

Zero-knowledge proof. In cryptography, a zero-knowledge proof or zero-knowledge protocol is a method by which one party (the prover Peggy) can prove to another party (the verifier Victor) that she knows a value x, without conveying any information apart from the fact that she knows the value x.

Another way of understanding this would be: Interactive zero-knowledge proofs require interaction between the individual (or computer system) proving their knowledge and the individual validating the proof.[1] If proving the statement requires knowledge of some secret information on the part of the prover, the definition implies that the verifier will not be able to prove the statement in turn to anyone else, since the verifier does not possess the secret information. Some forms of non-interactive zero-knowledge proofs exist,[2][3] but the validity of the proof relies on computational assumptions (typically the assumptions of an ideal cryptographic hash function).
Abstract examples[edit] Victor chooses an exit path , and. Preuve à divulgation nulle de connaissance. Une preuve à divulgation nulle de connaissance est une brique de base utilisée en cryptologie dans le cadre de l'authentification et de l'identification.

Cette expression désigne un protocole sécurisé dans lequel une entité nommée « fournisseur de preuve », prouve mathématiquement à une autre entité, le « vérificateur », qu'une proposition est vraie sans toutefois révéler d'autres informations que la véracité de la proposition. Integrity App Terms of Use. THESE TERMS ARE AVAILABLE ON THE COMPANY’S WEBSITE (“SITE”) AND FROM WITHIN THE APPLICATION. 1.
Related terms These Terms must be read in conjunction with the Company's Privacy Policy and, if you are an Admin User, the Terms of Service. We do not use persistent ID cookies on this site. 2. You must be at least 16 years of age to download the Application. 3. The Company hereby grants you a non-exclusive, non-transferable, revocable licence to download the Application to your device ("Device") and to link to Services Place and use the goods and services offered in the Service Places subject to these Terms ("User Licence"). In the event of your breach of the User Licence the Company shall be entitled to terminate the User Licence immediately. You acknowledge that your agreement with your mobile network provider ("Mobile Provider") will apply to your use of the Application. 4.
After you download the app you will be asked to set your identity as a user ("User Profile"). 5. 7. 8. Blockchain / Distributed Ledger Technologie (DLT) Blockchain, gouvernance et énergie ? [EN DIRECT] Discover Integrity. Discover Integrity. Hyperledger. Untitled. ZKProof Standards. Secure Cloud Storage — Privacy Guaranteed. What is Zero-Knowledge Encryption? Trusting personal information to online services makes us vulnerable to abuse.

However, unless you’re an IT professional, it is very hard to understand what “safety” means for each service you use. If you want to make sure that you are truly protecting your private data – you should go for services that use Zero-Knowledge encryption. From this article, you will learn what “Zero Knowledge” is, how Zero-Knowledge encryption works and why we believe this is the best way you can protect your information online. In a nutshell, Zero-Knowledge encryption means that service providers know nothing about the data you store on their servers. But, to better grasp the term, let’s go over how encryption works in general.
A trip to the Zero-Knowledge Hotel Let’s imagine we are on a business trip. Now, let’s put it in context with our online usage: Because of encryption, the locks used by many cloud-based services are so strong that it would take huge computational resources to identify a single key. Cryptography - Zero-Knowledge Proofs. The goal is to prove a statement without leaking extra information, for example, for some N,xN,x, prove xx is a quadratic residue in Z∗N.

Let L⊆Σ∗. Zero Knowledge Proofs and Their Future Applications by Elad Verbin at Web3 Summit 2018. Protocolo de Chaum-Pedersen. El protocolo de Chaum-Pedersen es un algoritmo que permite probar la igualdad del resultado de realizar el logaritmo discreto entre dos parejas de números.
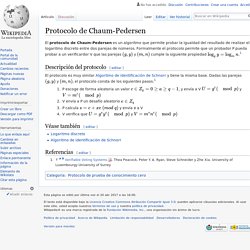
Formalmente el protocolo permite que un probador P pueda probar a un verificardor V que las parejas y. Proof of knowledge. Let be a statement of language in NP, and the set of witnesses for x that should be accepted in the proof.
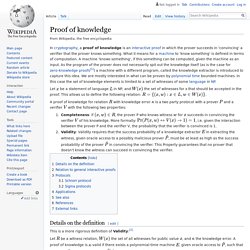
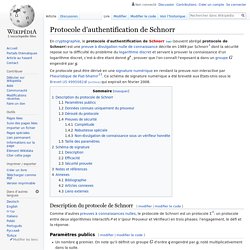
This allows us to define the following relation: Protocole d'authentification de Schnorr. En cryptographie, le protocole d'authentification de Schnorr (en) (souvent abrégé protocole de Schnorr) est une preuve à divulgation nulle de connaissance décrite en 1989 par Schnorr[1] dont la sécurité repose sur la difficulté du problème du logarithme discret et servant à prouver la connaissance d’un logarithme discret, c’est-à-dire étant donné , prouver que l'on connaît l'exposant engendré par.
Untitled. Protocole d'authentification de Schnorr. Zero-Knowledge Proofs & ZCash Simply Explained.