

The pfSense Book. NAXSI RMLL 2012 v1 2. Nbs-system/naxsi-rules. Linux configuration fr v1.2. NoScript - JavaScript/Java/Flash blocker for a safer Firefox experience! - get it! - InformAction. RiskIQ Community Edition. Rayna Stamboliyska : Du Sextoy au "Dark Web" - Thinkerview. About · PiRanhaLysis. Français ci-dessous You have landed on the PiRanhaLysis’s official (and bilingual) website.
Feel free to contact us should you be willing to contribute your content (in writing, voice, etc.). Content should be in either French or English (for additional languages, ask us before you write it all up ;) ). There are currently three main modules built within PiRanhaLysis: PiRogue, a small device meant to ease network interception and analysis; PiPrecious, the network analysis and experiment management platform; PiRanha, a mobile application and IoT network analysis automation tool; Learn more and contribute on our GitHub. Quickstart · EmpireProject/Empire Wiki. Initial Setup Run the .
/setup/install.sh script. This will install the few dependencies and run the . /setup/setup_database.py script. The setup_database.py file contains various setting that you can manually modify, and then initializes the . Running . Main Menu Once you hit the main menu, you'll see the number of active agents, listeners, and loaded modules. The help command should work for all menus, and almost everything that can be tab-completable is (menu commands, agent names, local file paths where relevant, etc.). You can ctrl+C to rage quit at any point. Listeners 101 The first thing you need to do it set up a local listener. The info command will display the currently configured listener options. Set optional and WorkingHours, KillDate, DefaultDelay, and DefaultJitter for the listener, as well as whatever name you want it to be referred to as.
KitPloit - PenTest Tools for your Security Arsenal ☣: Command Line. Online Courses From Top Universities. Join for Free. The Cryptopals Crypto Challenges. pFarb/awesome-crypto-papers: A curated list of cryptography papers, articles, tutorials and howtos. Open Information Security Foundation. Cisco Talos. Metasploit Unleashed - Free Online Ethical Hacking Course. Lessons « n00bpentesting.com. Default Passwords. Nikto2.
Nikto is sponsored by Netsparker, a dead accurate and easy to use web application security solution.
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated. Nikto is not designed as a stealthy tool. It will test a web server in the quickest time possible, and is obvious in log files or to an IPS/IDS. Not every check is a security problem, though most are.
Hacking Éthique : Étude des logiciels malveillants. Dogbert's Blog: BIOS Password Backdoors in Laptops. Synopsis: The mechanics of BIOS password locks present in current generation laptops are briefly outlined.
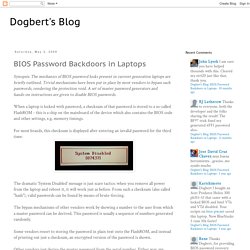
Trivial mechanisms have been put in place by most vendors to bypass such passwords, rendering the protection void. A set of master password generators and hands-on instructions are given to disable BIOS passwords. When a laptop is locked with password, a checksum of that password is stored to a so-called FlashROM - this is a chip on the mainboard of the device which also contains the BIOS code and other settings, e.g. memory timings. The Cyber Incident Tsunami - Time to Get Ready. In advance of Data Privacy & Protection Day, we just released the Cyber Incident & Breach Trends Report (press release here), a look back at the cyber incident trends in 2017 and what can be done to address them.

This report marks the tenth year OTA has provided guidance in this area, and while the specifics have certainly changed over time, the core principles have not. Originally we just looked at the number of reported breaches, but last year we broadened the definition to “cyber incidents,” which includes ransomware infections, business email compromise (BEC), distributed denial-of-service (DDoS) attacks and infiltrations caused by connected devices. This broader definition paints a more realistic picture of the threats and associated impact facing organizations today.
This year we found that the number of cyber incidents nearly doubled to 159,700 globally, and given that most incidents are not reported, this number could easily exceed 350,000. Home · Arachni/arachni-ui-web Wiki. Vulnerabilities (CVE) - Saucs. TorFlow. New attack on WPA/WPA2 using PMKID. In this writeup, I'll describe a new technique to crack WPA PSK (Pre-Shared Key) passwords.
In order to make use of this new attack you need the following tools: This attack was discovered accidentally while looking for new ways to attack the new WPA3 security standard. WPA3 will be much harder to attack because of its modern key establishment protocol called "Simultaneous Authentication of Equals" (SAE).
The main difference from existing attacks is that in this attack, capture of a full EAPOL 4-way handshake is not required. Hébergement E-commerce et sécurité informatique - NBS System. Home · nbs-system/naxsi Wiki. Download. Riverbed is Wireshark's primary sponsor and provides our funding. They also make great products that fully integrate with Wireshark. Créer son hacklab virtuel avec docker. OWASP. Open Web Application Security Project (OWASP) : Portfolio Projects. Maltego User Guide. Tools.kali. Maltego is a unique platform developed to deliver a clear threat picture to the environment that an organization owns and operates.
Maltego’s unique advantage is to demonstrate the complexity and severity of single points of failure as well as trust relationships that exist currently within the scope of your infrastructure. The unique perspective that Maltego offers to both network and resource based entities is the aggregation of information posted all over the internet – whether it’s the current configuration of a router poised on the edge of your network or the current whereabouts of your Vice President on his international visits, Maltego can locate, aggregate and visualize this information.
Maltego offers the user with unprecedented information. Libewf - ForensicsWiki. Libewf is a library to access the Expert Witness Compression Format (EWF).
Servers for Hackers. Security in a Box - Digital security tools and tactics. Home · Arachni/arachni-ui-web Wiki. Robertdavidgraham/masscan. The ZMap Project. Confidentialité et anonymat, pour tout le monde et partout. Kali Linux. A propos du Darkweb. DEFCON - Introversion software. Le manifeste du hacker. Le Manifeste du hacker (titré en anglais The Hacker Manifesto, ou The Conscience of a Hacker, « La Conscience d’un hacker ») est un petit article écrit le 8 janvier 1986, par le hacker Loyd Blankenship après son arrestation, sous le pseudonyme de « The Mentor ».

Publié pour la première fois dans le magazine électronique underground Phrack (Volume 1, Numéro 7, Phile 3 de 10), on peut de nos jours le trouver sur de nombreux sites web. Le Manifeste est considéré comme la pierre angulaire de la contre-culture hacker, et donne un aperçu de la psychologie des premiers hackers. Il affirme que les hackers choisissent cette activité parce que c’est un moyen pour eux d’apprendre, et à cause du sentiment fréquent de frustration causé par leur ennui à l’école. Il exprime aussi l’éveil d’un hacker réalisant son potentiel dans le domaine des ordinateurs.
Un autre s’est fait prendre aujourd’hui, c’est partout dans les journaux. Je suis au collège ou au lycée. J’ai fait une découverte aujourd’hui. Alias.sh. The Tor project. 1981 Chaos Computer Club. Live CD de désinfection. Password Strength Checker. BackTrack Linux.