


Absurdism Absurdism is very closely related to existentialism and nihilism and has its origins in the 19th century Danish philosopher Søren Kierkegaard, who chose to confront the crisis humans faced with the Absurd by developing existentialist philosophy.[3] Absurdism as a belief system was born of the European existentialist movement that ensued, specifically when the French Algerian philosopher and writer Albert Camus rejected certain aspects from that philosophical line of thought[4] and published his essay The Myth of Sisyphus. The aftermath of World War II provided the social environment that stimulated absurdist views and allowed for their popular development, especially in the devastated country of France. Overview[edit] "... in spite of or in defiance of the whole of existence he wills to be himself with it, to take it along, almost defying his torment. Relationship with existentialism and nihilism[edit] Related works by Søren Kierkegaard[edit] What is the Absurd? What, then, is the absurd?
Khokhmah and Sophia: the Judaic and Gnostic Goddess Wisdom goddesses are a primary survival of Goddess consciousness within patriarchal systems. In an intact Goddess cosmology, Wisdom is not sharply differentiated from other divine qualities. In that sense the separation is artificial, and typical of the divisions that arise when theologians erect their esoteric hegemonies. Khokhmah and Sophia Max Dashú The ancient Hebrew name for Wisdom is Khokhmah, a feminine noun. For in her there is a spirit that is intelligent, holy, unique, manifold, subtle; mobile, clear, unpolluted, distinct, invulnerable, loving the good, keen, irresistible, Beneficent, human, steadfast, sure, free from anxiety, all-powerful, overseeing all and penetrating through all spirits that are intelligent and pure and most subtle. Another beautiful passage likens Wisdom to “a flame of stars through the night.” I am Isis, mistress of every land I laid down laws for humanity and ordained things that no one may change... Thou art a Sophia.
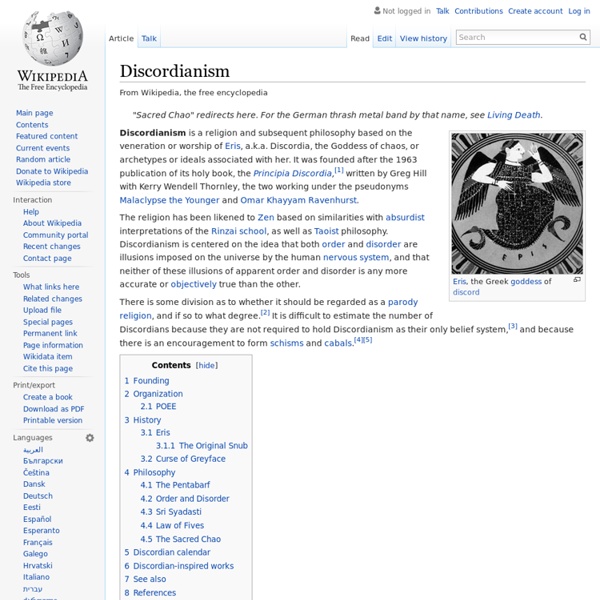
Parody religion A parody religion or mock religion is an imitation belief system that challenges spiritual convictions of others, often through humor, satire, and/or burlesque (literary ridicule). Often created to achieve a specific purpose related to another belief system, a parody religion can be a parody of several religions, sects, gurus, cults, and or new religious movements at the same time or a parody of no particular religion, instead parodying the concept of religious belief. In some parody religions, emphasis is on making fun and being a convenient excuse for pleasant social interaction among like-minded, e.g. the Church of the SubGenius. Other parody religions target a specific religion, sect, cult, or new religious movement. One approach to parody religion aims to highlight deficiencies in particular pro-religious arguments — the thinking being that if a given argument can also be used to support a clear parody, then the original argument is clearly flawed. Post-modern religions[edit] [edit]
Astrolabe The astrolabe is a device for solving problems relating to time and the position of the Sun and stars in the sky. Several types of astrolabes have been made. By far the most popular type is the planispheric astrolabe, on which the celestial sphere is projected onto the plane of the equator. The name astrolabe is derived by aster and lambanein, i.e., star and receive or get and means combined a device that finds a star. Astrolabes are used to show how the sky looks at a specific place at a given time. The most influential individual on the theory of the astrolabe projection was Hipparchus of Rhodes (called also Hipparchus of Nicaea or Hipparchus of Bithynia) (c. 190 – 120 BC) who was born in Nicaea in Asia Minor studied and worked on the island of Rhodes. The first major writer on the projection was the famous Claudius Ptolemy (ca. No one knows exactly when the stereographic projection was actually turned into the instrument we know today as the astrolabe. Miscellaneous The Astrolabe
Malaclypse the Younger Gregory Hill (21 May 1941 – 20 July 2000[1]), better known by the pen name Malaclypse the Younger, was one of the two writers of the Principia Discordia, along with Kerry Wendell Thornley (aka Lord Omar Khayyam Ravenhurst). He was also adapted as a character in The Illuminatus! Trilogy. Biography[edit] Robert Anton Wilson stated, in the lecture "The I in the Triangle" from 1990, that Greg Hill was at the time the head of a large computer facility owned by one of the largest banks in the United States.[2] Principia Discordia[edit] In 2006, a copy of the first edition of the Principia Discordia was claimed to have been discovered in the President John F. Possessing many titles, including "Omnibenevolent Polyfather of Virginity in Gold", Malaclypse's true identity or position within the Erisian religion is completely unknown. Very little is known about Malaclypse the Elder, the namesake of Mal-2. Illuminatus! Malaclypse the Younger also appears in The Illuminatus! Bibliography[edit]
