


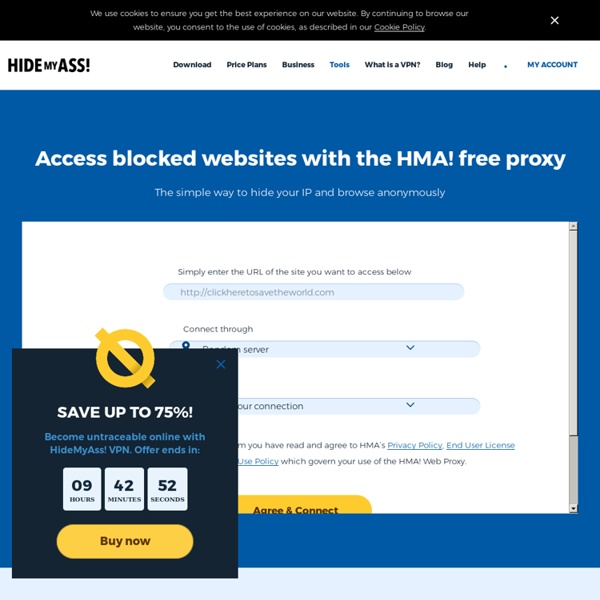
https://www.hidemyass.com/proxy
newbie_guide Idea and initial work: ASPj Additions by: a number of good souls Last updated: May 09, 2008 This tutorial will give you the basics to get started using the aircrack-ng suite. It is impossible to provide every piece of information you need and cover every scenario. So be prepared to do some homework and research on your own. The Forum and the Wiki have lots of supplementary tutorials and information.
How to Create a Master Installation Flash Drive with Multiple Versions of Windows You’ve got your collection of Windows ISOs and maybe you’ve burned installation DVDs or flash drives for them. But why not make yourself a master installation drive that you can use to install any version of Windows? Setting up a bootable USB Drive that includes multiple ISOs is actually pretty easy, We’re going to do it using a clever little free tool named WinSetupFromUSB, so go ahead and download the latest version of that. You can even include some non-windows ISOs on the disk, like Linux distributions and antivirus rescue disks.
Open Access Maps at NYPL The Lionel Pincus & Princess Firyal Map Division is very proud to announce the release of more than 20,000 cartographic works as high resolution downloads. We believe these maps have no known US copyright restrictions.* To the extent that some jurisdictions grant NYPL an additional copyright in the digital reproductions of these maps, NYPL is distributing these images under a Creative Commons CC0 1.0 Universal Public Domain Dedication. The maps can be viewed through the New York Public Library’s Digital Collections page, and downloaded (!) PrimoCache Overview PrimoCache is a software caching solution that cooperates with physical memory, solid-state drives (SSDs) and flash drives to provide data caching for local physical disks or iSCSI disks. It transparently stores disk data into fast cache devices such as physical memory, so that future read requests for those data will be served directly from the cache and be faster. Thus access time will be reduced, showing a great improvement in system reading performance. Furthermore, PrimoCache is able to complete write requests quickly by writing incoming data to fast cache devices first and writing back to target disks later, greatly improving the system writing performance. What Can You Do With It? PrimoCache In Detail
Join This Site - Goozers-chat This is a template project: we are making a template for open source project wikis. Right now this template is open to contributions from any registered Wikidot user. If you want to help with designing or fine-tuning, join the project as a member. Buyers Edge - Interest Free Shopping It's easy to provide your consent. Simply log in above to the Online Service Centre and look for the Credit Limit Invitations tab. It’s easy to provide your consent. Destiny 2: Override Frequency guide - Sleeper Node locations and Nascent Dawn About Ed Thorn Ed joined Metabomb in May 2017 and puts together guides and news across the site. Our Destiny 2 Override Frequency guide contains everything you need to know about how to unlock Override Frequencies, Nascent Dawn, find all Sleeper Nodes and their rewards. You've probably noticed these strange floating objects while out and about shooting the Hive and Cabal on the surface of Mars in Destiny 2's latest expansion Warmind. Try and crack them open without fulfilling the necessary requirements and they'll tell you to find the correct Override Frequency - but what does this actually mean?
Pimp my uTorrent : An angular.js application that removes the ads in uTorrent with a single click You've come to the right place, I'm about to pimp your µTorrent! All you have to do is make sure that µTorrent is running, click the 'Pimp My µTorrent' button below, grant the permission in µTorrent (a dialog will pop up) sit back and relax! Make sure you are running a recent version above 3.2.1!
What does UTP, S/UTP, FTP, STP and SFTP mean? Copper Ethernet Cables The table below shows the different types of copper Ethernet cable and gives a brief description of each type. Electromagnetic shielding/screening can be made from a metallic or polyester foil, or metallic braid, either around individual conductor pairs, all 4 pairs, or both. Cat5e, Cat6 and Cat6a are available in unshielded and shielded formats, Cat7 is only available as a shielded cable. The 7 Best Internet Speed Tests to Keep Your ISP Honest Internet service providers like to make a lot of claims about upload and download speeds when you sign up, but do you ever wonder how those numbers compare to the speeds you’re actually getting on a day-to-day basis? These are the best internet speed tests to help you determine your upload and download speeds, as well as identify other issues with your network, such as packet loss, latency issues, or physical connection problems. Note that some of these sites may not work with an ad blocker enabled. You can either add the site to your whitelist, or look for an option that doesn’t mind an ad blocker. The best
[ROOT] Framaroot, a one-click apk to root some devices Hi, Here an one-click application to install Superuser and su binary on phone. Look at the compatibility list here to see if this application can be useful for you. Search the collection Business as usual reference and digitisation services have resumed for WA. There may be a slight delay in responding to your request as we work through the backlog of applications received while access to the collection was closed. Thank you for your patience and support.
List of Nvidia graphics processing units This page contains general information about graphics processing units (GPUs) and video cards from Nvidia, based on official specifications. In addition some Nvidia motherboards come with integrated onboard GPUs. Limited/Special/Collectors' Editions or AIB versions not included. Field explanations[edit] Who Owns Which Car Brands? Here’s a list the major car corporations that sell in the U.S. and the brands they currently offer here. Parent Company owns Brand BMW Group owns BMW, Mini, and Rolls-Royce.Daimler AG owns Mercedes-Benz and Smart.Fiat Chrysler Automobiles owns Alfa Romeo, Chrysler, Dodge, Fiat, Jeep, Maserati, and Ram.Ford Motor Co. owns Ford and Lincoln.General Motors owns Buick, Cadillac, Chevrolet, and GMC.Honda Motor Co. owns Acura and Honda.Hyundai Motor Group owns Genesis, Hyundai, and Kia.Mazda Motor Corp. owns Mazda.Renault-Nissan-Mitsubishi Alliance owns Infiniti, Mitsubishi, and Nissan.Subaru Corp. owns Subaru.Tata Motors owns Jaguar and Land Rover.Tesla owns Tesla.Toyota Motor Corp. owns Lexus and Toyota.Volkswagen Group owns Audi, Bentley, Bugatti, Lamborghini, Porsche, and Volkswagen.Zhejiang Geely Holding Group (ZGH) owns Lotus, Polestar, and Volvo.