


Free Windows Bootdisks, Free DOS boot disk 1.44 Boot Disks IDE CDrom Drivers Included DOS 5.0 | Mirror DOS 6.0 | Mirror DOS 6.21 | Mirror DOS 6.22 | Mirror1 | Mirror2 Windows 95 Original | Mirror1 | Mirror2 Windows 95 Version B | Mirror1 | Mirror2 Windows 98 OEM | Mirror1 | Mirror2 Windows 98 Custom, No Ramdrive | Mirror1 | Mirror2 Windows 98 SE OEM | Mirror1 | Mirror2 Windows 98 SE Custom, No Ramdrive | Mirror1 | Mirror2 Windows Me OEM | Mirror1 | Mirror2 Windows Me Custom, No Ramdrive | Mirror1 | Mirror2 NTFS Bootdisks And Bootable CDs Bootable Utility CD With 68 Programs For Both DOS And Windows. Setup Any Computer With Windows 98 or XP. Fix Just About Every Problem. Bootdisks - PC Support - Essential Utilities Bootdisk.Com
Dmitry’s PowerBlog PowerShell and beyond Free NTFS Bootdisk, NTFS4DOS, NTFS Boot CD DOS Drivers For Reading, Copying, And Writing To NTFS Drives I've assembled Two Methods for you to see and work with NTFS drives while in DOS or by booting with a DOS bootdisk or bootable CD. They may come in real handy if you need to save data or modify/add/delete/edit files on an NTFS Drive or Partition. Method 1 View, Copy, Write, And Edit Files On NTFS Drives Sometimes you need full Read AND Write access to NTFS drives if XP/NT is not booting in order to delete a file, replace a file, rename a file, or edit a file such as boot.ini or perhaps win.ini. This driver is called NTFS4DOS Personal and used to be a free download from Avira but it seems to be no nonger on their website. To that end I created an easier to make/use a 1.44 bootdisk and a Bootable CD .iso with some Important Directions and KEY additional utilities ADDED to let you use their driver to do what you need to do.
Windows Server 2008, Exchange advice. Help solving computer problems. VBScript Dependency Walker (depends.exe) Home Page Windows PowerShell Updated: July 8, 2013 Windows PowerShell® is a task-based command-line shell and scripting language designed especially for system administration. Built on the .NET Framework, Windows PowerShell® helps IT professionals and power users control and automate the administration of the Windows operating system and applications that run on Windows. The documents published here are written primarily for cmdlet, provider, and host application developers who require reference information about the APIs provided by Windows PowerShell. For the basic information needed to start using Windows PowerShell, see Getting Started with Windows PowerShell . Provides information about how to install the Windows PowerShell SDK. Provides information for administrators, script developers, and cmdlet developers who need to package and distribute their Windows PowerShell solutions. Provides information for designing and implementing cmdlets.
Bootdisk.Com QAD cmdlets reference - PowerGUI Wiki QAD cmdlets reference From PowerGUI Wiki Jump to: navigation, search The ActiveRoles Management Shell for Active Directory is an Active Directory specific automation and scripting shell that provides a command-line management interface for administering directory data either via Quest ActiveRoles Server or by directly accessing Active Directory domain controllers. The ActiveRoles Management Shell is built on Microsoft Windows PowerShell technology. This reference is for AD cmdlets version 1.4. You can download AD cmdlets here. The following cmdlets are currently in the package: Connecting to AD, domain controllers, ADAM Generic object management User management Group management Computer accounts AD security Email address management Windows 2008 fine-grained password policies Certificate and Public Key Infrastructure (PKI) management Auxiliary cmdlets Convert-QADAttributeValue ActiveRoles Server cmdlets Deprovision-QADUser Get-QARSLastOperation Category: QAD cmdlets reference Views Personal tools Home Forum
Ultimate Boot CD - Overview Running Windows PowerShell Scripts Against Multiple Computers Here’s a quick tip on working with Windows PowerShell. These are published every week for as long as we can come up with new tips. If you have a tip you’d like us to share or a question about how to do something, let us know. Find more tips in the Windows PowerShell Tip of the Week archive. Running Windows PowerShell Scripts Against Multiple Computers If there’s a problem with the Script Center – wait a minute, who said there was a problem with the Script Center? Um, as we were saying, if there’s a problem with the Script Center it’s the fact that our scripts are almost all designed to be run against one computer at a time. Yes, just like the Scripting Guys. Of course, in real life things aren’t so simple; system administrators (that is, people who actually use scripts, as opposed to simply writing about them) need to manage multiple machines. Well, to be honest, they don’t. But first things first. Using Command-Line Arguments bios.ps1 atl-fs-01 atl-fs-02 That’s pretty cool, isn’t it?
Ultimate Boot CD - Overview Windows PowerShell for Windows Server 2012 and Windows 8 Windows Server 2012 and Windows 8 Updated: March 25, 2014 Applies To: Windows 8, Windows Server 2012 This topic lists the Windows PowerShell® modules included with Windows Server® 2012 and Windows® 8. The Windows PowerShell modules in the list support automating the features of those operating systems and provide links to the cmdlet references for each module. For information about the core features common to all versions of Windows PowerShell, see Windows PowerShell Core.
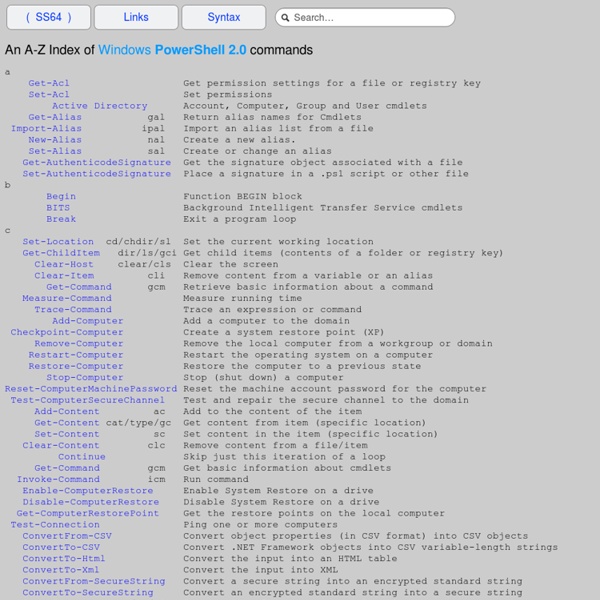
10 Essential Cheat Sheets To Download | MakeUseOf.com Advertisement Ever wanted to master the keyboard shortcuts and get more productive on the web? Here is everything you need – 10 quick cheat sheets for some of the most widely used tools on the web. Download, print and stick them somewhere near your desk. UPDATE: Hey folks, due to massive response the download links to above cheat sheets were moved to our must-have downloads page which is only available to MakeUseOf subscribers. We have over 65.000 subscribers so you have nothing to worry about. Plus, as a MakeUseOf subscriber you’ll also get regular updates about new cool websites and free software programs we come across. We notice you're using an adblocker. I've whitelisted MakeUseOf. Not now. We hate spam as much as you do!