


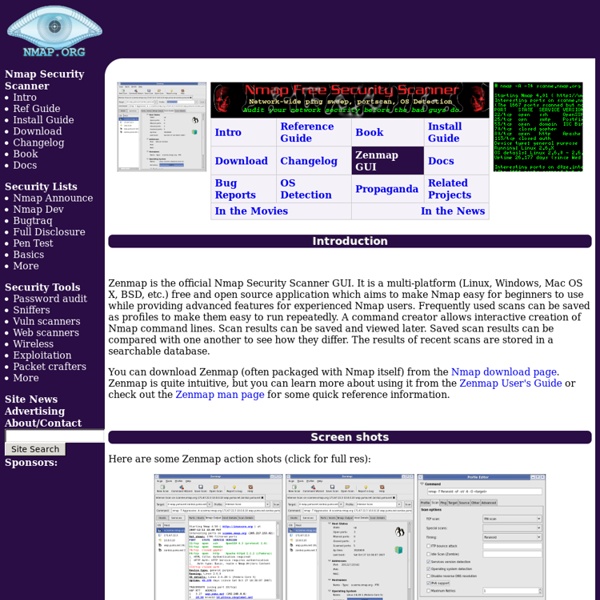
p0f v3 Copyright (C) 2012 by Michal Zalewski <lcamtuf@coredump.cx> Yeah, it's back! 1. What's this? P0f is a tool that utilizes an array of sophisticated, purely passive traffic fingerprinting mechanisms to identify the players behind any incidental TCP/IP communications (often as little as a single normal SYN) without interfering in any way. Some of p0f's capabilities include: Highly scalable and extremely fast identification of the operating system and software on both endpoints of a vanilla TCP connection - especially in settings where NMap probes are blocked, too slow, unreliable, or would simply set off alarms. Common uses for p0f include reconnaissance during penetration tests; routine network monitoring; detection of unauthorized network interconnects in corporate environments; providing signals for abuse-prevention tools; and miscellanous forensics. You can read more about its design and operation in this document. Fun fact: The idea for p0f dates back to June 10, 2000. 2. 3. 4. 5.
Working Links To The Deep Web Hidden Wikis Index pages in Wiki-based format. The Hidden Wiki - The original Hidden Wiki (after Matt's), owned by ion. Created January 2009. Other indexes Other places/directories you may be able to find links. OnionBookmark - Keep bookmarks private or share with public. Search engines Google for Tor. Grizzly Search Engine - New search engine. Other general stuff to see Starting places. Tor WebDesign Guidelines - Suggestions to start making your own Hidden Service. Marketplace See also: The separate Drugs and Erotica sections for those specific services. Reviews of the marketplace experience does not belong to the list below. Be wary when using any of these services, especially Commercial. Financial Services Currencies, banks, money markets, clearing houses, exchangers. Banker and Co. - Professional money laundering and consultation service. Commercial Services DiamondsandGold - Sells stolen diamonds and gold. Scams / Likely Scams Hosting Services Filesharing TorShare - 2GB file upload limit.
30 Specialist (and Super Smart) Search Engines Google is widely (and rightly) recognised as the mother of all search engines. But, if you need to drill down your searches by more specific details, do you trust Google to give you what you need every single time? Here’s a collection of 3o vertical search engines which you should have up your sleeve when you need some specialist power. Flights / Travel 1. SkyScanner.net – The leading flights search engine, providing information about all carriers to help you find the best deal. 2. 3. 4. 5. Images 7. 8. People 9. Forums 11. Music 12. Audio and Video 16. Resources 18. Domain names 20. Icons 22. Private search 25. Similar websites 26. All-rounders 27. While some of these are better alternatives to Google and the other major engines, for the most part, the big boys do it incredibly (incredibly, incredibly) well. olly via shutterstock
15 Best Free Open Source Ecommerce Platforms When it comes to open source ecommerce platforms, there are plenty to choose from. Here, we take a close look at the 15 best available, which should help guide you in the right direction. I’m not going to lie- finding the perfect platform is not easy. Each one has its own set of pros and cons and has been designed with a slightly different user in mind. Uploading products and customising your store can be very time consuming, so make sure you have given several platforms a try before you make that final decision and integrate one into your site. 1. You’ve only got to look at Magento’s client list to realise what an excellent piece of open-source software it is. 2. osCommerce (free) osCommerce is absolutely free under the GNU General Public License and caters very well to most people’s needs. 3. Not only does OpenCart look great, it’s extremely scalable. 4. Spree is an open-source ecommerce platform for Ruby on Rails. 5. 6. VirtueMart, which has been designed to work alongside Joomla! 7.
