


Worse than Zombies: The Mobile Botnets are Coming Hitman Pro "Hitman Pro" kombiniert mehrere Sicherheits-Engines unter einer Oberfläche, darunter bekannte Tools von Herstellern wie Dr. Web, Emsisoft und G Data. Die Software versucht diejenigen Viren, Malware, Trojaner oder Spyware-Komponenten aufzuspüren, die ihre installierten Schutzprogramme wie Antiviren-Software und Firewall nicht gefunden haben. Die parallele Nutzung verläuft konfliktfrei. "Hitman Pro" muss nicht installiert werden und kann nach dem Download einfach per Doppelklick gestartet werden, auf Wunsch auch direkt von einem USB-Stick oder von einer CD/DVD. Ab Version 3.7.x hat sich einiges getan. Fazit: Für alle, die ganz sicher gehen wollen und sich nicht auf ein einziges Sicherheits-Tool verlassen wollen.
Top 15 Security/Hacking Tools & Utilities 1. Nmap I think everyone has heard of this one, recently evolved into the 4.x series. Nmap (“Network Mapper”) is a free open source utility for network exploration or security auditing. It was designed to rapidly scan large networks, although it works fine against single hosts. Can be used by beginners (-sT) or by pros alike (–packet_trace). Get Nmap Here 2. Recently went closed source, but is still essentially free. Nessus is the world’s most popular vulnerability scanner used in over 75,000 organizations world-wide. Get Nessus Here 3. Yes, JTR 1.7 was recently released! John the Ripper is a fast password cracker, currently available for many flavors of Unix (11 are officially supported, not counting different architectures), DOS, Win32, BeOS, and OpenVMS. You can get JTR Here 4. Nikto is a good CGI scanner, there are some other tools that go well with Nikto (focus on http fingerprinting or Google hacking/info gathering etc, another article for just those). Get Nikto Here 5. 6. p0f 7. 8. 9.
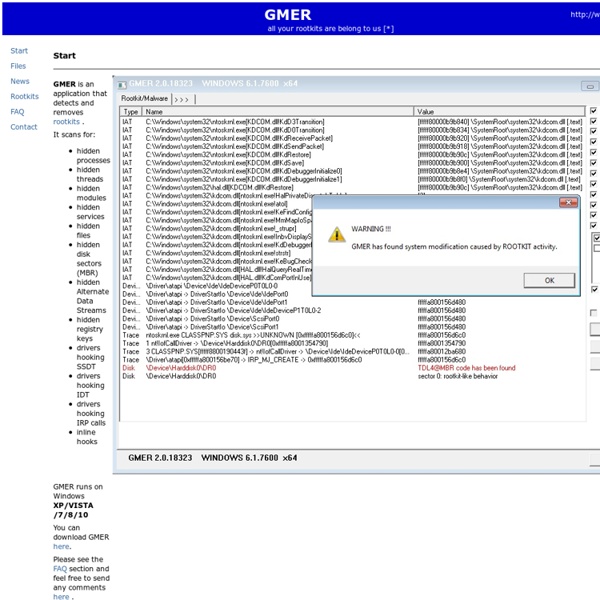
siszyd32.exe siszyd32.exe is usually located in the 'C:\Documents and Settings\Administrator\Start Menu\Programs\Startup\' folder. If you have additional information about the file, please share it with the FreeFixer users by posting a comment at the bottom of this page. Vendor and version information [?] siszyd32.exe does not have any version or vendor information. Digital signatures [?] siszyd32.exe is not signed. Folder name variants siszyd32.exe may also be located in other folders than C:\Documents and Settings\Administrator\Start Menu\Programs\Startup\. C:\Documents and Settings\??????? Hashes [?] Error Messages These are some of the error messages that can appear related to siszyd32.exe: siszyd32.exe has encountered a problem and needs to close. siszyd32.exe - Application Error. siszyd32.exe has stopped working. End Program - siszyd32.exe. siszyd32.exe is not a valid Win32 application. siszyd32.exe - Application Error. What will you do with siszyd32.exe? What did other users do? Malware or legitimate?
