

The coldest computers in the world. Image copyright Jack Hao Yang.
Can computers ever replace the classroom? For a child prodigy, learning didn’t always come easily to Derek Haoyang Li.

When he was three, his father – a famous educator and author – became so frustrated with his progress in Chinese that he vowed never to teach him again. “He kicked me from here to here,” Li told me, moving his arms wide. Yet when Li began school, aged five, things began to click. Differential Privacy. K-Anonymität. Weiblich, männlich, menschlich, künstlich: Wie klingt die Stimme Ihrer Brands? Google tweaked algorithm after rise in US shootings. Misinformation is so common after mass shootings that Google has had to tweak its algorithm to compensate, a senior search engineer at the company has revealed.
Pandu Nayak, who joined the company 14 years ago to work on its search engine, told the Guardian that mass murders presented an increasing challenge for the search engine to deliver accurate results. “In these last few years, there’s been a tragic increase in shootings,” Nayak said. “And it turns out that during these shootings, in the fog of events that are unfolding, a lot of misinformation can arise in various ways.
Will Artificial Intelligence Enhance or Hack Humanity? Hackers kill cars. YouTube algorithm adds 9/11 explainer to Notre Dame fire video. As thousands of Parisians lined the streets watching the historic Notre Dame cathedral burn on Monday evening, others around the world turned to YouTube for updates and were provided with false context about 9/11.
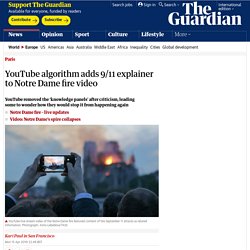
YouTube users watching the live stream of the burning building in the United States and South Korea were greeted with “knowledge panels”, a banner with a synopsis of related information, pushing Encyclopedia Britannica articles about the September 11 attacks. The platform introduced the knowledge panel feature in 2018 to cut down on misinformation, but in this case the tool created false associations between fire reportedly caused by accident and the 2001 US-based terrorist attack. The platform’s automated tools may have mistaken the visuals of the burning building for 9/11 footage, according to Vagelis Papalexakis, an assistant professor of computer science and engineering at the University of California, Riverside who studies machine learning used in similar systems.
How Android Fought an Epic Botnet—and Won( China’s hi-tech war on its Muslim minority. In mid-2017, Alim, a Uighur man in his 20s, returned to China from studying abroad.
As soon as he landed back in the country, he was pulled off the plane by police officers. He was told his trip abroad meant that he was now under suspicion of being “unsafe”. The police administered what they call a “health check”, which involved collecting several types of biometric data, including DNA, blood type, fingerprints, voice recordings and face scans – a process that all adults in the Uighur autonomous region of Xinjiang, in north-west China, are expected to undergo. Gaze Data wired. How Amazon's Algorithms Curated a Dystopian Bookstore. Your Apples May Soon Be Picked By Laser-Shooting Robots. Robot ‘Natural Selection’ Recombines Into Something Totally New. Urheberrecht - Was genau sind diese Upload-Filter? - Digital.
The World Wide Web Turns 30. Where Does It Go From Here? The state of Apple’s ecosystem lock-in, and where we’re at today. Depth map. In 3D computer graphics a depth map is an image or image channel that contains information relating to the distance of the surfaces of scene objects from a viewpoint.
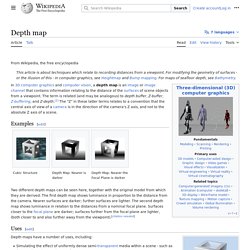
The term is related to and may be analogous to depth buffer, Z-buffer, Z-buffering and Z-depth.[1] The "Z" in these latter terms relates to a convention that the central axis of view of a camera is in the direction of the camera's Z axis, and not to the absolute Z axis of a scene. Examples[edit] Depth Map: Nearer is darker Depth Map: Nearer the Focal Plane is darker Two different depth maps can be seen here, together with the original model from which they are derived.
The first depth map shows luminance in proportion to the distance from the camera. Uses[edit] Shallow depth of field effect.
NATO Group Catfished Soldiers to Prove a Point About Privacy. XR. Cybersecurity Workers Scramble to Fix a Post-Shutdown Mess. German Regulators Just Outlawed Facebook's Whole Ad Business. Identifying, Auditing, and Discussing Third Parties. Urheberrecht und kreatives Schaffen in der digitalen Welt. Was ist und wie funktioniert Webtracking? Tracking ist eine Basistechnologie des Netzes.
