

Server (computing) Computer to access a central resource or service on a network First WWW server located at CERN with its original sticker that says: "This machine is a server.
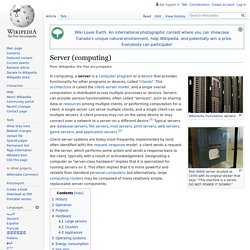
DO NOT POWER IT DOWN!! " Client–server systems are today most frequently implemented by (and often identified with) the request–response model: a client sends a request to the server, which performs some action and sends a response back to the client, typically with a result or acknowledgement. Designating a computer as "server-class hardware" implies that it is specialized for running servers on it. This often implies that it is more powerful and reliable than standard personal computers, but alternatively, large computing clusters may be composed of many relatively simple, replaceable server components. The Jargon File defines "server" in the common sense of a process performing service for requests, usually remote, with the 1981 (1.1.0) version reading: These types of servers are often housed in dedicated data centers.
Step-by-Step Guide for Setting Up VPN-based Remote Access in a Test Lab. This guide provides detailed information about how you can use five computers to create a test lab with which to configure and test virtual private network (VPN) remote access with the Microsoft® Windows® XP Professional operating system with Service Pack 2 (SP2) and the 32-bit versions of the Microsoft Windows Server™ 2003 operating system with Service Pack 1 (SP1).
These instructions are designed to take you step-by-step through the configuration required for a Point-to-Point Tunneling Protocol (PPTP) connection, a Layer Two Tunneling Protocol (L2TP) with Internet Protocol security (L2TP/IPsec) connection, and a VPN connection that uses certificate-based Extensible Authentication Protocol-Transport Level Security (EAP-TLS) authentication. Setting Up the Test Lab for PPTP, L2TP/IPsec, and EAP-TLS Remote Access VPN Connections The infrastructure for the VPN test lab network consists of five computers performing the following services: IIS1 obtains its IP address configuration using DHCP. Eigrp.jpg (JPEG Image, 925 × 637 pixels)
Redistribution OSPF - EIGRP - config-free. Determining Your Networking Requirements > Introduction to Cisco Network Design. Designing a network can be a challenging task.

Your first step is to understand your networking requirements. The rest of this chapter explains how to determine these requirements. After you have identified these requirements, refer to Chapter 2 for information on selecting network capability and reliability options that meet these requirements. Networking devices must reflect the goals, characteristics, and policies of the organizations in which they operate. Two primary goals drive networking design and implementation: Application availability—Networks carry application information between computers. A well-designed network can help balance these objectives. The Design Problem: Optimizing Availability and Cost In general, the network design problem consists of the following three general elements: The goal is to minimize cost based on these elements while delivering service that does not compromise established availability requirements.
Understanding Network Requirements and Configuration. This chapter describes the network requirements for the Exalogic machine.

It contains the following topics: 6.1 Overview of Network Requirements An Exalogic machine includes compute nodes, storage appliance, as well as equipment to connect the compute nodes to your network. The network connections allow the servers to be administered remotely, enable clients to connect to the compute nodes, and enable client access to the storage appliance. Each compute node consists of the following network components and interfaces: 4 embedded Gigabit Ethernet ports (On Oracle Linux: NET0, NET1, NET2, and NET3, on Oracle Solaris: igb0, igb1, igb2, igb3)Note: Only NET0 or igb0 is connected and used.1 dual-port QDR InfiniBand Host Channel Adapter (ib0 and ib1 for Oracle Linux, and ibp0 and ibp1 for Oracle Solaris)1 Ethernet port for Sun Integrated Lights Out Manager remote management (ILOM)Note: This port is not connected or used. Note: 6.2 Naming Conventions 6.3 Important Notes for Oracle Solaris Users.
Five Best Virtual Machine Applications. Oracle VM VirtualBox. VMware Virtualization for Desktop & Server, Application, Public & Hybrid Clouds. New Internet Routing Method Allows Users to Avoid Sending Data Through Undesired Geographic Regions. Censorship is one of the greatest threats to open communication on the Internet.
Information may be censored by a user’s country of residence or the information’s desired destination. But recent studies show that censorship by countries through which the data travels along its route is also a danger. Now, computer scientists at the University of Maryland have developed a method for providing concrete proof to Internet users that their information did not cross through certain geographic areas. The new system offers advantages over existing systems: it is immediately deployable and does not require knowledge of—or modifications to—the Internet’s routing hardware or policies.
This new system, called Alibi Routing, will be presented on August 20, 2015, at the Association for Computing Machinery Special Interest Group on Data Communication (ACM SIGCOMM) conference in London. Some parts of the world have been known to modify data returned to users, thus censoring content. Step-by-Step Guide for Setting Up VPN-based Remote Access in a Test Lab.