


NSA pays tech companies millions to engineer backdoors into encryption protocols (NaturalNews) There is a saying that says, when it comes to government, they've got you coming and going. No truer words are spoken when the subject comes to serial invasions of your privacy. Not only is the National Security Agency monitoring your every electronic communication, but the agency is paying your tech company and Internet service provider to hack you as well. According to Britain's The Guardian newspaper, which broke the story of massive NSA spying earlier this year: U.S. and British intelligence agencies have successfully cracked much of the online encryption relied upon by hundreds of millions of people to protect the privacy of their personal data, online transactions and emails, according to top-secret documents revealed by former contractor Edward Snowden. If need be, the use of 'brute force' to break encryption In other words, those little privacy spiels that social media and tech companies put on their sites to "assure you" that your privacy is "guaranteed" - are lies.
The Day We Fight Back - February 11th 2014 Smart Lights: New LEDS Allow NSA To Spy On Your Every Movement Galactic Connection UFO | Ascension | Conspiracy | Spirituality Smart Lights: New LEDS Allow NSA To Spy On Your Every Movement Fri, July 4, 2014 Like this: Like Loading... Related : 2014, Conspiracy, Cabal, and Government, Science and Technology Comments are closed. RSS feed for this post (comments) Previous Post« A “Phone Call” with SaLuSa Next Post‘Right to be forgotten’ is just latest of West’s delusions » Calotropis Theme designed by itx Warning: stripslashes() expects parameter 1 to be string, array given in /home/renoman/public_html/galacticconnection.com/wp-content/plugins/frame-webstore-shopping-cart-toolbar/framewebstore.php on line 79 %d bloggers like this:
BREAKING: Maryland Legislators Move To Kill NSA Headquarters NSA National Headquarters ANNAPOLIS, Md., February 10, 2014– It’s lights out for the National Security Agency (NSA). State lawmakers in Maryland have filed emergency status legislation that seeks to cut the NSA’s Ft. Meade headquarters off from all material support stemming from the state. “Maryland has almost become a political subdivision of the NSA,” Tenth Amendment Center Executive Director Michael Boldin said in a statement. House Bill 1074 (HB1074) would ban the NSA facility from all public state utilities, ban the use of NSA collected evidence in court, ban universities from partnering with the NSA and ban all political subdivisions from assisting the NSA from within the state. Any state entity, employee or contractor refusing to comply with the law would be immediately fired and banned from all future contracts within the state. The bill has eight Republican sponsors and has been referred to the House Judiciary Committee. So far, the Maryland and Tennessee (sponsored by Sen.
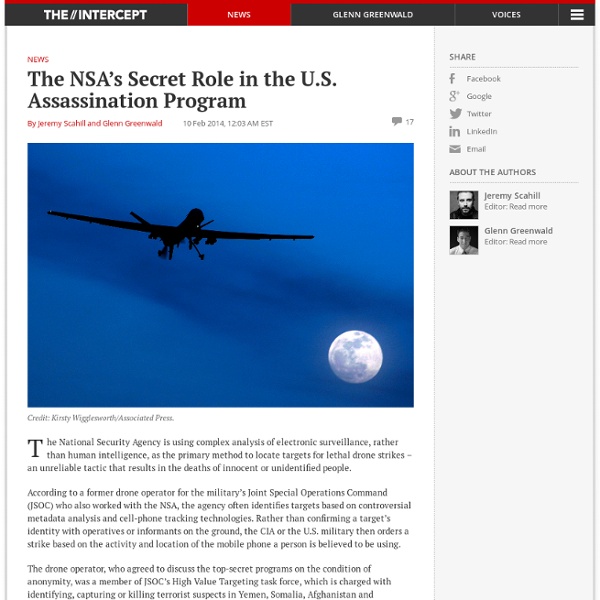
Snowden leak: NSA plans to infect ‘millions’ of computers (Thanks to Cheryl for a head’s up on potential virus bombardment!-A.M.)Published time: March 12, 2014 17:22 Edited time: March 13, 2014 08:34 The Threat Operations Center inside the National Security Agency (NSA) (AFP Photo) Yet more previously secret surveillance operations waged by the United States National Security Agency were made public Wednesday morning thanks to leaked documents supplied by former NSA contractor Edward Snowden. The files — published first by The Intercept this week and dissected over the course of a 3,000-word article attributed to journalists Glenn Greenwald and Ryan Gallagher — bring to light a number of previously unreported programs undertaken by the secretive US spy agency, including operations that have given the NSA the potential to infect millions of computers around the world by relying on malicious software that’s sent to targets through surreptitious means. NSA presentation from theintercept.com Related
How the NSA (may have) put a backdoor in RSA’s cryptography: A technical primer There has been a lot of news lately about nefarious-sounding backdoors being inserted into cryptographic standards and toolkits. One algorithm, a pseudo-random bit generator, Dual_EC_DRBG, was ratified by the National Institute of Standards and Technology (NIST) in 2007 and is attracting a lot of attention for having a potential backdoor. This is the algorithm into which the NSA allegedly inserted a backdoor and then paid RSA to use. So how is that possible? Backdoors The concept of a backdoor has cast a shadow over the security industry for a long time. Backdoors can be inserted by lazy programmers who want to bypass their own security systems for debugging reasons, or they can be created to intentionally weaken a system used by others. In theory, a well-designed cryptographic system does not include a backdoor. Open source is great tool for understanding how code works but it is not a cure-all for finding backdoors in software. Random weakness A random stream that isn't Looking Ahead
