


Forensic Tools Listings Pyext The ext3 or third extended filesystem is a journaled file system that is commonly used by the Linux kernel. It is the default file system for many popular Linux distributions. Stephen Tweedie first revealed that he was working on extending ext2 in Journaling the Linux ext2fs Filesystem in a 1998 paper and later in a February 1999 kernel mailing list posting, and the filesystem was merged with the mainline Linux kernel in November 2001 from 2.4.15 onward. Tspoofer This tool is programmed in Python so you'll need a Python interpreter which is pretty usual on Linux boxes but not in Windows. Qforegsics A qt4 app that visualizes on disk registry hives. Trisul Trisul is a flexible network traffic monitor. Prefetch-tool Script to extract information from windows prefetch folder (forensics use). Revealer web access Revealer Web Access (RWA) is a frontend web application designed to use and manage the Revealer Toolkit (RVT) computer forensics software. JDBCgrabber Forensie Vol2html dd lsof
Book Review: Digital Forensics with Open Source Tools | Forensic Methods With more forensic books hitting the shelves, I find myself prioritizing those by authors I know and trust. I have worked with Cory Altheide and he is an extremely talented forensic professional with a passion for open source tools. Not surprisingly, I would not categorize this as a beginner book. Open source tools require a higher level of interaction than their commercial counterparts, but are a great way to take your forensic skills to the next level. While teaching, I often see students frustrated that there is no one tool that can do it all. The book begins with an excellent section on setting up your forensic workstation, using either Linux or Windows as a host. Of course the coverage of open source tools is why many will buy this book. Overall, I found DFWOST to be a tremendous asset in an area with few published resources.
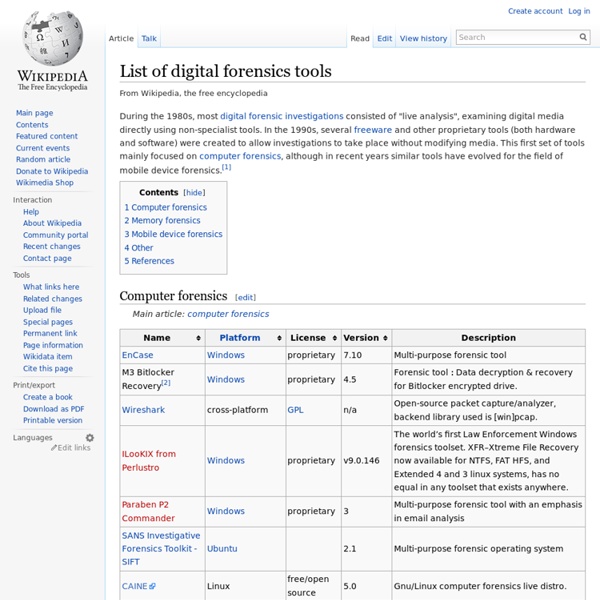
Top 20 Free Digital Forensic Investigation Tools for SysAdmins Digital forensics tools come in many categories, so the exact choice of tool depends on where and how you want to use it. Here are some broad categories to give you an idea of the variety that comes under the umbrella of digital forensics tools: Database forensicsEmail analysisAudio/video forensicsInternet browsing analysisNetwork forensicsMemory forensicsFile analysisDisk and data captureComputer forensicsDigital image forensics While this is not an exhaustive list, it gives you a picture of what constitutes digital forensics tools and what you can do with them. Sometimes multiple tools are packaged together into a single toolkit to help you tap into the potential of related tools. Also, it is important to note that these categories can get blurred at times depending on the skill set of the staff, the lab conditions, availability of equipment, existing laws, and contractual obligations. Choosing the right tool Skill level Output Cost Focus Additional accessories Key features 03 Volatility 17 HxD
Forensic Focus Live View Tech Insight: Making The Most Of Open-Source Forensics Tools Emerging offerings can turn network forensics into a low-cost, do-it-yourself security project A Special Analysis for Dark Reading Network forensic solutions come in many different shapes, sizes, and price ranges, but in the end they all have the same goal: recording activity on the network. As IT budgets tighten with the economy, it might be time for your organization to take a closer look at a do-it-yourself approach to forensics that leverages free and open-source tools. While your CFO might love the price of these tools, it may be difficult to "sell" them to your IT management. But don't let the support question turn you away. Making the case to build your own network forensics capabilities often means highlighting the shortcomings of your company's existing tools. Network forensic tools also fill in the blanks when performing internal investigations. Building a basic network forensic system -- including installing the software and deploying it -- can be accomplished quickly.
