, you have the following options: After registration, all future updates can be downloaded for free from this page (until further notice).
XXCLONE: Backup System Volumes While Retaining Self Boot Functionality Backup for system volumes can be performed with a number of applications. However, retaining the self-booting functionality of a volume can be difficult to achieve using conventional tools. XXCLONE is an application for copying your system volume to another, while retaining self-booting functionality. Using this application, you can even boot your system from the clone volume by swapping the disks. This can be particularly useful for disaster recovery, when the primary volume may have become redundant. To clone disk, select a source and destination volume and select a backup mode (backup the entire volume by copying all files from scratch, backup incrementally, backup Windows key directories or transfer system registry without file backup). You will be provided with a warning message, and informed if your selected backup mode will delete the data in the destination drive. XXCLONE works on Windows XP, Windows Vista, Windows 7, Windows Server 2003 and Windows Server 2008. Download XXCLONE
Monitor & Export Registry Changes Made By A Process Using RegFromApp Windows Registry is an operating system database that stores the configuration settings in Windows. It contains settings for operating system components, as well as information about hardware. In fact, every application you install on your PC, gets registered in the registry. Just like you’d keep a written record of your finances on a physical register, Windows registry works pretty much the same. One thing that is common among all NirSoft tools is their simple and minimalistic design, and the statement holds true for this application as well. Once a process is selected, any changes made by it to the registry are noted in RegFromApp’s window. RegFromApp, despite being its schematic design is both powerful and feature-rich, much like to NirSoft’s other tools. Download RegFromApp Advertisement
Send/Receive Large Files With Group & Speed Management Using Share File sharing has become pleasantly easy within the past few years, especially as we now have extremely fast internet connections. Various web services and desktop clients let you share your images, videos, documents and other files, with one another, within a few clicks. One such example is P2P (Peer-to-peer) clients, which connect people through internet via server and client relation. Sometime ago, we covered zeZebra, an application with eye candy interface that let you transfer large files in a very simple way. The only downside of zeZebra is that when you send a file to someone, it prompts the recipient to download and install the application before the file transfer can begin. After installation, the application will quietly sit in your system tray. The recipient will receive an email with a link to the file. To download the file, click on Download Share to start the download process. Share works on both 32-bit and 64-bit versions of Windows XP, Windows Vista and Windows 7.
20 Best Globally Renowned Online Time Tracking Software Tools For any business house, time is money and the rapid and sturdy technological advancements have provided the users with ample number of options to creatively and effectively manage their time online. The present day has witnessed the rise in the availability of a number of time tracking software, however to ease out your search for the best solution, we provide you with a comprehensive list of top twenty most amazing online time tracking software. 1. Invoicera It is amongst the most popular online time tracking solution available globally to different clients. Its sturdy support for multiple language and multiple currencies, is an extra added advantage to the users. 2. Do not judge the Freshbooks with its looks. 3. Dovico is a Canada based company which provides highly modernized and up to date time tracking services online at very competitive prices. 4. If you get intimidated and bugged by unfriendly user interfaces, Harvest is the tailor made solutions for you. 5. 6. 7. 8. 9. 10. 11.
FolderUsage Lets You View & Manage Folder Size Using Filters You will find a lot of tools, such as Folder Size, TDP x-Ray Lite and OverDisk, to check the size of folders and distribution of disk space to view and manage hard disk contents. All of them displayed size and contents of each folder in beautiful and easy-to-understand pie charts, and allowed you to export chart images. FolderUsage is a portable application to view the size and contents of folders according to Name, Size, Number of Files and Number of Folders. It allows you to view the file and folder size in Bytes, Kilobytes, Megabytes and Gigabytes. The application automatically highlights the folders without any file or folder in them, allowing you to easily delete empty folders. To start using the application, click the Browse button available on the right side, and navigate to the desired folder. To delete files, select single or multiple files, right-click and select Delete Files from the context menu. Download FolderUsage Advertisement
inCrypto Lets You Generate Hash Values And Encode & Encrypt Text Encrypting a file allows you to send it over the internet safely without worrying about its contents being read, or used by someone who is not intended to read them. for instance, a file that you upload on the internet might get hacked by someone with malicious intentions. If the file contains sensitive information, that can create a lot of trouble for you. Hashing a file, on the other hand, can be used to make sure that the file you downloaded is exactly the one that was uploaded by the author and not a file modified by a hacker. Developers often post the hash value along with the uploaded file, so that anyone downloading it can be sure that it is the same file that was originally uploaded by the author. Previously, we have covered a lot of tools, such as SFV Ninja, a portable hash value generator, that can be used to generate and compare hash values of files in order to verify their integrity. Donwload inCrypto Advertisement
Start Windows Programs Using Keyboard Hotkeys With MadApp Launcher The beauty of Windows operating system is the amount of customization features it provides, both aesthetically and ergonomically. Talking about ergonomics, there are various ways to make your applications and utilities easily accessible. Even though you can use desktop shortcuts to make your applications easy to approach, the other way is to use App Launchers. App launchers are applications that are designed to hold your frequently used tools and apps at one place. Instead of browsing through directories or cluttering your desktop with shortcuts, the easier method is to use launchers, which keep things more minimalistic and less cluttered. There are many application launchers available including Gizmo Toolbar or OldBar, just to name a few, that add application shortcut toolbars on your desktop, allowing quick access to your favorite and frequently visited applications. There isn’t much to applaud regarding the overall presentation and the tool comprise of quite a simple design.