Have Phones Become Boring? Well, They’re About to Get Weird. The Pitfalls of Facebook Merging Messenger, Instagram, and WhatsApp Chats. The World’s Fastest Supercomputer Breaks an AI Record. Warning! Everything Is Going Deep: ‘The Age of Surveillance Capitalism’ Missing Link. Facebook, Apple, Google und Co: Das passiert, wenn jemand Ihr Konto hacken will. Together we can thwart the big-tech data grab. Here’s how. Automat (Informatik) Ein Automat oder eine abstrakte Maschine ist in der Informatik, speziell in der Automatentheorie, das Modell eines digitalen, zeitdiskreten Rechners.
Paketdiagramm. Ein Paketdiagramm (engl. package diagram) ist eine der 14 Diagrammarten in der Unified Modeling Language (UML), einer Modellierungssprache für Software und andere Systeme.
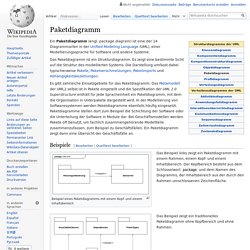
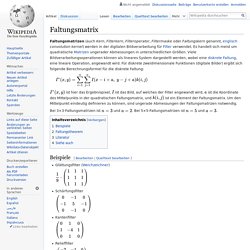
Es gibt zahlreiche Einsatzgebiete für das Paketdiagramm. Das Metamodell der UML2 selbst ist in Pakete eingeteilt und die Spezifikation der UML 2.0 Superstructure enthält für jede Spracheinheit ein Paketdiagramm, mit dem die Organisation in Unterpakete dargestellt wird. Faltungsmatrix. Ist hier das Ergebnispixel, ist das Bild, auf welches der Filter angewandt wird, ist die Koordinate des Mittelpunkts in der quadratischen Faltungsmatrix, und ist ein Element der Faltungsmatrix.
Convolutional Neural Network. Als Begründer der CNNs gilt Yann LeCun. Pixar's Renderman CGI Software Celebrates Its 30th Birthday. VR quotes. Opioids Haven't Solved Chronic Pain. Maybe Virtual Reality Can. What is Virtual Reality (VR)? The Complete WIRED Guide. Fußball: Werder Bremen beobachtet Training in Hoffenheim mit Drohne. The Iran Hacks Cybersecurity Experts Feared May Be Here. Uncanny Valley. 'Hi-tech robot' at Russia forum turns out to be man in suit. A “hi-tech robot” shown on Russian state television has turned out to be a man in a suit. Russia-24 praised the ersatz android during coverage of a youth forum dedicated to robotics, boasting that “Robot Boris has already learned to dance and he’s not that bad”. But sharp-eyed bloggers were dubious. The Russian website TJournal listed questions about the robot’s performance: Where were Boris’s external sensors? AI Experiments. Fehlerkorrekturverfahren. Shannon_entropy.
Why Do Computers Use So Much Energy? Microsoft is currently running an interesting set of hardware experiments. The Spatial Web Will Map Our 3D World—And Change Everything In the Process. Video game development. Process of developing a video game Mainstream commercial PC and console games are generally developed in phases: first, in pre-production, pitches, prototypes, and game design documents are written; if the idea is approved and the developer receives funding, then full-scale development begins.
The development of a complete game usually involves a team of 20–100 individuals with various responsibilities, including designers, artists, programmers, and testers. Overview[edit] Machine Learning Can Create Fake ‘Master Key’ Fingerprints. „Gehirn-Supercomputer“ mit 1 Million Prozessorkernen gestartet. Facebook hack (30 million users) #cuttingedge. Logic bombs YHarari HDp19. The tech giants, the US and the Chinese spy chips that never were… or were they?
On 4 October, Bloomberg Businessweek published a major story under the headline “The Big Hack: How China Used a Tiny Chip to Infiltrate US Companies”. It claimed that Chinese spies had inserted a covert electronic backdoor into the hardware of computer servers used by 30 US companies, including Amazon and Apple (and possibly also servers used by national security agencies), by compromising America’s technology supply chain. What is the internet? 13 key questions answered. What is the internet? The internet is the wider network that allows computer networks around the world run by companies, governments, universities and other organisations to talk to one another. The result is a mass of cables, computers, data centres, routers, servers, repeaters, satellites and wifi towers that allows digital information to travel around the world. It is that infrastructure that lets you order the weekly shop, share your life on Facebook, stream Outcast on Netflix, email your aunt in Wollongong and search the web for the world’s tiniest cat.