How the NSA's Domestic Spying Program Works %3Ciframe%20src%3D%22%2F%2Fwww.youtube-nocookie.com%2Fembed%2F_P1NA29X7Mw%3Frel%3D0%26autoplay%3D1%26mute%3D1%22%20allowfullscreen%3D%22%22%20frameborder%3D%220%22%20height%3D%22315%22%20width%3D%22560%22%20allow%3D%22autoplay%22%3E%3C%2Fiframe%3E Privacy info.This embed will serve content from youtube-nocookie.com The NSA’s domestic spying program, known in official government documents as the “President’s Surveillance Program,” ("The Program") was implemented by President George W. Bush shortly after the attacks on September 11, 2001. Our NSA Domestic Spying Timeline has a full list of important dates, events, and reports, but we also want to explain—to the extent we understand it—the full scope of the Program and how the government has implemented it. In the weeks after 9/11, President Bush authorized the National Security Agency (NSA) to conduct a range of surveillance activities inside the United States, which had been barred by law and agency policy for decades.
Catalog Reveals NSA Has Back Doors for Numerous Devices Editor's note: This article accompanies our main feature story on the NSA's Tailored Access Operations unit. You can read it here. When it comes to modern firewalls for corporate computer networks, the world's second largest network equipment manufacturer doesn't skimp on praising its own work. A 50-Page Catalog These NSA agents, who specialize in secret back doors, are able to keep an eye on all levels of our digital lives -- from computing centers to individual computers, and from laptops to mobile phones. This, at least, is the impression gained from flipping through the 50-page document. In the case of Juniper, the name of this particular digital lock pick is "FEEDTROUGH." Master Carpenters The specialists at ANT, which presumably stands for Advanced or Access Network Technology, could be described as master carpenters for the NSA's department for Tailored Access Operations (TAO). Some of the equipment available is quite inexpensive. 'Persistence'
NSA Cyber War Will Use Internet of Things as Weapons Platform; Your Home is the Battlefield Old-Thinker News | January 19, 2015 By Daniel Taylor “World War III is a guerrilla information war with no division between military and civilian participation.” – Marshall McLuhan, Culture is Our Business, 1970 New Snowden documents recently revealed that the NSA is getting ready for future digital wars as the agency postures itself in an aggressive manner towards the world. “The Five Eyes Alliance“, a cooperation between United States, Canada, Britain, Australia, and New Zealand, is working hard to develop these weapons of Cyber Warfare. So called “D” weapons, as reported by Der Spiegel, will paralyze computer networks and infrastructure that they monitor. The Der Spiegel report does not mention the wider issue of the expanding network of everyday objects and appliances that are connected to the internet. Consumer appliances are now becoming activated and “smart.” Think the idea of your appliances spying on you is crazy? Related July 14, 2011 In "Old-Thinker News Reports" October 19, 2014
NSA reportedly intercepting laptops purchased online to install spy malware According to a new report from Der Spiegel based on internal NSA documents, the signals intelligence agency's elite hacking unit (TAO) is able to conduct sophisticated wiretaps in ways that make Hollywood fantasy look more like reality. The report indicates that the NSA, in collaboration with the CIA and FBI, routinely and secretly intercepts shipping deliveries for laptops or other computer accessories in order to implant bugs before they reach their destinations. According to Der Spiegel, the NSA's TAO group is able to divert shipping deliveries to its own "secret workshops" in a method called interdiction, where agents load malware onto the electronics or install malicious hardware that can give US intelligence agencies remote access. This tool, among others, is available to NSA agents through what Der Spiegel describes as a mail-order spy catalog. Sometimes the NSA hops on an FBI jet for high-tech raids
Domestic Surveillance Techniques - Our Data Collection Program Surveillance Techniques: How Your Data Becomes Our Data In 2001, NSA published the secret "Transition 2001" report defining our strategy for the 21st century. No longer could we simply access analog communications using conventional means, the new digital world of globally-networked encrypted communications required a dramatic change to our surveillance strategy: NSA would need to "live on the network". We've turned our nation's Internet and telecommunications companies into collection partners by installing filters in their facilities, serving them with secret court orders, building back doors into their software and acquiring keys to break their encryption. Our Domestic Intercept Stations NSA technicians have installed intercept stations at key junction points, or switches, throughout the country. View a sample route that internet data traverses from a home in Toronto to the San Francisco Art Institute passing through several NSA intercept stations. Bulk Collection of U.S.
TheSoulfulEMU : .@3F_Bildideen @Heatherburns201...