

How Russian hackers infiltrated the US government for months without being spotted. Thousands of companies and governments are racing to discover whether they have been hit by the Russian hackers who reportedly infiltrated several US government agencies.

The initial breach, reported on December 13, included the Treasury as well as the Departments of Commerce and Homeland Security. But the stealthy techniques the hackers used mean it could take months to identify all their victims and remove whatever spyware they installed. To carry out the breach, the hackers first broke into the systems of SolarWinds, an American software company. How Long It Would Take A Hacker To Guess Your Password, Visualized. The fall of the FBI's most-wanted cybercriminal - The Kernel. On an unseasonably cold Saturday afternoon in March 2012, Jeremy Hammond, one of the most destructive hackers in American history, logged into his computer in his squalid Chicago duplex for the second-to-last time.
His friend Sabu, a notorious hacker who had often encouraged him to attack more ambitious targets, was playfully giving him a hard time over his period offline. “I mean you disappered all day. The NSA Is Running a Satellite Hacking Experiment. Low Earth orbit will soon be awash in small satellites, and the national security community is increasingly concerned about their security.
Researchers at the National Security Agency are using artificial intelligence to characterize strange behaviors in small satellites to understand if they’ve secretly been brought under adversarial control. Old laptop infected with the world's most dangerous malware sells for $1.34 million. You Have 19 Minutes to React If the Russians Hack Your Network.
After Moscow's hackers breach one PC, that network's defenders have less than a half-hour to prevent wider data theft or destruction, a new report finds.
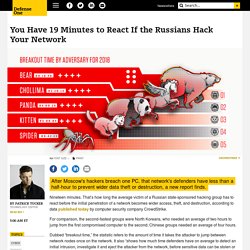
Nineteen minutes. That’s how long the average victim of a Russian state-sponsored hacking group has to react before the initial penetration of a network becomes wider access, theft, and destruction, according to data published today by computer security company CrowdStrike. For comparison, the second-fastest groups were North Koreans, who needed an average of two hours to jump from the first compromised computer to the second; Chinese groups needed an average of four hours.
Nest camera hacked: Hacker spoke to baby, hurled obscenities at couple using Nest camera, dad says. An Illinois couple said a hacker spoke to their baby through one of their Nest security cameras and then later hurled obscenities at them, CBS station WBBM-TV reports.
Arjun Sud told the station he was outside his 7-month-old son's room Sunday outside Chicago and he heard someone talking. "I was shocked to hear a deep, manly voice talking," Sud said. "… My blood ran cold. " Sud told WBBM-TV he thought the voice was coming over the baby monitor by accident. Will Artificial Intelligence Save Us From the Next Cyberattack? Employees at FedEx in the U.S., Telefónica in Spain and the National Health Service in the U.K. opened their work computers one day in May 2017 to find they no longer had access to thousands of crucial documents.
A message appeared demanding payment in bitcoin to have them restored. The ransomware attack known as WannaCry afflicted more than 200,000 people in 150 countries, according to Europol, and was the largest of its kind in recent history. The threat of this sort of crippling data security breach has tech giants turning to artificial intelligence for solutions.
As online hackers increasingly use advanced technology for penetrative attacks, the companies that host our private information also are engaging the most advanced systems available in a bid to protect us. Psy-Ops, Meet Cyber-Ops: U.S. Takes on Russian Trolls. A Russian troll sits down at his desktop and logs into one of the social media accounts he uses to impersonate and radicalize Americans.
Suddenly, a direct message appears: “Hello, Ivan. Inside North Korea’s Hacker Army. In most respects, Jong Hyok looks like any other middle-aged male tech worker you might see on the skyscraper-shadowed streets of Seoul’s Gangnam district: smartphone in hand, dark-blue winter coat over a casual, open-collared work shirt.
Sit him down at a sushi restaurant and start asking him questions, though, and you soon sense that Jong is harboring an extraordinary tale. He slouches, staring intently at the table before him and speaking haltingly, his sentences often trailing away unfinished. Jong tells you he’s in his late 30s, but his tired eyes and wizened skin make him look a decade older. He says he’s concerned that you’ll be indiscreet with details that could expose him or his family. A Simple Design Flaw Makes It Astoundingly Easy To Hack Siri And Alexa. Chinese researchers have discovered a terrifying vulnerability in voice assistants from Apple, Google, Amazon, Microsoft, Samsung, and Huawei.
It affects every iPhone and Macbook running Siri, any Galaxy phone, any PC running Windows 10, and even Amazon’s Alexa assistant. Using a technique called the DolphinAttack, a team from Zhejiang University translated typical vocal commands into ultrasonic frequencies that are too high for the human ear to hear, but perfectly decipherable by the microphones and software powering our always-on voice assistants. This relatively simple translation process lets them take control of gadgets with just a few words uttered in frequencies none of us can hear.
