

NULL Life. The Hacker Games « Thoughts on Security. Welcome, welcome!
The time has come to select one courageous young hacker for the honor of representing District 12 in the 74th annual Hacker Games! And congratulations, for you have been selected as tribute! Hacking games and CTF’s are a lot of fun; who doesn’t like pitting your skills against the gamemakers and having a free pass to break into things? But watch out, as you will find out, some games are more dangerous than others. I have talked about counterattacks here before, and this system has implemented a number of aggressive anti-hacker measures. In fact, this VM is downright evil. To save precious bandwidth, this has been implemented in a minimal tinycore-based VM, and will require VirtualBox to run.
Unfortunately, I didn’t have the time to add nearly all the things I wanted to, so there are really just a few challenges, a couple of counterhacks, and about 10 memes to conquer. No sponsors are necessary, so don’t light yourself on fire. Introducing CryptOMG. Index of / Hacking Conference - Capture the Flag Archive. This page is devoted to collecting accounts, walk throughs and other resources of Capture the Flag at DEF CON over the years, not only for history's sake but so the uninformed can better grasp the epic journey that teams must face on the road to CTF victory!

If you know of a resource that should be included on this page, feel free to pass it along to neil ]at[ defcon [dot] org. DEF CON 21 Capture the Flag Pcaps, Binaries and Tools Binaries and Tools: Torrent Friday Packet Captures: Torrent Saturday Packet Captures: Coming Soon! DEF CON 21 Capture the Flag Write-ups CNBC Article - Cyberteams duke it out in the World Series of LegitBS Blog - Final Writeup: LegitBS Blog - Public Handout: Positive Hack Days. CTF. Gameplay Analysis.

CTF Quals, registration has started! Hackers from All Over the World Competed to Join PHDays IV CTF PHDays CTF Quals, an information security competition, took place from 12 p.m. on January 25 to 12 p.m. on January 27, with teams competing for the entire 48 hours. Dragon Sector, a Polish team, won the contest, though quite unexpectedly, PPP, from the USA, took second place and More Smoked Leet Chicken, from Russia, came in third. Contests. Infosec stuff: CAPTURE THE FLAG CHALLENGE. HackIM 2012 - Delhi. New NoVA CTF Challenge. The folks over at NoVA CTF recently released a new contest to the NoVA Hackers list.
They again gave me permission to republish the challenge here for the rest of the community to enjoy. If everything goes well … expect two more follows-ons to this challenge in the near future. You might also want to check out some of their previous challenges here and here. Well on to the details of this contest… “Reverse Engineering CTF – Part 1″ Analyze the following file to find “something.” (or at least I am told from the creator of the CTF… obviously rename this too easteregg.exe) easteregg.
Good luck everyone! CaptureTheFlag – Hack.LU2012. CSAW CTF 2012. Drunk Admin Web Hacking Challenge. Recently I conducted a few keynote talks on the WeBaCoo tool and some web backdoor shell implementation techniques.
As a great supporter of practical learning, I designed a relative web hacking challenge that was given to the events attendees after the end of the talk part. The challenge focuses on techniques and methodologies discussed during the talks and implements a slightly restricted web server setup serving a vulnerable image hosting service. Download The challenge was served on a Debian vmware image which is available for download on the following link: Download Challenge (539MB) – md5sum:edf9bcd28049ed85312510d5872ea463Download mirror from boot2root Configuration The network is configured to obtain an IP address via DHCP by default. Mission The challenge includes an image hosting web service that has various design vulnerabilities. FINAL GOAL: Reveal the hidden message for a date arrange that Bob sent to Alice. Work Flow Appendix A. Blog: </CaptureTheFlag> The last flag has been captured, and the final tallies are in.
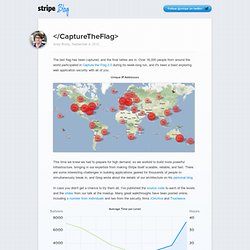
Over 16,000 people from around the world participated in Capture the Flag 2.0 during its week-long run, and it's been a blast exploring web application security with all of you. Unique IP Addresses This time we knew we had to prepare for high demand, so we worked to build more powerful infrastructure, bringing in our expertise from making Stripe itself scalable, reliable, and fast. There are some interesting challenges in building applications geared for thousands of people to simultaneously break in, and Greg wrote about the details of our architecture on his personal blog.
Stripe: Capture the Flag. Captf - Practice ctf list. Here's a list of some CTF practice sites and tools or CTFs that are long-running.

Thanks, RSnake for starting the original that this is based on. If you have any corrections or suggestions, feel free to email ctf at the domain psifertex with a dot com tld. Live Online Games Recommended Whether they're being updated, contain high quality challenges, or just have a lot of depth, these are probably where you want to spend the most time. Others Meta (excellent list of challenge sites) (good CTF wiki, though focused on CCDC) (great archive of CTFs) Webapp Specific Forensics Specific Recruiting Paid Training Downloadable Offline Games Virtual Machines Inactive or Gone. Captf Calendar.