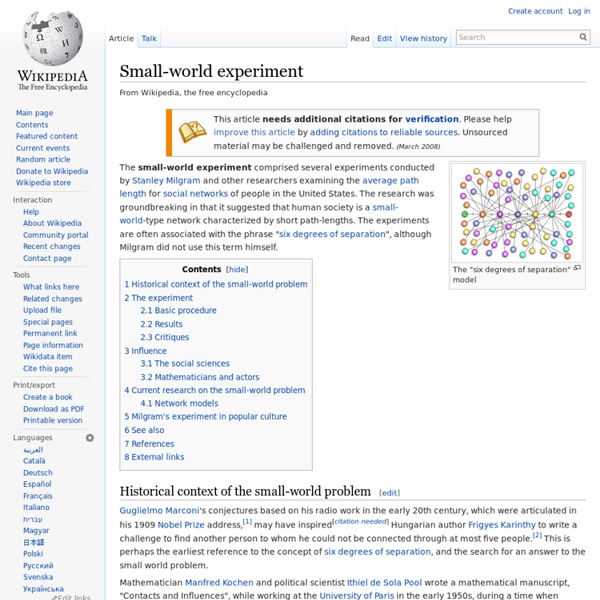
Math algorithm tracks crime, rumours, epidemics to source
(Phys.org) -- A team of EPFL scientists has developed an algorithm that can identify the source of an epidemic or information circulating within a network, a method that could also be used to help with criminal investigations. Investigators are well aware of how difficult it is to trace an unlawful act to its source. The job was arguably easier with old, Mafia-style criminal organizations, as their hierarchical structures more or less resembled predictable family trees. In the Internet age, however, the networks used by organized criminals have changed. "Using our method, we can find the source of all kinds of things circulating in a network just by 'listening' to a limited number of members of that network," explains Pinto. Out in the real world, the algorithm can be employed to find the primary source of an infectious disease, such as cholera. The validity of this method thus has been proven a posteriori. Explore further: Pseudo-mathematics and financial charlatanism
Cours de cartes conceptuelles
Une carte conceptuelle (ou schéma conceptuel, concept map en anglais), dont les variantes sont la mind map, carte des idées ou carte heuristique, est un diagramme qui représente les liens entre différents concepts. Elle peut être également appelée schéma de pensée, carte mentale, arbre à idées ou topogramme. La différence entre une carte heuristique et une carte conceptuelle est que cette dernière relie un ensemble de concepts entre eux par des lignes orientées et qualifiées (est un composant de.., favorise). De plus, elle prend la forme d' un graphe alors que la carte heuristique est un arbre. Ces cours en diapositives animées, vidéo, ppt, pdf et ces cartes conceptuelles sont distribués sous licence Creative Commons : à condition de me citer et de mettre un lien vers cette page, vous pouvez les réutiliser ou les modifier dans un cadre non-commercial, mais vous devez ensuite les publier aux mêmes conditions. - Cours de mind mapping en vidéo - En pdf et pptx En analyse fonctionnelle :
Crisis Mapping and Disaster Risk Reduction
By Vincent Fung GENEVA, 16 December 2011 - Crisis mapping has emerged in the last five years as a dynamic and open way to visualize and report on crisis and disasters. With increasing internet connectivity, mobile phone use, and user-generated content, 'crowdsourcing' is gaining traction by taking advantage of information communication technology (ICT) that allows communities and networks to answer some of the world’s most pressing issues. Held for the first-time ever in Europe, the 3rd International Conference on Crisis Mapping (ICCM) was one example of how new technologies and growing networks of tech-savvy individuals and organizations can help to prevent, prepare for and respond to disasters. “ICT tools, such as those used by Crisis Mappers, help us understand what is happening on the ground and who’s affected following a disaster. “The key to this insight is data – we have to continually collect, manage and update our organizational data to feed our analysis. Watch the video
The DIMES project | Join the journey to map the Internet, download the DIMES agent today
Installation d'un réseau : les étapes à respecter
1. Conseil de déploiement et audit du réseau Avant de démarrer une installation ou une modernisation du réseau informatique, l'entreprise doit évaluer ses besoins et connaître le périmètre fonctionnel de son réseau. Un prestataire rédige alors un cahier des charges précis. la nature et la superficie des locaux à équiper,les contraintes techniques de ces locaux,le nombre de serveurs requis,le nombre de personnes et de postes de travail à relier,les besoins en bande passante et en débit. 2. Cette étape vise à équiper les locaux de l'entreprise d'un réseau de câbles pour relier les serveurs et les PC entre eux. si le bâtiment est ancien, il sera difficile de percer les murs. 3. Il convient de vérifier la connectique des serveurs. 4. Les commutateurs réseaux sont des équipements électroniques intelligents qui permettent de connecter les différents serveurs et les postes de travail. 5. Cette étape plutôt classique vise à paramétrer les serveurs Windows et/ou Linux. 6. 7.
Researchers developing a social media lie detector
An international group of researchers led by the University of Sheffield are trying to find a way to verify information spreading on social networks in real-time, in order to provide a reliable and valuable resource for journalists, governments, emergency services and health agencies. In Greek mythology, Pheme would tell tales first with a whisper but then gradually getting louder until word had spread to everyone. This is precisely how rumour and misinformation can spread on social media and is the same name given to an EU-funded project researching how to sort the truth from the lies. Researchers from seven different countries are taking a multidisciplinary approach to the problem, combining big data analytics with natural language processing and text mining, web science, social network analysis, and information visualisation. How Pheme works Resources testing the veracity of user-generated content already exist. Stopping the spread of bad information A service like this has many uses.
Data Visualization Software | Tulip
Apprenez le fonctionnement des réseaux TCP/IP
Internet est devenu un élément incontournable de la vie quotidienne pour beaucoup de gens, et indispensable pour les informaticiens. Cependant, peu de monde connait en détail le fonctionnement d'Internet ! Aujourd'hui, il est devenu courant d'utiliser Internet à son travail. Mais savez-vous réellement ce qu'il se passe lorsque vous vous connectez à Internet ? De la même façon, presque tous les foyers sont équipés d'une multitude d'appareils informatiques : le boîtier ADSL, l'ordinateur de bureau, l'ordinateur portable, l'imprimante etc. Mais peu de gens savent vraiment faire communiquer entre-elles toutes ces machines ! Nous allons voir à travers ce cours comment créer ce qu'on appelle un réseau, pourquoi et comment les informations circulent sur Internet, et comment gérer sa connexion (et écouter celle des autres ! Comment les ordinateurs parlent-ils entre-eux ? Vous serez aussi en mesure de créer votre propre réseau local chez vous, et de l'administrer proprement. Vous êtes motivés ?