The researchers didn’t just activate basic commands like “Hey Siri” or “Okay Google,” though. They could also tell an iPhone to “call 1234567890” or tell an iPad to FaceTime the number. In other words, Silicon Valley has designed human-friendly UI with a huge security oversight. Pro-Russian Bots Take Up the Right-Wing Cause After Charlottesville. This article has been updated to include a comment provided by Sputnik after this story was published.
Sputnik’s full comment can be found here. Angee Dixson joined Twitter on Aug. 8 and immediately began posting furiously — about 90 times a day. A self-described American Christian conservative, Dixson defended President Donald Trump’s response to the unrest in Charlottesville, criticized the removal of Confederate monuments and posted pictures purporting to show violence by left-wing counterprotesters. Researchers Used Infected DNA to take Full Control of a Computer.
Remember a few month ago when we were all laughing at Harvard scientists for putting a GIF inside a strand of DNA? Now that bridge between technology and the substance that makes up every living organism has taken a much darker turn. Researchers at the University of Washington took control of a machine using a malicious strand of DNA in what is being considered the first “DNA-based exploit of a computer system.”
Malicious software was encoded into short strands of DNA that scientists purchased online. When analyzed, the infected DNA corrupted gene-sequencing software, allowing researchers to take “full control” of the underlying system. U.S. Power Companies Warned ‘Nightmare’ Cyber Weapon Already Causing Blackouts. Seven minutes before midnight last Dec. 17, a bomb of sorts went off in a high-voltage substation north of Kiev. But if you were standing outside the 20 acres of gleaming metal transformers and coils, you wouldn’t have heard a bang or seen a flash.
It wasn’t that kind of bomb. It was a piece of malicious software that had been hiding in a control-room computer miles away, waiting for the right time to reveal itself. At 11:53 p.m., the logic bomb transmitted a staccato burst of pre-programmed commands to the substation, popping one circuit breaker after another until a strip of houses in and around western Kiev were plunged into darkness. How a $10.69 purchase may have sidelined the global malware attack. National Security Administration headquarters in Fort Meade, Md. (Jim Lo Scalzo/European Pressphoto Agency) Russian Expat Founds CrowdStrike to Guard Against Russian Email Hackers - Who Is Dmitri Alperovitch? The government's attitude toward attribution moved closer to Alperovitch's in September 2015, in the run-up to a state visit by Chinese president Xi Jinping. A year earlier, five members of the Chinese People's Liberation Army had been indicted by a grand jury in Pennsylvania for stealing economic secrets from the computers of U.
S. firms in the nuclear, solar, and metals industries. Carlin told me that the indictments were meant as "a giant No Trespass sign: Get off our lawn. " But the indictment didn't stop the hackers. Alperovitch went on television to call for a stronger response. The Russian Expat Leading the Fight to Protect America. Russia DNC Hack - Proof Russia Was Behind the DNC Email Hack. Log In. Guccifer2 Debunks DNC Claim it Was Hacked by Russia. Publishes Huge Tranche of Files Online - The Duran.
Entire database of Trump opposition research stolen from DNC database by Russian hackers. As Russian President Vladmir Putin praised presumptive Republican presidential nominee Donald Trump as “undoubtedly a very colorful, talented person,” Russian spies reportedly hacked into the servers of the Democratic National Committee (DNC) to steal the entire database of opposition research against the controversial candidate. Theconversation. The world is fighting a hidden war thanks to a massive shift in the technologies countries can use to attack each other.
Vuvuzela, a next-generation anonymity tool that protects users by adding NOISE. Cracking bin Laden's computer code: unlikely. It has been reported that Osama bin Laden’s hard drives have been seized, hard drives that could conceivably contain information regarding the membership, funding and future plans of al-Qaeda. Information of this type would help anti-terrorism agencies enormously. Hacker collective Anonymous claims ISIS has plans for more attacks on Sunday. CIA Email Hackers Breach FBI-run Site, Deputy Director's Private Email. Cyber war and the question of causation. Hackers Likely Gained Access To Sensitive Data About Military, Intelligence Personnel. Rep. News from The Associated Press. Feds Say That Banned Researcher Commandeered a Plane. Hackers Steal Up To $1 Billion From Banks. New evidence Sony hack was ‘inside’ job, not North Korea. Who Was Behind the Cyberattack on Sony? Dragos Security - Blog. The Evidence That North Korea Hacked Sony Is Flimsy.
Human biology inspires "unbreakable" encryption. Jeremy Hammond's Sentencing Statement. Stuxnet has infected a Russian nuclear plant and the space station [Updated] Patients' own heartbeat could work as anti-hacking password for implants. Automotive takeover schemes to be detailed at Defcon hacker conference. Hacker Demonstrates Android Smartphone App To Hijack A Plane Midair. Fast-Talking Computer Hacker Just Has To Break Through Encryption Shield Before Uploading Nano-Virus. “I’m Going To Prison For Arithmetic” Andrew Auernheimer aka Weev. Unraveling The Stuxnet Virus. Hacktivism: Civil Disobedience or Cyber Crime? A Box For Manipulating The News On Other People’s Computer Screens.