50 Essential Open Source Security Tools - Anti-Everything, Encryption, Secure Delete, Forensics - Roundup Anti-Everything, Encryption, Secure Delete, Forensics November 11, 2008 By Cynthia Harvey The area of open source security software is growing rapidly, with a cornucopia of apps for every use: anti-spam, firewalls, forensics, encryption, log monitoring, passwords – the list is growing even as you read this. In many cases, these open source security tools – many of which are free – are available for the Windows, Linux and Mac operating systems. Let the downloading begin… 1. Winner of multiple Datamation Product of the Year awards, SpamAssassin uses header and text analysis, Bayesian filtering, DNS blocklists, and collaborative filtering databases to block unwanted e-mail at the server level. Anti-Virus/Anti-Malware 2. This anti-virus toolkit is designed especially for protecting mail gateways and features a command line scanner, automatic updates, and more. 3. ClamWin provides a Windows front-end for the ClamAV antivirus toolkit. Application Firewall 4. 5. Data Destruction 6. 7. Encryption 8.
Public Intelligence Computer Forensics Book | PDF Free Digital evidence and computer forensics - university of, Title: microsoft powerpoint - digital evidence locations and computer forensics - judges conference apr 2-3 2012 [read-only] author: cherry created date. / incident response & computer forensics / prosise, Chapter 2 introduction to the incident response process 11 hacking / incident response & computer forensics / prosise & mandia / 222696-x / chapter 2. Ryan r. kubasiak, investigator - new york state police, Macintosh forensics a guide for the forensically sound examination of a macintosh computer ryan r. kubasiak, investigator - new york state police. Digital evidence and computer crime - elsevier store, Related titles by eoghan casey handbook of digital forensics and investigation edited by eoghan casey
Digital Corpora IRMA (I Reveal My Attributes) project | I Reveal My Attributes research project How to Visualize Investigations In security and investigations, the phrase "A picture is worth a thousand words" usually refers to CCTV footage or some evidence that proves a subject's guilt (or innocence). Unfortunately most corporate investigations rarely even touch upon cases with a lot of visual content, which can become rather large collections of three ring binders. While we all hope to present a smoking gun for our final report, sometimes presenting our case to law enforcement, lawyers, human resources and even our own management without the proper visual can keep even a solid case from closing. Like children's books full of images deeply expanding short story lines into memorable tales, visualization can be an effective way to quickly and successfully present your investigation on a high level. Also see Internal Investigations: The Basics My favorite tools, i2 Inc's Analyst's Notebook and their line of investigative analyst software, is the sports car to bring your investigations to life.
10 Data Recovery Tools You Can Download For Free [Windows] It happens to the best of us. We are working on that very important file when suddenly disaster strikes. It accidently gets deleted, corrupted, the computer died or a number of unfortunate things that prevent you from gaining access to the file. What’s worse, you don’t have a backup and are in desperate need of those important files urgently. Well, don’t fret as it is possible to recover those deleted files. Recommended Reading: 20+ Data Backup & Synchronization Tools For Hard Drives 1. PhotoRec is a powerful command line recovery tool that can recover your lost data by bypassing the file system, perfect for when your computer can see the drive but cannot access it or for use on a formatted drive. [Download here] 2. Recuva provides a number of tools and features that makes recovering your data easier. [Download here] 3. There are times when your drive’s file system will get damaged and you are unable to access the data within. 4. [Download here] 5. [Download here] 6. [Download here] 7. 8. 9.