

Manner of collection of personal information (principle four) Personal information shall not be collected by an agency - (a) by unlawful means; or(b) by means that, in the circumstances of the case - (i) are unfair; or(ii) intrude to an unreasonable extent upon the personal affairs of the individual concerned.

When an agency collects information about a person, it has to do it in a way that's fair and legal. Principle 4 governs how information is collected (as distinct from what information is being collected, or why). It stops agencies from collecting information in a way that is: unlawful;unfair; orunreasonably intrusive. When is a method of collection 'unlawful'? Some means of collecting information are specifically prohibited. Collection might also be unlawful if the conduct of the person or agency collecting the information breaks a law. Where an agency has relied on an unlawful action to help it collect information, that collection is a likely breach of principle 4. See Case note 5421 - unlawful Case note 3734 - unlawful See guidance for CCTV.
Our methods. Intelligence Cycle The process the New Zealand Security Intelligence Service follows in conducting investigations, collecting intelligence, assessing it and reporting to the Government can be illustrated in what is known as the "security intelligence cycle".
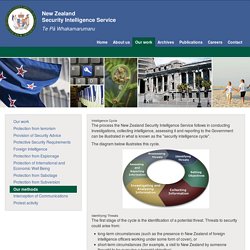
The diagram below illustrates this cycle. Identifying Threats. The Role of Intelligence. With the end of the Cold War and the reduced need to focus on the former Soviet Union, many observers believed that the Intelligence Community was looking for new missions to justify its existence.

The Commission found, to the contrary, that the core missions of U.S. intelligence have remained relatively constant. There has been a substantial shift in intelligence requirements and priorities away from Cold War targets, but the missions intelligence agencies are expected to perform have not changed dramatically with the end of the Cold War. UK gathering secret intelligence via covert NSA operation. The UK's electronic eavesdropping and security agency, GCHQ, has been secretly gathering intelligence from the world's biggest internet companies through a covertly run operation set up by America's top spy agency, documents obtained by the Guardian reveal.
The documents show that GCHQ, based in Cheltenham, has had access to the system since at least June 2010, and generated 197 intelligence reports from it last year. The US-run programme, called Prism, would appear to allow GCHQ to circumvent the formal legal process required to seek personal material such as emails, photos and videos from an internet company based outside the UK. The use of Prism raises ethical and legal issues about such direct access to potentially millions of internet users, as well as questions about which British ministers knew of the programme. Coexistence and Covert Collection. An intelligence officer surveys his new opportunities and problems in a coexisting world.
George Romano The collection of intelligence information is greatly influenced in its purposes and methods by the state of international affairs; changes in the world situation can create or improve certain opportunities for collection and diminish or even deny others, while shifts in world opinion may seriously affect the advisability of undertaking particular types of intelligence activities. Intelligence Collection Disciplines. Intelligence Collection and Covert Action: Time for a Divorce? A retired CIA station chief examines they marriage between human intelligence collection and covert action that came about in the early years of the Cold War and its detrimental effects on the Agency’s ability to produce useful and timely intelligence on U.S. enemies.

If we cannot eliminate covert action entirely, he concludes, it should at least be separated from the intelligence collection function. – Ed. America has lived with its “Intelligence Community” – the CIA, NSA, DIA and all the other lesser intelligence organizations – for decades. Depending on your viewpoint, they have been somewhere between successful and unsuccessful in providing our government both with the organizational structure and with the intelligence needed to protect our country and advance its international interests.
Whatever your take, there is one immutable involved in intelligence work: It is an aggressive, risk-taking business that withers when bureaucratic inertia and caution settle in. Major issues in data mining. Every project should be undertaken with all the necessary preparations.
Data mining is no different. This tip from... By submitting your email address, you agree to receive emails regarding relevant topic offers from TechTarget and its partners. You can withdraw your consent at any time. Contact TechTarget at 275 Grove Street, Newton, MA. Data Mining. Data Mining: What is Data Mining? Overview Generally, data mining (sometimes called data or knowledge discovery) is the process of analyzing data from different perspectives and summarizing it into useful information - information that can be used to increase revenue, cuts costs, or both.

Data mining software is one of a number of analytical tools for analyzing data. It allows users to analyze data from many different dimensions or angles, categorize it, and summarize the relationships identified. Technically, data mining is the process of finding correlations or patterns among dozens of fields in large relational databases. Continuous Innovation Although data mining is a relatively new term, the technology is not. Example For example, one Midwest grocery chain used the data mining capacity of Oracle software to analyze local buying patterns. Data, Information, and Knowledge Data Data are any facts, numbers, or text that can be processed by a computer.