Docorigin "Seeing that everybody, gods of the world and mankind, says that nothing existed prior to chaos, I, in distinction to them, shall demonstrate that they are all mistaken, because they are not acquainted with the origin of chaos, nor with its root. Here is the demonstration. How well it suits all men, on the subject of chaos, to say that it is a kind of darkness! But in fact it comes from a shadow, which has been called by the name 'darkness'. And the shadow comes from a product that has existed since the beginning. It is, moreover, clear that it existed before chaos came into being, and that the latter is posterior to the first product. After the natural structure of the immortal beings had completely developed out of the infinite, a likeness then emanated from Pistis (Faith); it is called Sophia (Wisdom). This describes Lucifer which in the Hebrew is: Heylel (h1966) hay-lale'; from 1984 (in the sense of brightness); the morning-star: - lucifer. Then his father called him Eee-a-o ('Yao').
GNOSTIC PAGAN HYMNS My words are tied in one with the great mountains, with the great rocks, with the great trees, in one with my body and my heart. All of you see me, one with this world. O great and Holy Goddess, I pray Thee by thy plenteous and liberal right hand, by the joyful ceremonies of thy harvest, by the secrets of thy Sacrifice, by the flying chariots of thy dragons, by the sowing of the ground gnosis thou hast invented on earth for thy children; by the marriage of Persephone, by the diligent wisdom and devotion of thy blessed daughter; and by the other secrets and devotions thou hast revealed to thy mortal followers, whose hands till the earth in love for Thee. Come to us here in this consecrated place, Deign to bless these rites with thy shinning face, Bless thy faithful Children with thy Holy Grace. O beautiful Ceres and Great Mother Isis are One! [Adapted from Psyche in Apuleius] [Remembered from the words of a Mountain Elder] Song of Bernadette There was a child named Bernadette 2000 C.E.
The Zoe Group - Music, Drama, Dance as Change Agent "Leah Taylor is a certified trainer for Corporate Scenes, Inc. and has worked with companies such as AT&T, Pacific Bell and Sandia Laboratories. Currently Ms Taylor is an adjunct faculty member at the University of San Francisco, teaching in the College of Professional Studies. She received her BS in Human Relations and organizational behavior from the University of San Francisco and completed an M.Ed. in Creative Arts and Learning, Theater Studies and Communications from Lesley College, Cambridge, MA. During her fifteen years experience as a successful business woman, theater artist and teacher she has led group sessions and individual tutorials at intensive residential training programs for teachers, actors and business professionals from South Africa, Canada, Germany, Ukraine, UK and the US. Sedonia Cahill is an experienced seminar teacher and trainer. A Testimonial: "My initial motivation for Wisdom Circles came during a vision quest led by Sedonia Cahill. Lynn Anderson writes:
Marcosians - Wikipedia, the free encyclopedia System[edit] Theory of letters[edit] Sometimes Marcus counts the number of letters in a name, sometimes he reckons up the sum total, when to each letter is given its value in the Greek arithmetical notation: sometimes he uses a method which enables him to find still deeper mysteries. Marcus points out that if we take a single letter, Δ, and write its name at full length, δέλτα, we get five letters; but we may write again the names of these at full length and get a number of letters more, and so on ad infinitum. If the mysteries contained in a single letter be thus infinite, what must be the immensity of those contained in the name of the Propator. Concerning this name he gives the following account:—When the first Father, who is above thought and without substance, willed the unspeakable to become spoken, and the invisible to become formed, He opened His mouth and emitted a Word like Himself, which being the form of the invisible, declared to Himself what He was. Tetrad[edit] Ἰησοῦς[edit]