Digital footprint Digital footprint refers to the traces of data that are left behind by users on digital services. [1] There are two main classifications for digital footprints: passive and active. A passive digital footprint is created when data is collected about an action without any client activation, whereas active digital footprints are created when personal data is released deliberately by a user for the purpose of sharing information about oneself.[1] Passive digital footprints can be stored in many ways depending on the situation. In an online environment a footprint may be stored in an online data base as a hit. This footprint may track the user IP address, when it was created, and where they came from; with the footprint later being analyzed. Active digital footprints can be also be stored in many ways depending on the situation. Web browsing[edit] Social networking systems may record activities of individuals, with data becoming a life stream. Privacy issues[edit] See also[edit]
FreeFixer The Cuckoo's Egg (book) Summary[edit] Clifford Stoll (the author) managed some computers at Lawrence Berkeley National Laboratory in California. One day, in August 1986, his supervisor (Dave Cleveland) asked him to resolve a USD$0.75 accounting error in the computer usage accounts. Over the next ten months, Stoll spent a great deal of time and effort tracing the hacker's origin. Over the course of this investigation, Stoll contacted various agents at the FBI, CIA, NSA, and Air Force OSI. Studying his log book, Stoll saw that the hacker was familiar with VMS, as well as AT&T Unix. Stoll later had to fly to Germany to testify at the trial of Hess and a confederate. References in popular culture[edit] See also[edit] References[edit] External links[edit]
SpyBot - Search & Destroy Das Programm "SpyBot - Search & Destroy" durchsucht Ihre Windows-Installation auf Knopfdruck nach Spyware. Findet SpyBot verdächtige Software auf Ihrem PC, kann es die für die Werbung und das Spionieren zuständigen Teile entfernen, ohne die Funktion des eigentlichen Programmes zu beeinträchtigen. Immunisierungen und Quarantäne-Funktionen sorgen für zusätzliche Sicherheit. Ein weiteres Feature von SpyBot ist die Beseitigung von "Gebrauchsspuren", die es unerkannten Spionen schwerer macht, überhaupt Informationen zu finden. Entfernen lassen sich zum Beispiel die Listen der zuletzt besuchten Webseiten, geöffneten Dateien, gestarteten Programmen oder Cookies. Für Neueinsteiger gibt es einen Easy Mode, Profis können den Advanced Mode mit zusätzlichen Werkzeugen und Einstellungs-Möglichkeiten benutzen. In der neuen Version 2.2 wurde Spybot für Windows 8.1 vorbereitet. Im Downloadbereich des Herstellers finden Sie auch noch die ältere Version 1.6.2.
How To Become A Hacker Copyright © 2001 Eric S. Raymond As editor of the Jargon File and author of a few other well-known documents of similar nature, I often get email requests from enthusiastic network newbies asking (in effect) "how can I learn to be a wizardly hacker?". Back in 1996 I noticed that there didn't seem to be any other FAQs or web documents that addressed this vital question, so I started this one. If you are reading a snapshot of this document offline, the current version lives at Note: there is a list of Frequently Asked Questions at the end of this document. Numerous translations of this document are available: ArabicBelorussianBulgarianChinese, Czech. The five-dots-in-nine-squares diagram that decorates this document is called a glider. If you find this document valuable, please support me on Patreon or SubscribeStar. The hacker mind-set is not confined to this software-hacker culture. If you want to be a hacker, keep reading. 1. 2. 3. 5. 2. 3.
Set Up a Home Server Setting up a home server running an open-source operating system is a popular and useful activity. Useful in what ways, you may ask. You could use it to run a website (I use a home server to power my world travel website, luxagraf.net), collect and send e-mail messages, store your OpenID credentials or serve your music around the home. As you can guess, we have a great many tutorials on Webmonkey for getting the most out of that machine in your closet. But here are some guidelines for the hardware side of it. Introduction Before You Start – Alternatives Setting up a home server can be a lot of fun and a great learning experience. What you’ll need To build your own server, you need just a few components, some or all of which you may well have already: A computer A broadband network connection A network router, with Ethernet (CAT5) cable A monitor and keyboard (just for the first few steps) A CD/DVD drive/burner will be handy if you plan to use the server for media. The computer Memory
Why Python? My first look at Python was an accident, and I didn't much like what I saw at the time. It was early 1997, and Mark Lutz's book Programming Python from O'Reilly & Associates had recently come out. O'Reilly books occasionally land on my doorstep, selected from among the new releases by some mysterious benefactor inside the organization using a random process I've given up trying to understand. One of them was Programming Python. I had already heard just enough about Python to know that it is what is nowadays called a “scripting language”, an interpretive language with its own built-in memory management and good facilities for calling and cooperating with other programs. Perl, of course, is the 800-pound gorilla of modern scripting languages. At that time, I had used Perl for a number of small projects. I immediately tripped over the first odd feature of Python that everyone notices: the fact that whitespace (indentation) is actually significant in the language syntax. Listing 1 Listing 2