

Top 100 Network Security Tools. 80+ Best Free Hacking Tutorials. Learning to become hacker is not as easy as learning to become a software developer. Free Online IDE and Terminal. Secure Shell: How Does SSH Work. Taking remote shell, for carrying out different tasks is a norm, if you have multiple server machine's in your infrastructure.

Different protocols and tools were made to accomplish this task of taking a remote shell. Although the tools made during the initial days were capable enough to carry out necessary shell related tasks, there were different design concerns, that resulted in advancements and new tools to accomplish this task. In this tutorial guide, we will be discussing one such tool, that was designed to eliminate the flaws in previous remote shell programs. Our topic of interest for this tutorial is none other than the Secure Sell, better known as SSH.
The key characteristics that makes a remote login program an efficient one is pointed out in the below list. DCOM Error: 10009 - Windows Events. DCOM was unable to communicate with the computer swbend531 using any of the configured protocols.
Jun 12, 2009 DCOM was unable to communicate with the computer tracy using any of the configured protocols. Jun 21, 2009 DCOM was unable to communicate with the computer 216.34.131.135 using any of the configured protocols. The Internet map. 30 must know. Wireless Tools « Wireless Training Solutions. OSI model (Networking Layers) IPS (Internet Protocol Suite) Built-in functions and Stored Procedures. Overview The HSQLdb database engine included with Base supports the following functions and stored procedures for use within queries.
The Query component in Base allows for SQL commands that return a result set, i.e. SELECT and CALL. The component supports two views: GUI Query Designer (Designer View) Text editor (SQL View) Queries created and executed in Designer and SQL View support the use of named replaceable parameters in these statements, in most cases. Cisco ASA 5505 Quick Start Guide. 1.
Verifying the Package Contents 2. Installing the Chassis 3. Powering on and Verifying Interface Connectivity Interface Connectivity. How to find inactive users in Active Directory. Introduction Don’t we tend to inflict nightmares on ourselves?
When the small company I was with decided to go public, SOX audit reared its ugly head. And the internal SOX auditors were very quick to jump on those self-inflicted wounds. Allow me to explain. Advanced Threat Protection (ATP) Reviews. Import / Export SSL Certificates in Exchange Server 2016. If you have multiple Exchange servers it is imperative that each server have a valid 3rd-party certificate reflecting the namespace.
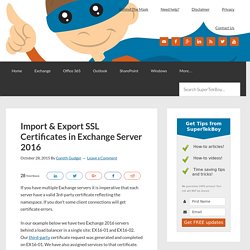
If you don’t some client connections will get certificate errors. Connect to Office 365 Compliance Center with PowerShell. Office 365: Delivery Has Failed to These Recipients or Groups. Exchange 2016 RTM was released on 1st October 2015.