CloudSurfer (Web Browser) ★★★ Limited time sale. Only $1.99 30%OFF ★★★ CloudSurfer is a web browser supporting Firefox Sync, bidirectional Dropbox Sync, saving web page as eBook and many other features with a beautiful and clean design. No complex configuration and setting page. Simple, elegant and just works. ● Unique Features ● ★ POWERFUL GESTURE RECOGNIZERThe unique gesture recognition user interface gives you the closest experience and operation of the mouse gesture of all the popular PC browsers. ★ FIREFOX SYNCCloudSurfer brings all your bookmarks from your Firefox back to iPad. ★ SAVE AS EBOOKCloudSurfer is the only browser can save webpages as ebooks and view them in iBooks or other ebook readers. ★ TRUE BI-DIRECTIONAL DROPBOX SYNCUnlike other browsers just give you 1-way uploading to Dropbox. ★ AD-BLOCKBlock all the annoying advertisement by AdBlock+ Easylist. ★ DOWNLOAD ALL IMAGESCloudSurfer can download all the images and automatically save in a new folder. What's new Screenshots Share with Others Version:
Recommended Search Engines-The Library Google alone is not always sufficient, however. Not everything on the Web is fully searchable in Google. Overlap studies show that more than 80% of the pages in a major search engine's database exist only in that database. Table of features Some common techniques will work in any search engine. You may also wish to consult "What Makes a Search Engine Good?" How do Search Engines Work? Search engines do not really search the World Wide Web directly. Search engine databases are selected and built by computer robot programs called spiders. If a web page is never linked from any other page, search engine spiders cannot find it. After spiders find pages, they pass them on to another computer program for "indexing." Many web pages are excluded from most search engines by policy.
Understanding user-agent strings (Internet Explorer) Updated: July 2013 Here we discuss the user-agent string, which identifies your browser and provides certain system details to servers hosting the websites you visit. We'll also learn how to view your user-agent string, understand tokens used by recent versions of Windows Internet Explorer, and understand registry keys that affect the user-agent string. We'll cover these sections. Introduction When you visit a webpage, your browser sends the user-agent string to the server hosting the site that you are visiting. Because certain non-Microsoft sites add details to the user-agent string, it's important to understand the user-agent string. Understanding the user-agent string When you request a webpage, your browser sends a number of headers to the server hosting the site that you're visiting, as shown here. These headers occur during a negotiation process that helps the browser and the hosting server determine the best way to provide the requested information. Viewing the user-agent string
s | Password Haystacks: How Well Hidden is Your Needle? ... and how well hidden is YOUR needle? Every password you use can be thought of as a needle hiding in a haystack. After all searches of common passwords and dictionaries have failed, an attacker must resort to a “brute force” search – ultimately trying every possible combination of letters, numbers and then symbols until the combination you chose, is discovered. If every possible password is tried, sooner or later yours will be found. The question is: Will that be too soon . . . or enough later? This interactive brute force search space calculator allows you to experiment with password length and composition to develop an accurate and quantified sense for the safety of using passwords that can only be found through exhaustive search. <! (The Haystack Calculator has been viewed 8,794,660 times since its publication.) IMPORTANT!!! It is NOT a “Password Strength Meter.” Since it could be easily confused for one, it is very important for you to understand what it is, and what it isn't: Okay.
Scraping for Journalism: A Guide for Collecting Data Photo by Dan Nguyen/ProPublica Our Dollars for Docs news application lets readers search pharmaceutical company payments to doctors. We’ve written a series of how-to guides explaining how we collected the data. Most of the techniques are within the ability of the moderately experienced programmer. The most difficult-to-scrape site was actually a previous Adobe Flash incarnation of Eli Lilly’s disclosure site. These recipes may be most helpful to journalists who are trying to learn programming and already know the basics. If you are a complete novice and have no short-term plan to learn how to code, it may still be worth your time to find out about what it takes to gather data by scraping web sites -- so you know what you’re asking for if you end up hiring someone to do the technical work for you. The tools With the exception of Adobe Acrobat Pro, all of the tools we discuss in these guides are free and open-source. Ruby – The programming language we use the most at ProPublica.