Although I haven’t deployed this at the production level yet but my initial experience with Exchange 2016 is positive comparatively with previously versions of Exchange. Traditionally we had to wait for at least service pack 1 to be out before we even think about deploying Exchange at the production level and this is purely due to our real world experiences and how buggy Exchange has been. This perception is about to change as Exchange 2016 RTM is exactly the same Exchange as Exchange online - part of the office 365 already in production. I am optimistic that it is going to be less problematic and will help customers and organisations with early adoptions.The purpose of this blog is not to praise Exchange 2016 but rather to take a look at the features and under the hood architecture changes Exchange 2016 RTM has and how it differs from Exchange 2013. Exchange 200/2003 Exchange 2007/2010 Exchange 2013.
PowerShell for Microsoft Exchange Server. PowerShell Scripts for your Exchange Server Toolkit. Exam 70-410 Objective 1.2 – Configure Servers - Enterprise Daddy. Welcome back, this post covers Exam 70-410 Objective 1.2 – Configure Servers.
In the previous post, Exam 70-410 Objective 1.1 – Install Servers, we dealt with installing the Windows Server 2012 R2 and the various options that are available to us along with the planning and various other concepts. Once the server is ready after installing the operating system, typically it is not yet ready to perform the tasks that you intend it to do. Hence in this objective, we will deal with the various configurations that are required after installing the OS.
This objective covers how to: Configure NIC Teaming NIC Teaming is a feature of Windows Server 2012 R2 that enables administrators to combine the bandwidth of multiple network interfaces, providing increased performance and fault tolerance. Ensure LAN has priority over Wi-Fi. ETW Framework Tutorial. This tutorial provides conceptual overviews of the underlying Event Tracing for Windows (ETW) framework upon which message/event capturing is based in Message Analyzer.
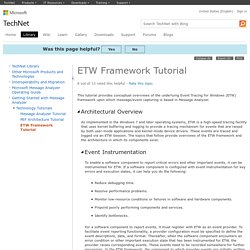
As implemented in the Windows 7 and later operating systems, ETW is a high-speed tracing facility that uses kernel buffering and logging to provide a tracing mechanism for events that are raised by both user-mode applications and kernel-mode device drivers. These events are traced and logged via an ETW Session. The topics that follow provide overviews of the ETW framework and the architecture in which its components exist. Network Monitor Open Source Parsers - Home. 16 Little-Known Google Calendar Features That'll Make You More Productive. Some things you think will be simple actually end up getting really complex.
Smtp. Definition of information management terms. There is considerable confusion in the marketplace regarding the definition of various information management terms. The scope and role of specific information systems is particularly blurry, in part caused by the lack of consensus between vendors. With the aim of lessening this confusion, this briefing provides an at-a-glance definition of terms for a range of information systems. Content management system (CMS) Content management systems support the creation, management, distribution, publishing, and discovery of corporate information. Also known as ‘web content management’ (WCM), these systems typically focus on online content targeted at either a corporate website or intranet. Enterprise content management system (ECMS) An enterprise content management system consists of a core web content management system, with additional capabilities to manage a broader range of organisational information.
Thinking Strategies. Goal Setting. Clarifying Priorities. How To Focus Your Attention. Problem Analysis & Problem Solving. Design Thinking. Acting Decisively; Making Good Decisions. What is ITIL? CompTIA Security+ Information Study Pack Concise Courses 2014. Security certification, CompTIA Security+ certification. Why Security+? Approved by U.S. Dept. of Defense to meet IA technical and management certification requirements Chosen by professional staff at Hitachi Information Systems (Japan), Prestariang Systems Sdn. Bhd. (Malaysia) and U.S. government contractors such as CSC, General Dynamics and Northrop Grumman Updated every 3 years and part of the CompTIA Continuing Education program Relevant Job Titles Security Engineer Security Consultant Network Administrator IA Technician or Manager Plan Your Career Path Certification Information The Security+ exam covers the most important foundational principles for securing a network and managing risk.
Wireshark Display Filters. How to Use Wireshark to Capture, Filter and Inspect Packets. Wireshark, a network analysis tool formerly known as Ethereal, captures packets in real time and display them in human-readable format. Wireshark includes filters, color-coding and other features that let you dig deep into network traffic and inspect individual packets. This tutorial will get you up to speed with the basics of capturing packets, filtering them, and inspecting them. You can use Wireshark to inspect a suspicious program’s network traffic, analyze the traffic flow on your network, or troubleshoot network problems.
Getting Wireshark You can download Wireshark for Windows or Mac OS X from its official website. Just a quick warning: Many organizations don’t allow Wireshark and similar tools on their networks. Network LAN TS2. Telnet commands. FREE CCNA Subnetting Tutorial: Practice IP Subnetting with examples. CCNA [Home] >> Learning Center>> Interactive Tutorials A short IP subnetting tutorial. Subnetting is explained with examples. Post assessment exercises after the course gives you hands on practice.By the end of this subnetting course, you should be able to: Define subnet and subnet masks Understand IP subnetting maths Calculate Network addressDefine private addressSubnet an IP network in a given scenario To start the subnetting tutorial, click the start button in the flash demo below!
Protocol Registries. Security+ List of Run Commands in Windows 7 and 8. Speed Up Windows 7 – Master Tutorial to Make Windows 7 Super Fast. This is the 3rd tutorial of our "Master Tutorial" series. We have already posted 2 other tutorials for Windows XP and Windows Vista in past and now its turn of Windows 7. Slow-Link with Windows 7 and DFS Namespaces - Ask the Directory Services Team. Fixing Problem With Windows 7 Shared Files and Mapped Drives Unavailable Over VPN. Step by Step Online IT Training.